Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Spora Ransomware?
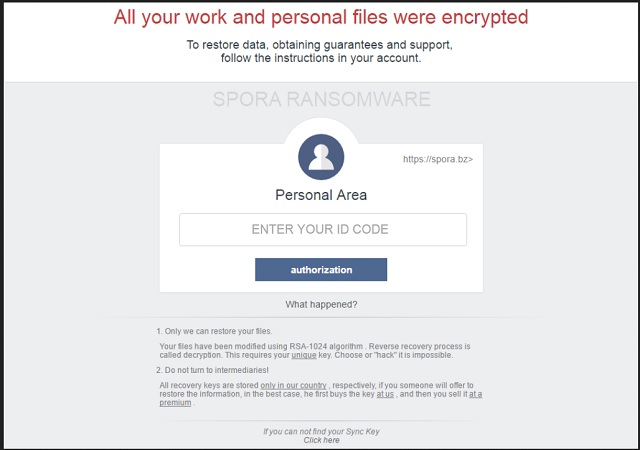
Readers recently started to report the following message being displayed when they boot their computer:
Все Ваши рабочие и личные файлы были зашифрованы
Для восстановления информации, получения гарантий и поддержки,
следуйте инструкции в личном кабинете.
SPORA RANSOMWARE
1. Только мы можем восстановить Ваши файлы.
Ваши файлы были модифицированы при помощи алгоритма RSA-1024. Обратный процесс восстановления называется дешифрование. Для этого необходим Ваш уникальный ключ. Подобрать или “взломать” его невозможно.
2. Не обращайтесь к посредникам!
Все ключи восстановления хранятся только у нас, соответственно, если Вам кто-либо предложит восстановить информацию, в лучшем случае, он сперва купит ключ у нас, затем Вам продаст его с наценкой.
Если Вы не смогли найти Ваш ключ синхронизации
Нажмите здесь
Spora Ransomware is a brand new parasite. It captured researchers’ interest just a couple of days ago but is already wreaking havoc online. To begin with, this is ransomware. The most devastating, cunning and aggressive type of virus. There’s no wonder you’re reading removal guides because this program has to go. Hackers seem to be paying special attention to file-encrypting infections nowadays. Do you know why? Ransomware is probably the most effective way for crooks to blackmail PC users. Instead of taking your money, ransomware tricks you into giving it away voluntarily. This is a very simple yet clever and efficient trickery. Apart from several small details, Spora Ransomware follows the classic ransomware pattern. The virus begins its harassment with a thorough scan of your device. Spora is searching for your files. Unfortunately, it always finds what it’s looking for. We’re talking photos, music, MS Office documents, videos, presentations, anything. Ransomware is famous for modifying a huge variety of formats. All your precious, important, beloved files fall victim to the parasite. Spora successfully locates everything of value stored on your computer. That means, unless you have a backup of your data, things are about to get ugly. Once Spora finds the target data, encryption begins. This infection uses the complicated RSA-1024 and AES cryptography. As a result, it locks every single bit of information on your PC system. Yes, that involves your favorite pictures and work-related documents. Ransomware is striking where hackers know it would hurt the most. It goes without saying most people would desperately want their files back. However, this is how they get involved in a scam. Spora Ransomware doesn’t rename the files it encrypts. We don’t see many ransomware programs that apply this technique. In addition, the virus is able to work even with no Internet connection (offline). While encrypting your information, Spora creates payment-instructions. You will notice a .html and a .KEY file in every folder that contains locked data. Your desktop wallpaper may get changed too. The ransom messages are written in both Russian and English and contain a link to Spora’s website. Another quite unique trait is the fact this page contains lots of information. It provides you details about the encryption cipher, ransom and decryption key. The deal is very straightforward – you receive a decryptor if you pay. To put it mildly, making a bargain with cyber criminals wouldn’t be your brightest idea.
How did I get infected with?
Spora Ransomware travels the Web via a corrupted email. Said email is in Russian and looks like a typical accounting report. This email wasn’t sent from your manager, though. It was sent by greedy cyber criminals who are trying to let Spora loose. In there you will find a malicious .hta file which must NOT be executed. If it does, voila. The ransomware gets installed on your PC and immediately starts its shenanigans. To protect your safety in the future, stay away from questionable emails. Same thing goes for suspicious-looking messages in social media. We recommend deleting any email/message from unknown senders. Spam messages could be posing a giant threat to your security so be careful. You only need one single negligent click to download a vicious infection. Now that you know how problematic ransomware is, are you willing to deal with it ever again? Put your safety first and don’t take unnecessary risks. Also, stay away from unverified websites, random program updates, torrents and pop-up ads. You won’t regret it.
Why is Spora dangerous?
Spora Ransomware encrypts your information. It modifies your files and holds them hostage. Then hackers start playing mind games with you in attempts to steal your money. As mentioned already, Spora provides detailed payment instructions. According to these ransom notes, you must give away a certain sum of Bitcoins. For those of you unfamiliar with Bitcoins, that’s a very popular online currency. Depending on what you want to receive from hackers, the sum varies. Freeing your locked information would cost you up to 280 USD. Victims could choose to just get immunity or remove the ransomware in which cases the sum is about 80 USD. In no scenario imaginable should you pay a single cent to crooks. Paying their ransom guarantees you absolutely nothing. Keep in mind that Spora will cause you irreversible damage if you allow it. To delete this pest manually, please follow our removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.

Spora Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Ransomware Startup Location
STEP 4: Recover Spora Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Spora encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Spora encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



