Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
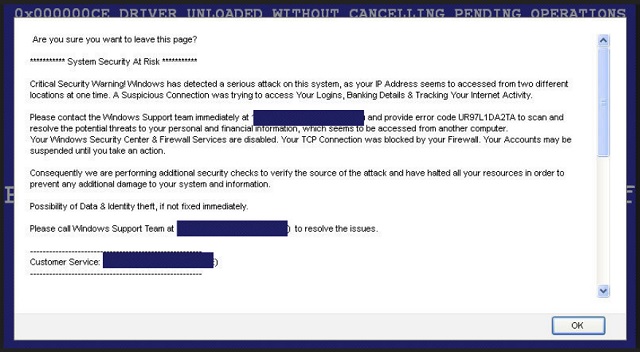
Can’t Remove A Suspicious Connection Was Trying to Access Your Logins pop-ups?
If you are suddenly bombarded with an endless array of pop-up messages, claiming ‘A Suspicious Connection Was Trying to Access Your Logins,’ you are in trouble. The message’s appearance is clearly indicative of the presence of malware. Oh, yes. There is a malicious cyber threat, residing somewhere in the corners of your PC, and it will throw you into a world of trouble if you don’t take preemptive measures against it. Right from the top you must understand that the more time you allow the infection to spend on your computer, the more opportunities it has to mess everything up. Don’t let it! Don’t stand by as it wreaks havoc! Locate where exactly its hiding spot is, and when you do – get rid of it. If you choose not to or delay its deletion, you better brace yourself for a pretty unpleasant experience. In the case of the ‘A Suspicious Connection Was Trying to Access Your Logins’ pop-up, you’re dealing with the type of infection come to be known as ‘scareware.’ As the name lets out, the dreaded tool uses scare tactics to frighten you into a panic frenzy and take advantage of you. The message, shared above will be thrown your way incessantly, and it won’t be alone. It will be accompanied by many others, equally or even more frightening. The nasty tool will try to make you believe your system is under threat of Trojans, adware, hijackers, ransomware and, pretty much, every other cyber infection, roaming the web. Supposedly, if you don’t call the helpline, which the malware behind the message so thoughtfully provides, and ask for assistance in dealing with these problems, terrible things will happen to your system! Don’t buy it. It’s all lies. And, as for the number given, don’t ever call it! You’d do best NOT to trust anything, which the tool shows you. The ‘A Suspicious Connection Was Trying to Access Your Logins’ pop-up is but the first of many such invasive and disruptive annoyances, which the malware behind it will bombard you with – ads, redirects, sponsored links, etc. Not to mention, the security risk it will place upon you. Do yourself a favor, and don’t let it run rampant on your system, and make a mess. Find its hiding place, and delete it as soon as the opportunity presents itself. You won’t regret it.
How did I get infected with?
Such dangerous and damaging tools don’t just show up on your computer one day, out of the blue. Oh, no. They require your permission to enter. And, they’re bound to ask for it. That’s right. For such a nasty program to invade your system, you have to allow it. That means, at some point, the malicious application, you’re currently stuck with, which is ruining your browsing and threatening your privacy, asked you for permission, and you granted it! Wrap your head around that. You may not remember doing it, but you did. You agreed to install malware on your computer. And, do you know why? Carelessness. Infections prey on it. They rely on your distraction, naivety, and haste and use them to their advantage. By exploiting your gullibility and carelessness, they fool you into permitting them in, without you even realizing it. But how exactly do they manage that? Well, they tend to slither in undetected via slyness and subtlety, and the assistance of the old but gold methods of infiltration. They often pretend to be bogus updates, like Java or Adobe Flash Player, or hitch a ride with corrupted links or sites, spam email attachments or freeware. If you wish to keep such nasty cyber threats away from your PC, be more thorough and vigilant! Even a little extra attention goes a long, long way, and can save you a ton of grievances. Remember that next time you’re debating whether to skip reading the terms and conditions or just agree to everything and hope for the best. If you go with the latter, don’t be surprised if one day you’re greeted with the ‘A Suspicious Connection Was Trying to Access Your Logins’ pop-up.
Why are these ads dangerous?
The people behind the ‘A Suspicious Connection Was Trying to Access Your Logins’ pop-up are fear mongers. They employ scare tactics and hope you’ll fall for their deceptive, made-up claims and panic, and, in your panicked state, will do what they ask of you. Don’t make the mistake of trusting these people! They’re malicious and only seek to exploit you for monetary gain. They throw fake statements your ways, trying to frighten you into doing something, which you’ll later regret. So, don’t believe them! Ignore their endless stream of bogus pop-ups, which may prove to be quite a difficult feat since they’ll appear incessantly. Unsurprisingly, because of the constant disruptions, which the malware behind the fake, frightful claims, will put you through, you’ll begin to experience many more frustrations. Like, a slower computer performance, as well as frequent system crashes. But as interruptive and obnoxious as these issues may be, they pale in comparison to the security threat you’ll face. The pesky program, plaguing your PC, is designed to spy on you from the moment it slithers its way in and keep track of your browsing. But it doesn’t just monitor your online activities. It thoroughly catalogs them. And, once it determines it has gathered enough data, it sends it to the third parties that published it. That means strangers will have access to your personal and financial information. The question is, are you going to let that happen? Think long and hard before you reply as both your and your system’s well-being rely on your response.
How Can I Remove A Suspicious Connection Was Trying to Access Your Logins Pop-ups?
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
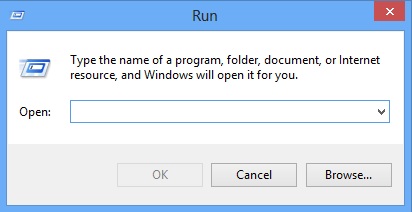
Type “Appwiz.cpl”
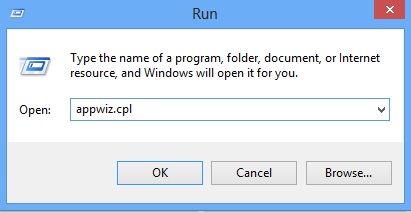
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
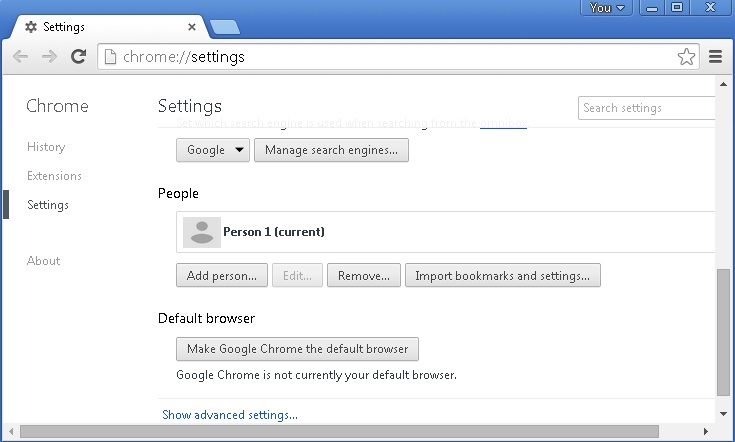
- choose a preferred name.
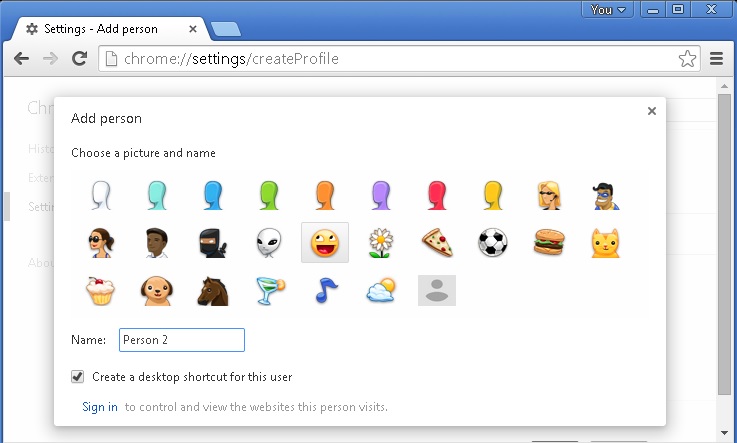
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
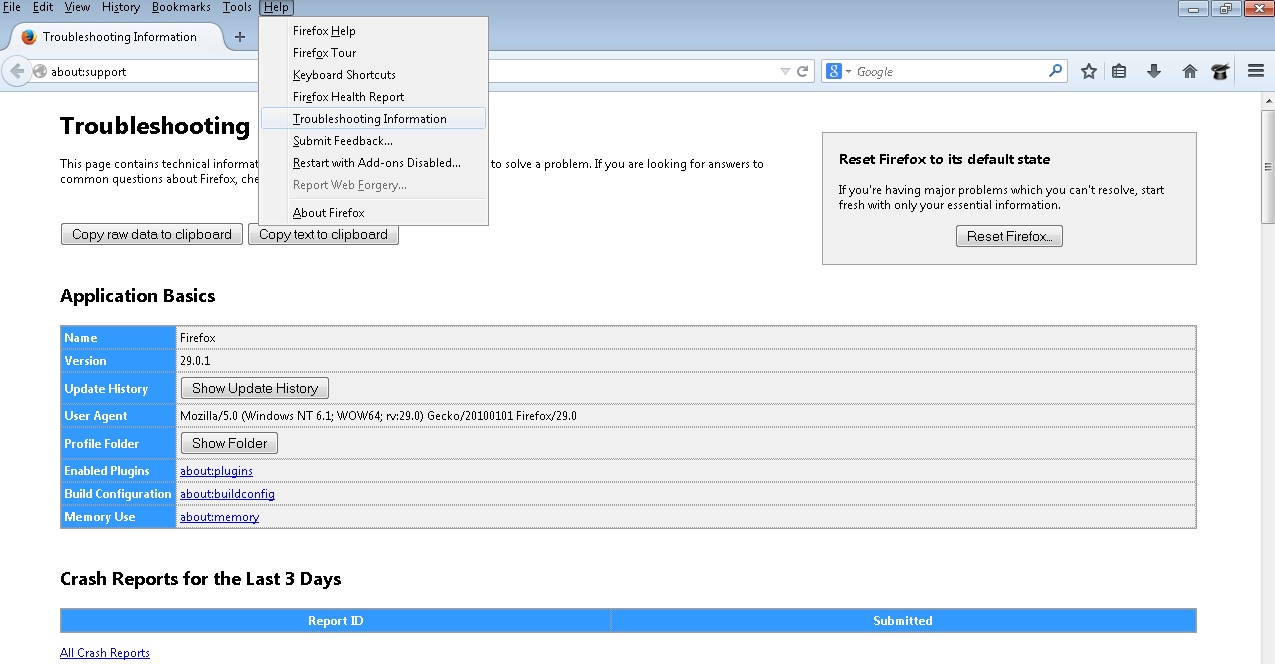
- Open the Firefox’s Help Menu
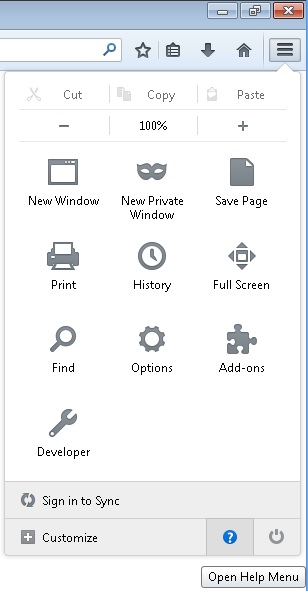
- Then Troubleshoot information
- Click on Reset Firefox
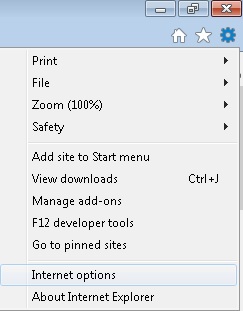
Remove from Internet Explorer
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
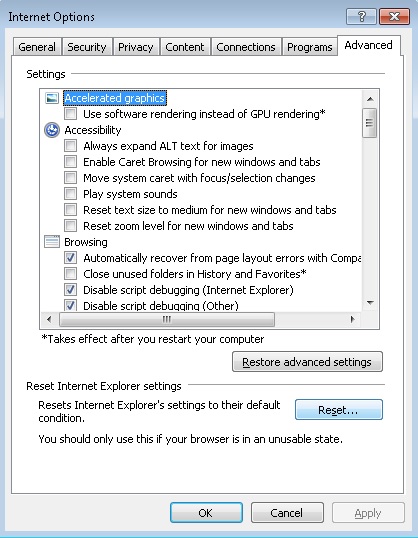
- Click on Internet options
- Select the Advanced tab and click on Reset.
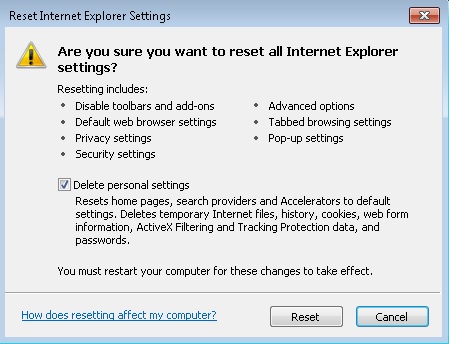
- Check the “Delete Personal Settings Tab” and then Reset
- Close IE
Permanently Remove A Suspicious Connection Was Trying to Access Your Logins Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.