Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zuahahhah Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
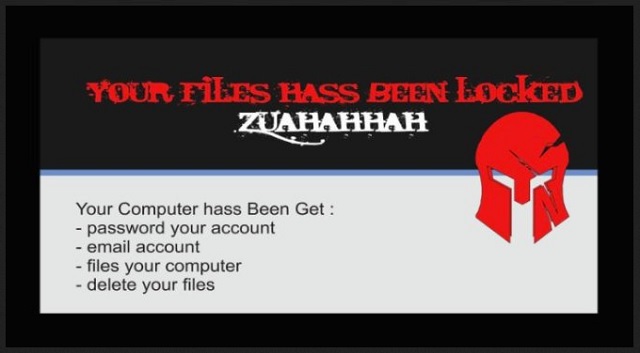
YOUR FILES HAS BEEN LOCKED
ZUAHAHHAH
Your Computer has been Get:
– password your account
– email account
– files your computer
– delete your files
Ransomware viruses are the most dreaded computer infections nowadays. There is a good reason for that. These parasites are fatal. They will not destroy your computer. They are far worse. They aim at your data. Your work and memories are gone in a split-second. That is what the Zuahahhah Ransomware pretends to be doing. It targets user generated files such as your pictures, documents, archives, and databases. The ransomware locks your files successfully. Yet, just like its previous variants the Crypt888 Ransomware and the Aviso Ransomware, Zuahahhah is decryptable. You are incredibly lucky. You can restore your files. So, breathe. Your files are not gone. Not yet. The Zuahahhah ransomware is still under development. You should not leave it to chance. Remove the infection immediately. Otherwise, it may evolve into full-fledged ransomware. Even in its current state, Zuahahhah can penetrate your system on an advanced level. It has full access to your HDD and can make changes to your system. This parasite can add and remove entries from your system’s registry. Judging by its ransom note, this parasite is more than a typical ransomware. It is probably a spying virus as well. Even though it is not written by native speakers, the ransom note is clear. The crooks have access to your username, password, email account. Security researchers have confirmed that the ransomware can connect to its Command and Control (C&C) server. This means that the hackers can easily transfer data via this virus. Do not wait to see what will happen to your files. Take action against the ransomware now!
How did I get infected with?
Zuahahhah is mainly distributed via spam email attachments. The hackers attach corrupted files. When you open these files, they execute malicious code which downloads the payload file of the ransomware. Everything else proceeds quite typically for a ransomware infection. Once the virus is installed, it scans your HDD and encrypts all target files. Only then will it replace your desktop’s background with its ransom note. Unfortunately, the spam emails are not the only virus distribution method. Torrents, fake software updates and freeware bundles are also quite commonly used nowadays. The key to a secure and infection free computer is caution. Always keep your guard up. Whenever you are installing a program, opt for advanced setup option. Only under the advanced installation can you see whether there are additional programs about to be installed. In case there are, examine them carefully. Do not rush. More often than not, these extras are malicious. Read the terms and conditions. Make sure you understand what you are approving on your computer. Your vigilance can keep your device clean. The Zuahahhah ransomware wouldn’t have infected your machine if you were a bit more diligent. Yet, what’s done is done. Learn your lessons. It is also a good idea to back up your files. Do it regularly. This way, you will be prepared if a ransomware attacks you again.
Why is Zuahahhah dangerous?
Zuahahhah Ransomware is quite dangerous. Even though its encryption is breakable, the virus still has managed to infect your machine. What is even more worrisome is the fact that the virus communicates with its developers. There is evidence that the hackers are still developing the infection. If they succeed, they can update the virus you are infected with. Do not test their skills. Besides. It is not just your files that are at risk. Zuahahhah can steal sensitive information. Can you imagine what may happen if the crooks get in possession of your IP and email addresses, credit card and bank account details? With the ransomware installed on your system, you cannot use your PC freely. Otherwise, you risk your data The virus may also delete information stored on your PC. This piece of software has no place on your machine. It is a hole in your security wall and should be removed upon discovery. We recommend you to use an automated solution. Zuahahhah Ransomware is quite a complicated virus. So is its removal. Therefore, it is in your best interest to invest in a trustworthy anti-virus program.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Zuahahhah Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zuahahhah Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zuahahhah encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zuahahhah encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



