Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Troldesh Ransomware?
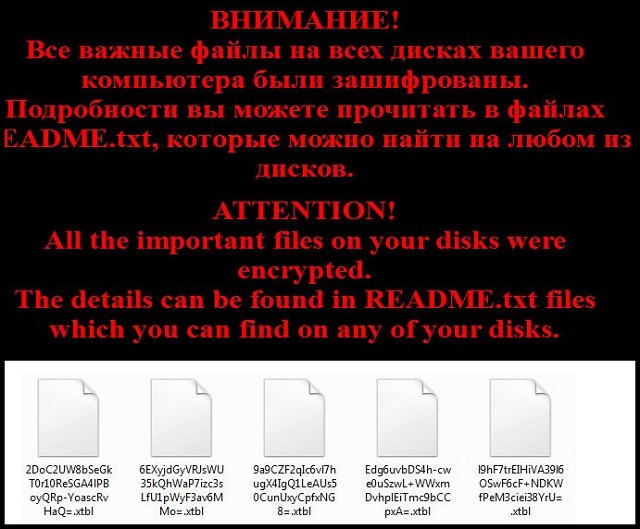
Readers recently started to report the following message being displayed when they boot their computer:
ATTENTION!
All the important files on your disks were encrypted.
The details can be found in README.txt files which you can find on any of your disks.
Troldesh is the name of a ransomware threat. It also goes by Encoder.858 or Shade. The Troldesh threat infiltrates your system via trickery, then corrupts it. It uses encryption algorithms to lock every file, you have on your PC. Music and audio files, pictures and videos, archives and documents. It all gets locked. The infection appends a special extension at the end of each file, to solidify its grip. It follows the format: [random characters]=.xbtl. Once the renaming process is complete, your files get rendered inaccessible. The only way to access them again, is to comply with the cyber kidnappers’ demands. Speaking of, once the encryption finishes, you see your Desktop picture replaced. It now displays a message. You also find about 20 text files on your Desktop. As well as, a text file in each folder that contains locked data. They all share a name in the format: README[number].txt. That’s the infection’s ransom note. It contains instructions for you to send a specific code to a certain email address. The note offers no specifics. Instead, you’re expected to contact the cyber criminals via that email. And, communicate with them on establishing the ransom amount, and payment details. Do NOT do that! Don’t contact these people, and don’t follow their demands. Compliance guarantees nothing. And, it tends to lead to regret. Yes, the cyber criminals promise to send the decryption key, you need, after payment. But promises are not guarantees. Don’t waste your money on the word of cyber extortionists. Don’t comply.
How did I get infected with?
Ransomware infections are an utter cyber menace. How do you imagine you got stuck with the Troldesh one? Well, it managed to slither past you, unnoticed. The tool resorts to the old but gold invasive methods, when it comes to gaining entry to your PC. It turns to the usual tricks, and does its best to slip by, undetected. The common invasive methods, include the following. Hiding behind corrupted links, sites or torrents. Not to mention, freeware, and spam emails. As well as, posing as a fake update. The infection isn’t shy about using every known trick in the book. It’s up to you to spot its trickery. Don’t get fooled! Caution helps you to prevent infections, like Troldesh, from invading. Be thorough! Read terms and conditions, look for the fine print, and double-check everything. Don’t click or download anything, unless you’re sure it’s safe. Even a little extra attention can save you a ton of troubles. And, carelessness invites them in. Make the right choice. Don’t give into naivety, don’t rush, don’t throw caution to the wind. Don’t ease the infection’s infiltration.

Why is Troldesh dangerous?
The cyber criminals, behind Troldesh, offer room for negotiation, regarding the ransom amount. Several users online, who were victims of the ransomware, shared their experience. They claimed to have reached out to the cyber kidnappers, and haggled for the price. And, they managed to get discounts. If the extortionists demanded $250, they managed to get it down to $125. However, that’s ill-advised. Experts urge against contacting these people. Don’t reach out to them. And, don’t pay them a dime. Here’s the thing. Even if they offer you a 90% discount, what then? Will you pay the price? Well, if you do, there’s a few ways the situation can unfold. Let’s examine them. Say, you pay, provide proof of payment, the works. You do your part, and await to receive the decryption key. What if these people don’t give it to you? They can double-cross you, and send you nothing? Or, send a key that proves useless? Think about it! You have ZERO guarantees, they’ll keep their end of the bargain. You rest only on their word. And, can you trust the word of cyber criminals? People, who unleashed an infection on you, encrypted your files, and extorted you for money? Don’t be naive. Keep your money, and don’t waste your time and energy, dealing with these people. They’re unreliable and malicious, and the odds are not in your favor.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Troldesh Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Troldesh Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Troldesh encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Troldesh encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.