Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zyklon Locker Ransomware?
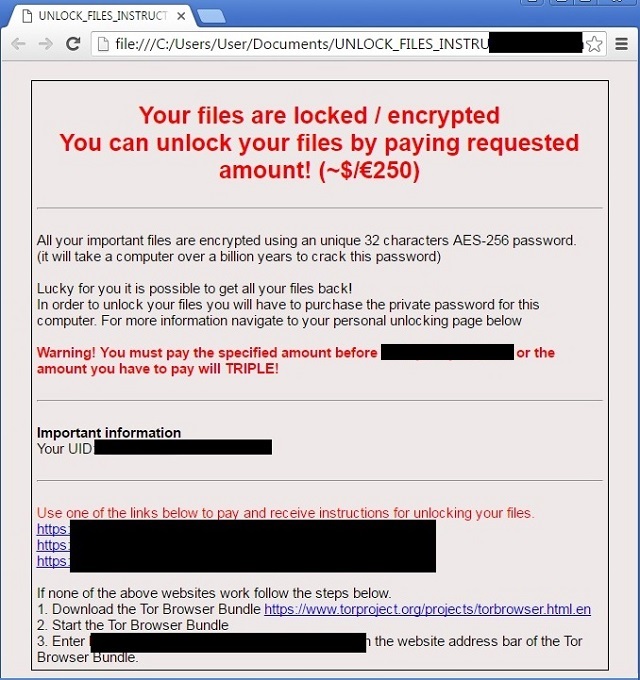
Reader recently start to report the following message being displayed when they boot their computer:
Your files are locked / encrypted
You can unlock your files by paying requested
amount! (~$/€ 250)
All your important files are encrypted using an unique 32 characters AES-256 password.
Lucky for you it is possible to get all your files back!
In order to unlock your files you will have to purchase the private password for this computer. For more information navigate to your personal unlocking page below.
Warning! You must pay the specified amount before … or the amount you have to pay will TRIPLE!
Zyklon Locker is part of the most unpleasant family of infections – ransomware. This type of cyber threat is notoriously invasive and harmful as it’s designed to slither in undetected and target your data. Yes, once the malicious tool finds its way into your system, its array of disaster begins with encryption. Zyklon Locker encrypts every single file you have stored on your computer and holds it hostage for monetary payment. It’s a simple, but quite lucrative, scheme as most users are willing to do everything they can to get their files back. Now, make no mistake. The ransomware doesn’t relocate or delete your data. Oh, no. It merely makes it so you cannot access them in any way. It uses the AES CBC 256-bit encryption algorithm and locks your files by adding either the .locked or .zyklon extension. And, then you cannot open a single file. Renaming them won’t do the trick, as well. The only way to free your files from the tool’s captivity is to meet its demands and do what it wants. And, what it requests from you is to pay up. Once the encryption has been completed, Zyklon Locker makes sure you become aware of its requirements by displaying them on your screen. Plus, it adds files, containing both the demands, as well as instructions for payment in each of your folders. It leaves no chances – the tool wants you to know what you must do if you wish to take back your files. But, here’s what you should understand. Even if the ransomware asks you to transfer one dollar (which it doesn’t, it’s more), you must NOT do it! Don’t forget these are unknown individuals with questionable intentions and, most likely, wicked agendas. They cannot be trusted! They designed a malicious infection and released onto the web, where it found its way to your system, and then proceeded to corrupt it. These strangers encrypted your data and held it for ransom. Do you honestly believe they are trustworthy enough to keep their end of the bargain? Don’t be naive. As difficult as it may be, make the wiser choice. Disregard your data in favor of your privacy and your system’s well-being. Don’t pay these people. It’s not worth the risk.
How did I get infected with?
Ransomware doesn’t just appear out of the blue, and neither does Zyklon Locker. For such a tool to enter your system, you were involved. In fact, it’s more than probable that you invited it in, held the door open for it as it paraded through, and didn’t even know it. How come? Well, it’s pretty straightforward. You were duped. The nasty infection fooled you into allowing it into your system via slyness and subtlety. It turned to every known trick in the book so as to deceive you into giving it the green light. But its most commonly used means of infiltration is by far through emails. It uses spam emails, and attaches itself to the content, hoping you’ll be careless enough to allow it into your PC. The infection often masks itself as an official letter from a legitimate company, like DHL or FedEx, but don’t buy it. As you might have guessed already, it’s utterly bogus. Ignore the logos and signs, which are crafted to further convince you of the email’s ‘authenticity,’ and which, sadly, usually do the trick. If you wish to keep ransomware such as Zyklon Locker away from your computer, be more careful! Always be more thorough and vigilant. Don’t rush and don’t give into distraction and gullibility. Take every email from an unknown sender with a grain of salt, and even double-check the ones from known senders! Better safe than sorry.
Why is Zyklon Locker dangerous?
Zyklon Locker is a plague on your system. It’s an utter menace. As was already explained, once it makes its way into your computer, it begins its encryption process to lock your data. It attacks every single one of your files. Nothing is safe from its reach. So, when it’s done, you’ll find every picture, video, document, music file, everything, encrypted. For example, if you had a video, called ‘amazing,’ you’ll suddenly see it as either ‘amazing.locked’ or ‘amazing.zyklon.’ And, do you know what? As much as you try to access these files by renaming them, it won’t work. Once it takes your data hostage, the tool displays a message on your screen, which states that the one and only way to take back everything, is to pay a ransom. It usually amounts to 0.6 BTC (Bitcoins) or approximately 250 USD. And, since the ransomware doesn’t want to waste time waiting, it gives you a deadline. If you delay the payment and pass the data it has set, the ransom amount is said to be tripled. But if you wish to decrypt your files with the proper key, you have to pay up. Zyklon Locker doesn’t give you a choice. Supposedly, when you complete the payment, you’ll receive a decryption key, and when you apply it – voila! You get your data back. No more encryption. That sounds great, but there are so many questions you need to ask yourself before you make any decision. What if the Zyklon Locker tool double-crosses me? After all, it is a cyber infection, designed to exploit you. What if it does go through with its end of the deal and does provide me with a decryption key, but it doesn’t work? What if it works and I regain my files, but the nasty ransomware’s programming kicks back in the next day, and I find myself forced back to square one? Those are all valid questions you need to address before deciding how to act. And, they don’t even exhaust all of the possibilities, which you might face. Not to mention that if you do choose to pay the ransom, you’ll be giving access to your private details to these people, which opens a whole other door of disaster. Are you prepared for the tremendous amount of risks of allowing strangers with malicious intentions into your private life? Don’t gamble with your privacy! Your pictures and music aren’t worth as much as your personal and financial information. Choose privacy over data.
Zyklon Locker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zyklon Locker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zyklon Locker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zyklon Locker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



