Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Strictor Ransomware?
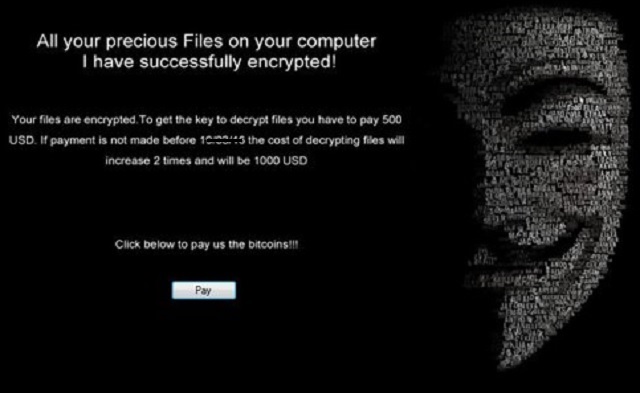
Reader recently start to report the following message being displayed when they boot their computer:
All your precious Files on your computer
I have successfully encrypted!
Your files are encrypted. To get the key to decrypt files you have to pay 500
USD. If payment is not made before … the cost of decrypting files will
increase 2 times and will be 1000 USD
Click below to pay us the bitcoins!!!
Strictor belongs to the vicious ransomware family. Unfortunately, that means you’re now stuck with a particularly destructive type of virus on board. Ransomware is on the rise right now and hackers constantly keep coming up with fresh ideas for infections. How great is that? We’ve already written numerous articles about similar programs – Locky, CryptoJoker, Cerber, etc. They all work the same way and you definitely do not want to cross paths with any of them. Ironically enough, Strictor strictly follows the classic ransomware pattern. You know perfectly well what to expect out of this virus, don’t you? Damage. This is probably among the most virulent infections on the Web so your cyber situation is, to put it mildly, quite troublesome. Do you know how Strictor works? The virus gets activated immediately after installation. On the bright side, you will know that your machine is infected in a heartbeat. Strictor’s silver lining, however, is ending right here. This thing performs a thorough scan on the PC searching for files with specific extensions. For example, it locates pictures, music, Microsoft Office documents, presentations, videos, etc., practically anything of value you may have stored on board. Strictor then uses a highly complicated encrypting algorithm to lock your data. Aggravating, isn’t it? Wait till you hear what happens next. This is only the beginning. A huge percentage of your personal files with various extensions such as .mp3, .mp4, .jpg, .jpeg, .pdf, .ppt, .gif, .txt, .doc, .docx gets encrypted. The ransomware program replaces your original file extension with its own malicious one. As you could imagine, your computer can’t open this new file format so your private data is now inaccessible. You can no longer view or use or work with your very own information, however important it might be. During the encryption process, Strictor also dropped .txt files in every single folder that contains infected data. Judging by the fact how much data gets locked, those are a lot of folders. The virus also adds the same .txt file to your PC desktop just so you could stumble across it on a daily basis. Why are hackers so stubborn in displaying this message? Because it comprises detailed payment instructions. Ransomware is strictly money-oriented; actually, the very reason why it was developed in the first place was to blackmail PC users. The scheme is rather simple – once your data is locked, you’ll be desperately searching for a way to restore it. Many people would give into panic and anxiety seeing such random unauthorized modifications. In this exact moment hackers offer you a deal. After paying a ransom in Bitcoins, you’re supposed to receive a decryption key. This is all really amazing in theory but in practice, you might receive nothing. Making a deal with cyber criminals isn’t the best possible idea, is it? If you’re particularly unlucky, you could end up in a much worse situation than your current one – with your files still unusable, your machine still compromised and a hefty sum of your money gone. Instead of trusting hackers’ empty threats and bogus promises, do the right thing concerning your privacy and your bank account. Get rid of the parasite.
How did I get infected with?
Spam messages from unknown/known senders, spam email-attachments, unreliable third-party advertisements, malicious websites, bundled freeware/shareware – those are just a few of the most popular infiltration methods online. It’s highly recommended that you pay close attention to your machine when you surf the Web. Don’t visit suspicious-looking websites and watch out for infections. It’s much easier to prevent virus installation than to remove a parasite later on so make no mistake. Take your time online; you definitely will not regret it. The ransomware might have also invaded your machine with the help of a sneaky Trojan. To protect your device in the future, stay away from random executables and make sure you remain cautious online. Sometimes a single careless click is more than enough to bring upon you irreversible damage so don’t risk it. Preventing virus infiltration isn’t a challenging task; all you have to do is be more careful.
Why is Strictor dangerous?
Strictor aims for your money. It’s extremely aggressive, virulent and problematic. As mentioned already, the very last thing you should do is follow hackers’ instructions. Simply ignore the ransom note Strictor constantly forces on you and don’t attempt to contact hackers because this will not end well. The virus provides you an email addresses and warns you that unless you play by the rules, you’ll never regain access to your encrypted files. The problem is, cyber criminals aren’t exactly famous for being honorable people. Crooks have no reason whatsoever to give you a decryption key; they a reason to scam you. If you don’t insist on becoming their sponsor, you will make sure you stay away from this cyber fraud. In the future, have a backup of all your important files and protect your machine from ransomware. To delete this infection manually, please follow the comprehensive removal guide that you will find down below.
Strictor Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Strictor Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Strictor encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Strictor encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



