Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RoshaLock Ransomware?
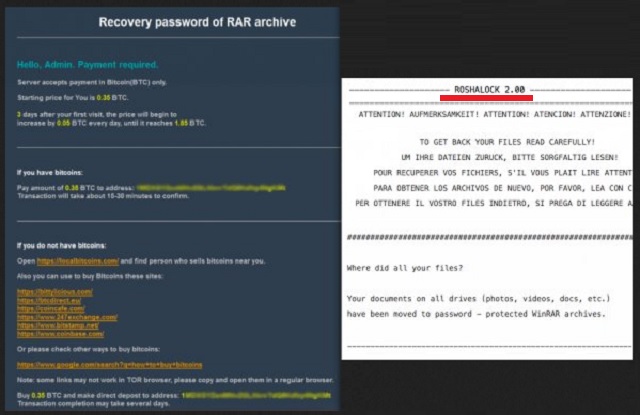
Readers recently started to report the following message being displayed when they boot their computer:
ATTENTION! AUFMERKSAMKEIT! ATTENTION! ATENCIÓN! ATTENZIONE!
TO GET BACK YOUR FILES READ CAREFULLY!
RoshaLock is the newest member of the ransomware family. The program seems to be the All your documents ransomware under the guise of a new face. It’s the same threat but with a revamped look. Although, you could arguably get away with saying that for all ransomware infections. They tend to operate in the same manner. The infection creeps into your system via deceitful and sneaky methods. Once in, it takes over completely. And, here’s where RoshaLock stands out a bit. It doesn’t use an encryption algorithm to lock your files with an extension. Instead, it goes a different way. The tool gathers the targeted data, and places it in archives. It creates two, one for each drive. The archive are, of course, password-protected. If you’re wondering which files get targeted, the answer is a lot of them. There have been estimates that the ransomware takes aim at 2634 various file types. Odds are, your pictures, music, documents, videos, everything falls under RoshaLock. You won’t find much that’s not locked in the archives. They bear the name All_Your_Documents.rar. And, are located in the folder [Drive letter]:\All_Your_Documents\All_Your_Documents.rar. If you don’t remember such a folder, it’s because the ransomware created it for that sole purpose. To contain the locked archives. Once it gathers and locks your data, the tool leaves a ransom note. It’s a TXT file, called All Your Files in Archive! And, it’s rather standard as ransom notes go. The twist is, it’s in five languages – German, Italian, French, Spanish, and English. It explains your predicament, and gives you specific instruction on what to do next. If you follow them, it claims you’ll regain control of your data. If not, you lose everything. It’s scare tactics, and it tends to work like a charm. To make sure you’re scared enough, adds an extra incentive. Every day you delay payment, the requested amount increases by 0.5 Bitcoin. And, that’s a substantial increase. 1 Bitcoin equals about $600. RoshaLock gives you three days to ponder your predicament. Then, on the fourth, the increases begin to kick in. The ransomware promises to send you the needed password after it receives payment. But don’t get your hopes up. There are so many ways the exchange can go wrong. After all, you’re placing your faith on cyber extortionists. Don’t expect any miracles. As much as you won’t like it, the best course of action you can take is to forsake your files. Don’t contact the kidnappers. Don’t send them money. Losing files is preferable to losing something more precious. Like, your personal and financial information. And, if you pay, you’re putting it on the line. So, don’t.
How did I get infected with?
RoshaLock uses the usual methods of invasion to gain access to your system. It turns to freeware, corrupted links, spam email attachments. The old but gold means of infiltration. The tool can also pretend to be a bogus system or program update. Like, Java. You can believe you’re updating your Java, but you’re wrong. In reality, that’s a ransomware in disguise. If you wish to avoid getting stuck with such a dreaded infection, be wary. Always do your due diligence when installing tools or updates. Remember to always read the terms and conditions. It’s crucial for maintaining an infection-free PC. Carelessness leads to cyber threats. Vigilance helps to keep them away. Choose caution over distraction, naivety, and haste. Sometimes even a little extra attention goes a long way.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Why is RoshaLock dangerous?
Do NOT make the mistake for believing RoshaLock’s lies! Don’t fall for its deceptive promises. If you pay the ransom it requests, that doesn’t make your problem go away as if by magic. They’re still there! What happens after you pay? Let’s examine the possible scenarios. You comply, and transfer the sum, RoshaLock demanded. Then what do you think happens? The tool stated that it sends you the password for unlocking its archives. But what if it doesn’t? What if it sends nothing? Or, what if it sends the wrong one? Even if it sends the right one, and it works, you’re still in a bad place. The password only unlocks the archives that keep your data. It doesn’t magically remove the infection. It’s still there. The RoshaLock ransomware remains. It lurks somewhere on your computer, ready to strike again. But uncertainty is not the biggest part of why you must NOT pay. You mustn’t pay because, by doing so, you expose your private life. Think about it. When you transfer the money, you provide your personal and financial information. You give these cyber criminals access to it. And, that’s something, you never want to do. Protect your privacy. Discard your data. It’s the lesser of two evils.
RoshaLock Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover RoshaLock Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with RoshaLock encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate RoshaLock encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



