Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wanna Decryptor Ransomware?
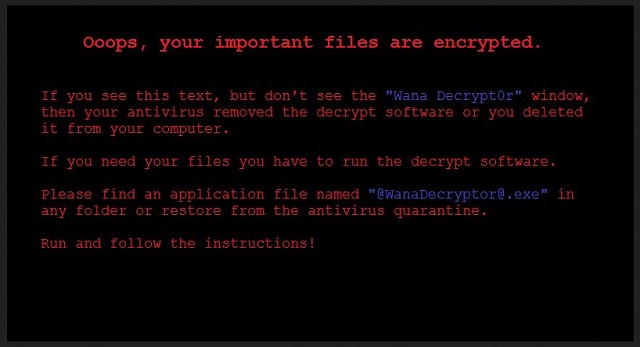
Readers recently started to report the following message being displayed when they boot their computer:
Ooops, your important files are encrypted.
If you see this text, but don’t see the ”Wana Decrypt0r” window,
then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files you have to run the decrypt software.
Please find an application file named “@WanaDecryptor@.exe” in any folder or restore from the antivirus quarantine.
Run and follow the instructions!
Wanna Decryptor, also known as Ransom Decrypt0r, is the newest member of the ransomware family. This piece of software is a classic win-locker. It will sneak into your machine unnoticed. Once on board, this pest will scan your HDD and detect all target files. And then, the virus will encrypt the detected files. This will happen behind your back. The virus won’t betray its cover before the encryption process is complete. You may notice that your PC is performing a bit slower during the encryption process. Once this process is complete, the virus will drop a ransom note. It is a brief explanation of what had happened and the possible outcomes. Here is the tricky part. The hackers are quite smart. They use psychological tricks to make you act impulsively. The ransom note reads that you have only three days to pay the ransom. Apparently, if you miss the deadline, the price will be doubled. However, the games are not ending here. You have seven days in total to make up your mind. The hackers threaten that the virus won’t let you recover your files once the countdown is over. Be rational. Don’t do anything before you are sure. You have enough time.
How did I get infected with?
Wanna Decryptor did not appear as if by magic. To infect your machine, Wanna Decryptor has to distribute its payload file to your machine. The scheme is simple. The hackers would disguise the payload file as an invoice, job application or something entirely different. Then, they will attach this file to an email. You must have guessed it. The hackers rely on the good old spam emails. We all try our best to avoid them, however, this task is getting harder and harder. It is harder to distinguish which emails are spam and which are legit. Therefore, before you open an email, heck the sender’s contacts. You can do so by entering the questionable email address into some search engine. If this email was used for shady business, someone might have complained online. Yet, this technique is not flawless. Therefore, check everything twice. This is your computer. You are the one who is responsible for its security. If you receive an email from an organization, visit their official website. Find their authorized email addresses and compare them with the one you have received a letter from. If they don’t match, delete the questionable email immediately. Other malware distribution techniques include torrents, freeware bundling, and fake software updates. Be vigilant. Only your caution can spare you future troubles.
Why is Wanna Decryptor dangerous?
Ransomware infections are the worst. They are keeping your files as hostages and demand enormous ransom for them. Don’t contact the hackers. These people didn’t hesitate to penetrate your computer. You cannot trust them. They promise decryption services, but will they deliver it? The chances are, they won’t. There are many cases where the victims paid, yet, they did not receive a working decryption tool. You are dealing with criminals. You can’t expect them to play fair. The crooks demand payment in Bitcoins. This currency cannot be tracked down. You can ask for a refund. Even the authorities won’t be able to help you. Unfortunately, there are no free decryption tools. However, you may be able to restore your files from a system back-up. Before you attempt such a recovery, delete the virus. Otherwise, your newly restored files will be encrypted too. Consider discarding your files. Use a trustworthy anti-virus program and delete the ransomware. Or, you can do it manually. Follow our guide and clean your machine for good.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Wanna Decryptor Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Wanna Decryptor Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wanna Decryptor encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wanna Decryptor encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



