Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Troldesh Ransomware?
Troldesh is a hazardous ransomware. If you’re unsure what that implies, it’s pretty straightforward. The first thing you should realize is that the appearance of this tool, on your computer, is a clear sign of trouble. So, expect an abundance grievances and headaches. Why? Well, once the ransomware slithers into your system, it takes over. It encrypts everything you have stored on your PC and does not let you access it. You can’t use the internet, and you cannot go to your Control Panel. You can’t do anything because Troldesh has claimed the power over your system. As the name implies, after the infection invades your system and encrypts everything on it, it demands a ransom to be paid. The ransomware states that if you wish to decrypt your data, you have to pay a ransom. Otherwise, you can say goodbye to your pictures, files, videos, documents, music, everything. And, that’s hardly something to look forward to as no one wants to lose everything they have on their PC. As you would expect from such a hazardous tool, it CANNOT be trusted. Even if you go through with its demands and pay the sum they require from you, you can still be left empty-handed. There are three ways the scenario can go down. One, you pay the “kidnappers”, they give you the decryption key, and you decrypt your files. Come the next day, you find them encrypted again with a new ransom note on your desktop. Two, you pay, and the “kidnappers” choose to not give you the key. And, then there’s option three. It will seem like the most unpleasant one, but, in actuality, it’s the best one of the bunch. Don’t pay. Accept your losses, and say goodbye to your data. That way you may lose valuable information, but at least you won’t grant access to your personal and financial details to strangers with agendas as you would by paying them. Go with scenario number three. It’s for the best.
How did I get infected with?
Troldesh is a sly tool. It resorts to trickery and subtlety to sneak into your system without you even realizing it. And, by the time you do become aware of its presence, it’s already too late as the damage is done. It usually gains access to your PC, courtesy of your distraction, naivety, and haste. More often than not, it uses freeware as a means of infiltration as it provides possibly the easiest entry point. That’s because users tend to rush through its installation. They don’t bother to read the terms and conditions, but just agree to all of them and hope for the best. That’s a poor strategy with horrendous results. If you desire to get stuck with a hazardous infection such as the Troldesh ransomware tool, that’s one sure way to do it. But if you want to protect yourself and your system, be extra careful! Be on the lookout when dealing with questionable updates, spam email attachments, corrupted links, or websites, because Troldesh often uses them as a front to hide behind, as well. Remember, a little extra attention today can save you a lot of future headaches and troubles.
Why is Troldesh dangerous?
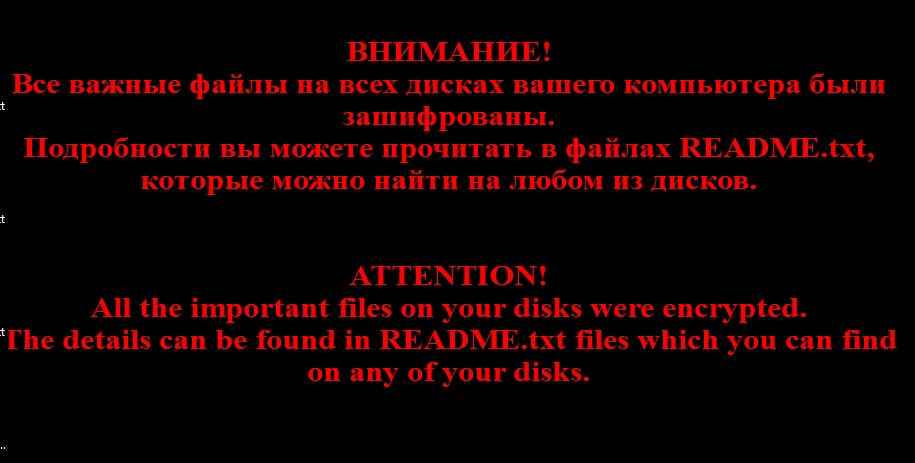
Once Troldesh enters your system, it places your PC under complete lock-down. After it’s done encrypting each one of your files, it displays a ransom note. Since the note is written in English and Russian, it’s safe to assume that the ransomware targets mostly Russian and English-speaking countries. Latest research determines that the ransomware demands to be paid a sum between $250 and $300. Whatever you do, don’t pay! Remember scenario number one and two, which were mentioned above? Going through with the payment will lead to nothing good. Well, at least not for you. It’s of the utmost importance to make backups of all of your files! That way, even if the unspeakable happens, and your PC gets invaded by a ransomware such as this one, you won’t feel backed into a corner and forced to go through with the payment. Do the right thing and back-up your data. Then, maybe you won’t be faced with having to choose whether to pay wicked third-party individuals with malicious intentions and dealing with the consequences that follow that decision, or lose everything you have on your PC. Troldesh is unreliable, dangerous, damaging, infuriating, and, basically, every other negative adjective you can think of. But as obnoxious and hazardous as it is, it’s not worth the trouble of going through with the “kidnappers’” demands. You’ll only bring about more issues than when you started trying to sort them out. Cut your losses, and call it a day. Do yourself a favor, and create backups of your files NOW! That way, if Troldesh attacks your computer, you’ll be ready for it.
Troldesh Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

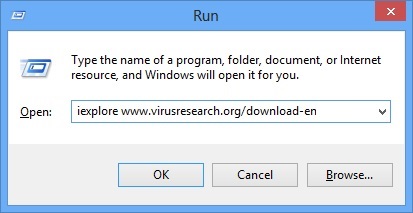
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Troldesh Manually
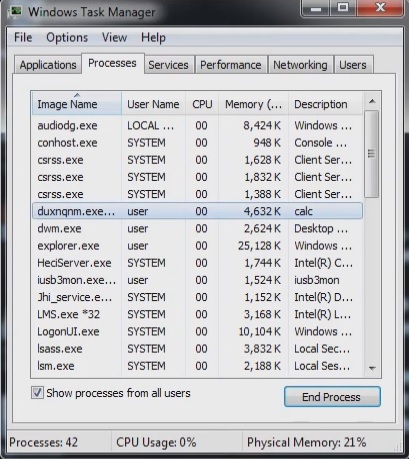
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.