Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove vxCrypter Ransomware?
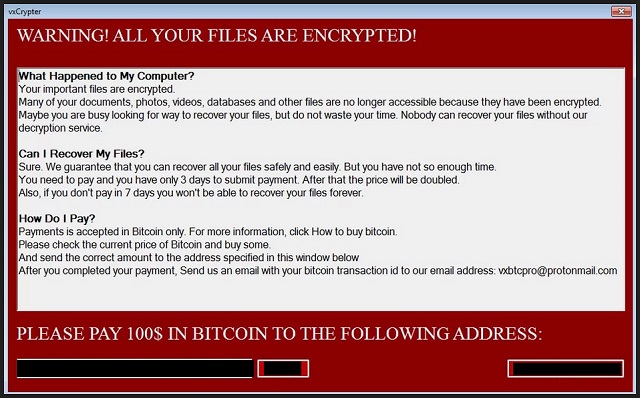
vxCrypter is an interesting ransomware virus. It is based on the unfinished vxLock ransomware. Both viruses use executable files named vxDriver.exe and the .xLck file extension. The experts believe that vxCrypter is still under development, as it has quite a few glitches. This ransomware is also reported to delete duplicate files. Other than that, the virus follows classic patterns. It slithers into your system through deception, corrupts your entire OS, detects the user-generated data, and starts encryption processes. The ransomware is after your documents, pictures, databases, archives. It gets your precious files under lock and key and drops its ransom note. vxCrypter demands $100 paid in Bitcoin. It threatens to double the amount if you don’t pay up within three days. Do not swing into action, though! Take a moment to consider the situation. This virus is still being developed. Practice shows that the inexperienced hackers are often unable to remove their own encryption. Paying does not guarantee results! You will only become a sponsor of cybercriminals. Do not give into naivety. You cannot win against criminals. Your best course of action is the immediate removal of the virus! Find where vxCrypter lurks and delete it upon detection!
How did I get infected with?
vxCrypter relies on classic distribution strategies. It lurks behind corrupted links, fake updates, and spam messages. The virus preys on your carelessness and naivety. All its tricks work only when you let your guard down. Do not make that mistake! No anti-virus app can protect you if you throw caution to the wind. Only your actions can keep your device secure and virus-free. Pay attention to the fine print. Choose caution over carelessness. Always take the time to do your due diligence. Don’t visit questionable websites. Download software and updates from reliable (preferably official) sources only. And, of course, be very careful with your inbox. Whether it’s an instant message or an email, treat all unexpected messages as potential threats. Always verify the senders. If, for example, you receive an email from an organization, go to their official website. Compare the email addresses listed there to the suspicious one. If they don’t match, delete the pretender immediately! You can also enter the suspicious email addresses into a search engine. If they were used for questionable activities, someone might have complained online! Even a little extra attention can spare you an avalanche of problems.

Why is vxCrypter dangerous?
vxCrypter is a complete and utter menace. As soon as this virus invades, corruption follows. The ransomware alters settings, modifies the registry, drops malicious files, and starts dangerous processes. This, of course, happens without any noticeable symptoms. The virus spreads its roots around your entire OS without triggering any alarms. This ransomware is designed to be stealthy. It lurks in the shadows and corrupts your data. The virus locks the user-generated files and adds the “.xLck” extension to them. Everything with that extension is inaccessible. You can still see the icons of your pictures, documents, databases, but you cannot view or edit them. Creating new files is also pointless. Everything gets locked. That’s the plan! vxCrypter makes your computer useless. It pushes you into paying the ransom. Be strong! Don’t give in. Such actions won’t accomplish anything. The hackers tend to ignore the victims once they receive the money. There are cases when the victims paid just to be blackmailed for more. There are also instances when the victims received nonfunctional decryption tools. Do not give into naivety. Don’t pay the ransom. Consider discarding your files. If you have backups stored on external devices and clouds, you can use them to restore your files. Just make sure that the virus is completely removed before you attempt any file-recovery operations.
vxCrypter Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover vxCrypter Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with vxCrypter encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate vxCrypter encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.