Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Scylex just keeps popping up and you cannot remove it?
Trojans are, in a way, the backbone of Internet viruses. They’ve been around for a while and have continuously plagued web users. Trojans are nasty cyber threats. They’re a menace not just to your system, but also to your privacy. They target both your and your system’s well-being. And, unless you act against the infection ASAP, it may succeed in its malicious agenda. And, since Trojans have been roaming the web for so long, it’s no surprise that new one pop up daily. Now, cyber crooks have come up with a new name for an old product. The Scylex Trojan has been plaguing web users recently. It’s one of the newest threats online, and it’s quite the nuisance. Despite the tool’s new name, it’s still programmed to act like any old Trojan. So, it displays all the common characteristics you find n these infections. It sneaks into your PC undetected by preying on your carelessness. It promptly begins its mess-making. And, continues until it’s no longer residing on your computer. That’s right. Scylex WILL wreak havoc for as long as you let it. So, here’s some advice: don’t let it! As soon as you become aware of the infection’s existence, take action! Do something to prevent it from making a gigantic mess, and placing your private life on the line. Don’t just idly stand by as it bombards you with issues and grievances. Avoid the unpleasantness. Spare yourself the headaches. Find the infection’s hiding spot at once! And, when you do, delete it. The sooner, the better.

How did I get infected with?
As was already mentioned, Scylex sneaks in undetected. It employs the old but gold means of infiltration. And, it slithers into your system without you even realizing it. Now, that may sound a bit surprising, considering it requires your approval to enter. Yes, Trojans have to gain your permission to install themselves. If they don’t get it, they cannot invade your system. They’re bound to ask for it. So, how do you suppose that exchange goes down? How do you imagine you give the green light to such a threat? Well, it’s pretty simple. Yes, the tool has to seek your consent. But it doesn’t have to do it openly. Instead, it turns to every known trick in the book to dupe you into saying that coveted ‘Yes.’ For example, it can hitch a ride with spam email attachments. Or, hide behind freeware, corrupted links, or sites. It can even pretend to be a fake update, like Adobe Flash Player or Java. As you can see, each method of infiltration cannot prove successful if you are attentive. If you don’t rush and do your due diligence, you can spot the Trojan trying to invade your PC. And, prevent its invasion. So, be more vigilant. Do your due diligence. Your caution can save you a ton of troubles and headaches.
Why is this dangerous?
Scylex is a hazardous cyber threat. Once it slithers its way in and settles into your system, brace yourself. You’re in for a pretty bad time. Scylex is a specific type of Trojan. It belongs to the category of Banking Trojans. And, as you can probably already tell, that’s not a good thing. That type of tool is an utter menace. Its developers have programmed it to spy on you in an attempt to steal your private information. They aim to get a hold of your personal and financial details. And, the end-game is profit. Unsurprisingly, these unknown third parties want your money. The espionage begins shortly after infiltration. Scylex starts to keep track of your browsing activities as soon as it settles. And, it not only monitors your online habits but also catalogs them. It keeps a thorough record of your every move. And, once it deems it has gathered enough data, it sends it to the unknown individuals behind it. Think about it. Strangers with questionable intentions, to say the least, with access to your private life. Ask yourself if that’s something you’re willing to accept.
Manual Scylex Removal Instructions
STEP 2: Windows 7/XP/Vista Removal
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking in Windows 8
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
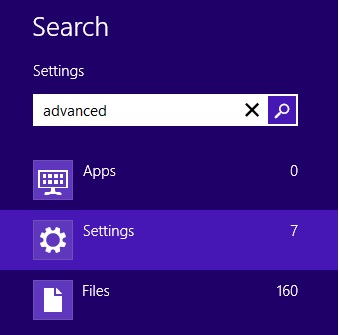
- select Settings
- in the search box type Advanced
- On the left the following should appear
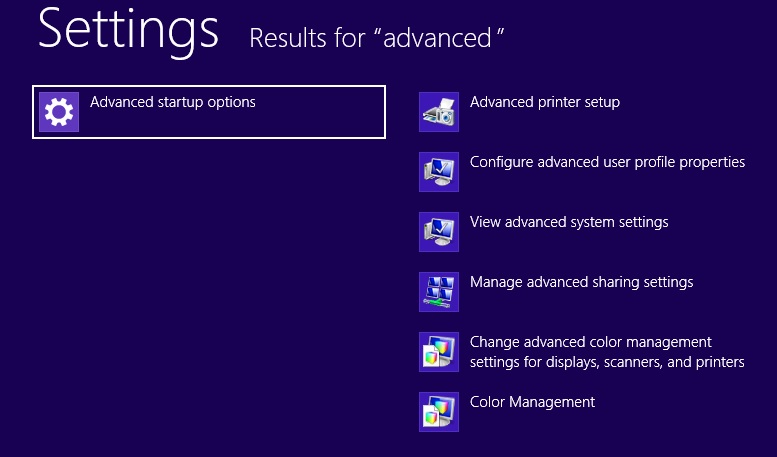
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
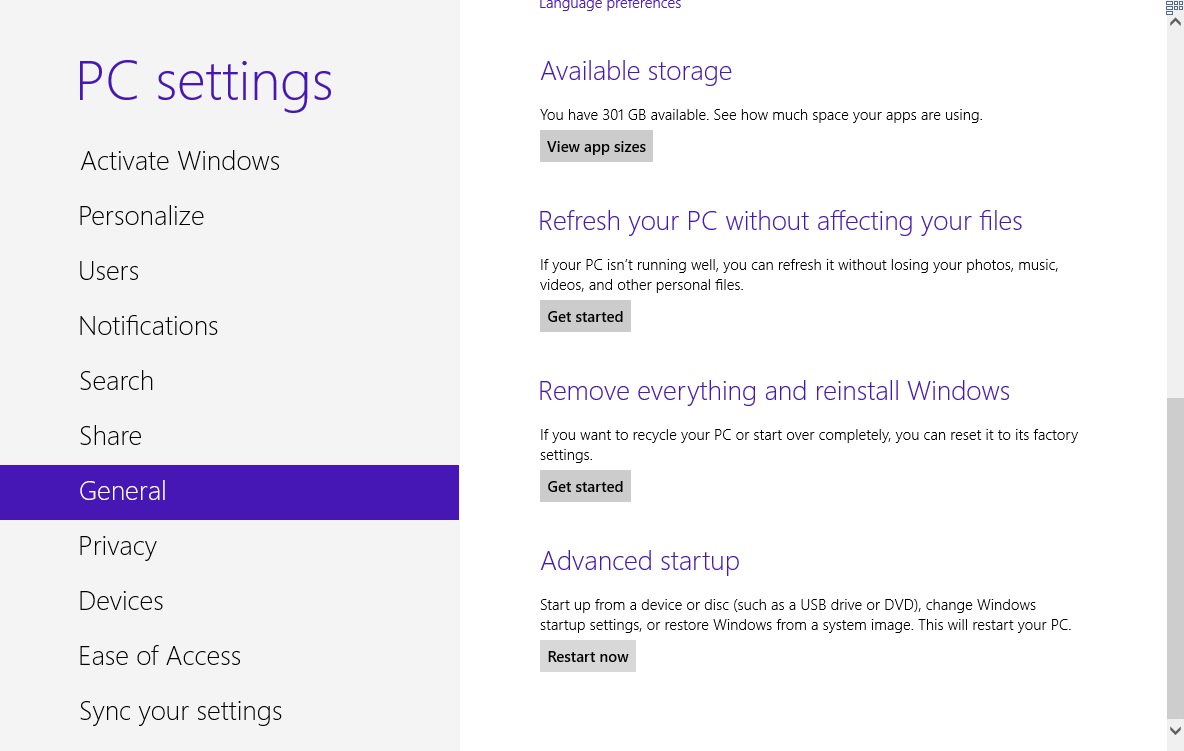
- Click on Troubleshoot
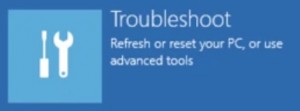
- Then Advanced options

- Then Startup settings

- Then Restart
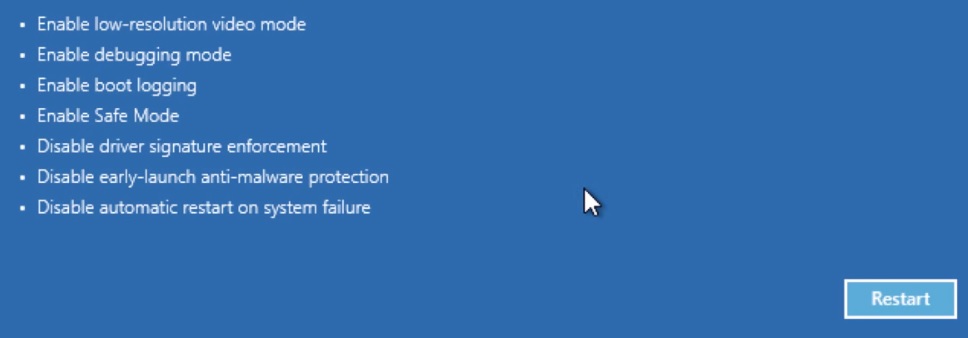
- When you see this screen press F5 – Enable Safe Mode with Networking

STEP 2: Start Your Computer into Safe Mode with Networking in Windows 7/XP/Vista
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

STEP 3: Locate the startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
%LocalAppData%\uqgtmedia
where %LocalAppData% refers to:
C:\Users\{username}\AppData\Local
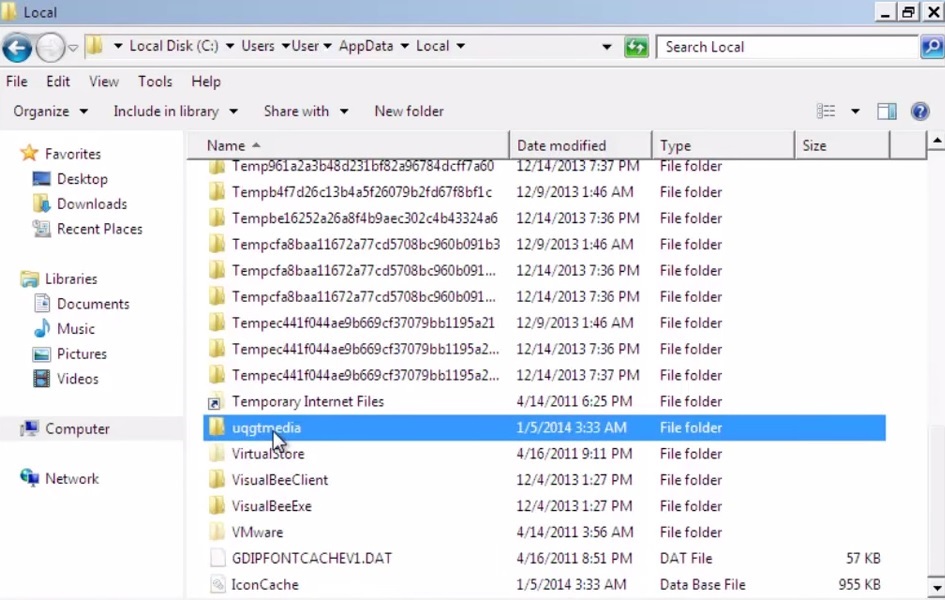
- delete the whole folder
Double check with any antimalware program for any leftovers. Keep your software up-to date.



