Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zayka Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
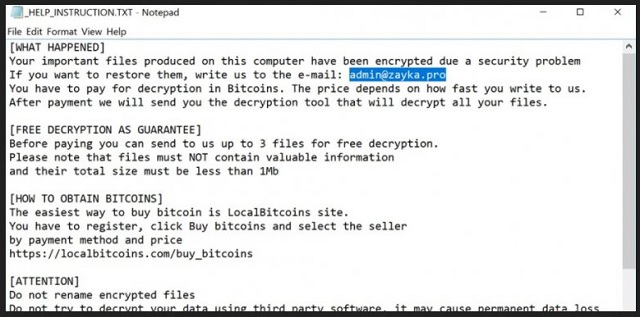
[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem If you want to restore them, write us to the e-mail: admin@zayka.pro
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption. Please note that files must NOT contain valuable information, and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site. You have to register, click Buy bitcoins and select the seller by payment method and price hxxps://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files Do not try to decrypt your data using third party software, it may cause permanent data loss
NOOB
Zayka Ransomware is one of many file-encrypting viruses. Researchers have established this is a new variant of the infamous CryptoMix Ransomware. Zayka is also associated with Noob Ransomware. If you end up stuck with this infection, know you’re in for trouble. File-encrypting viruses are notoriously dreaded, super aggressive and very dangerous. Don’t waste any time and, furthermore, don’t pay hackers anything. Zayka Ransomware uses a complicated encrypting cipher to lock your files. It firstly scans your computer and locates all your personal information. That includes a huge variety of formats which is a recipe for disaster. Ransomware targets all your photos, documents, videos, music files. As you could imagine, the virus might damage some precious, irreplaceable data. We’d recommend that you keep backup copies of your important information. Do not overlook the threat ransomware infections pose. There are plenty of programs like Zayka out there so you could get infected again. Do not make the same mistake twice and protect your files. Zayka Ransomware renames them. It adds the .Zayka extension which indicates the encryption is over. Your favorite files are now unusable and unrecognizable to your PC. As a result, the machine won’t be able to open any of them. Hackers are holding your data hostage and then try to fool you into buying a certain decryptor. The problem is that you may pay the entire ransom right away and still remain unable to free your files. You have been involved in a nasty attempt for a fraud so don’t believe anything hackers promise. They aren’t famous for playing by the rules anyway. Instead of falling right into the trap, remove the ransomware. The Zayka virus drops ransom notes (_HELP_INSTRUCTION.txt files) as soon as it locks your data. You will find these messages in all folders that contain encrypted files. Hackers make an effort to constantly force their notes on you. Of course, that is because they rely on the fact you’d panic and eventually pay. Bear in mind that giving into anxiety will cost you a hefty sum of money. Do not become a sponsor of hackers’ illegal business and ignore their attempts to blackmail you. Paying the ransom demanded doesn’t guarantee anything. Your favorite pictures and other files may remain inaccessible. The least you could do is protect your bank account.
How did I get infected with?
Chances are, you clicked open some fake email or message. This is the most commonly used infiltration method when it comes to ransomware. If you come across a questionable email-attachment, do yourself a favor and delete it. That might save you quite the trouble later on because many types of malware travel the Web this way. If you’re especially unfortunate, you might let loose a whole pile of malicious parasites. File-encrypting viruses also use exploit kits and bogus torrents/program updates to get spread online. Always keep an eye out for potential intruders. Preventing malware infiltration is a lot less time-consuming than fighting ransomware, for instance. Stay away from unverified websites as well as illegitimate programs bundles. When installing bundled programs, take your time during the process. Skipping steps exposes your machine to malware and could cause you harm. Also, avoid clicking third-party commercials because those could turn out to be corrupted and harmful. Long story short, you have to be very careful when browsing the Internet. One single wrong move may allow all sorts of dangerous cyber parasites to get installed.
Why is Zayka dangerous?
Zayka Ransomware renames your personal data. It encrypts your files out of the blue thus taking advantage of your panic. As mentioned, panicking is the very last thing you should do. Hackers are trying to trick you into paying a ransom in exchange for a unique decryptor. They even provide the admin@zayka.pro email address. You’re supposed to contact crooks and make the payment so you could regain access to your own data. If that sounds unfair to you, that is because it is. Ransomware uses devious tricks and lies to steal your Bitcoins. The Zayka parasite will involve you in a fraud unless you remain calm and reasonable. Paying would only make the mess greater because hackers may ignore you and keep your files locked. Or, they may provide the decryption key and lock your data again. It goes without saying that you should never make negotiations with criminals. To delete their parasite for good, please follow our detailed manual removal guide. You will find it down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Zayka Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zayka Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zayka encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zayka encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



