Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove Total Access Network pop-ups?
If messages, emails, or pop-ups by Total Access Network congratulate you on winning great prices, don’t get your hopes up. That’s a scam! Do not fall for these lies. The crooks promise gift cards, the latest phones, and money. To get these prices, however, they ask you to provide them with your personal information and financial details. Again, don’t fall for the tricks! You are facing a common phishing scam. The crooks pretend that they need your name and address to send you the gifts, but they also ask for other private details such as phone numbers, email addresses, credit card details, and more. Don’t act impulsively. See through the deception! Everything you share with the crooks will be used against you. Delete the Total Access Network messages and pay close attention to your computer. If the messages reappear, run a virus scan immediately. Scams like the Total Access Network one are usually spread through scamware parasites. Make sure that your computer doesn’t harbor one.

How did I get infected with?
A scamware menace displays the Total Access Network messages. This parasite sneaks into your computer and throws you into a whirlwind of false ads, deceptive messages, and corrupted websites. Do not imagine cyber-attacks, though. The scamware is not a virus, but a deceiver. It lures you not only into online scams but also into installing it. That’s right. The parasite tricked you into approving its installation. This menace knows how to manipulate people. It either pretends to be a useful app or a critical update. It might also use a software bundle or a spam message to sneak into your computer. The scamware has many tricks up its sleeve. Your caution, however, can prevent them from succeeding. Even a little extra attention can spare you an avalanche of problems. So, don’t be lazy! Always take the time to do your due diligence. Don’t visit dodgy websites. Download software and updates from reliable sources only. And forget about the “Next-Next-Finish” setup strategy. If available, use the advanced/custom setup option. Deselect the unwanted bonus apps and go through the terms and conditions. Don’t hesitate to abort the installation if you notice anything suspicious!
Why are these ads dangerous?
The Total Access Network scam is a nasty one. Its messages usually pop up in your email inbox, but they may also bombard you as advertisements online. If you get flooded with them, don’t waste time and run a virus scan. Scamware spreads these phishing messages. It sneaks into your computer and floods your browser with deceptive messages. If it fails to lure you into one trap, it tries with another. The scamware has only one purpose – to push people into unwanted actions. It displays misleading messages, as well as redirects your web traffic to deceptive pages. Do not underestimate it! It is a menace that exists to generate revenue for its criminal publishers. These crooks are after your money, private data, and computer resources. The criminals use various tricks to make a mint at your expense. And the scamware is a tool that helps them achieve their criminal goals. Do not wait to see how imaginative their scams can be. The Total Access Network pop-ups are your warning – your computer is corrupted and no longer secure. Take immediate action! Find where the scamware hides and delete it upon detection. Remove this parasite before it gets a chance to cause you harm!
How Can I Remove Total Access Network Pop-ups?
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 3: Permanently Remove Total Access Network from the windows registry.
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
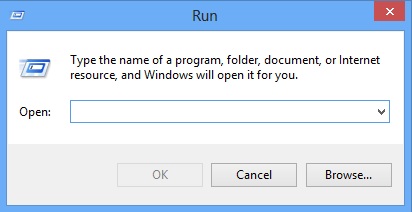
Type “Appwiz.cpl”
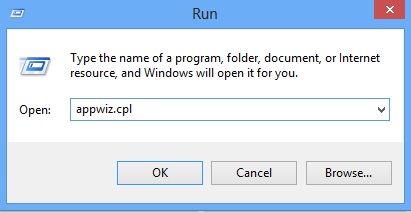
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
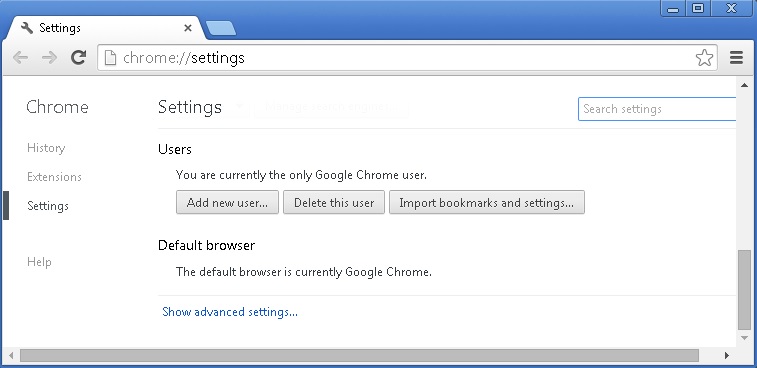
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
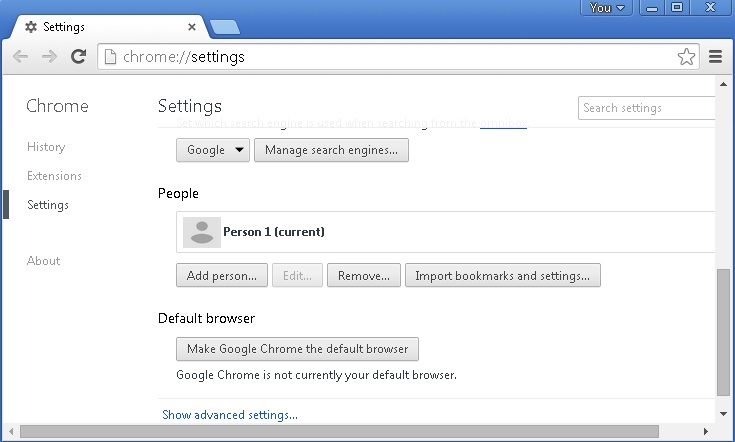
- choose a preferred name.
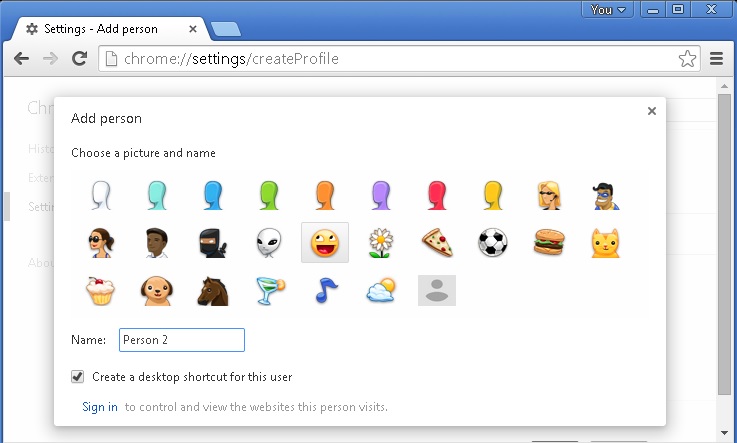
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
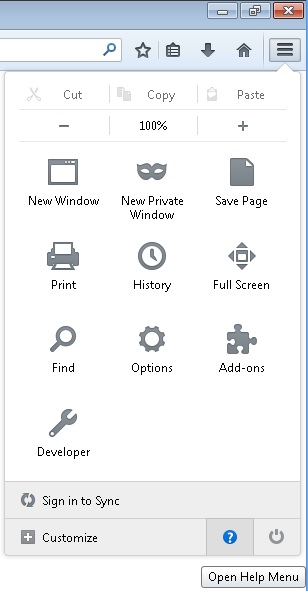
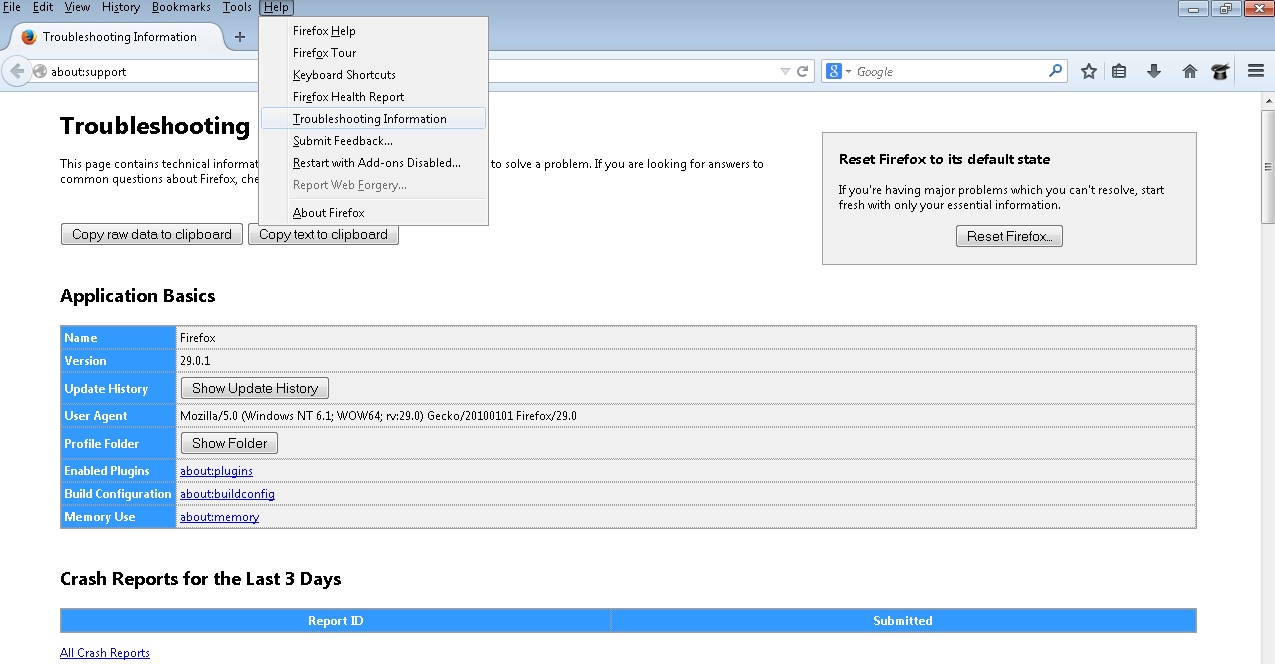
- Then Troubleshoot information
- Click on Reset Firefox
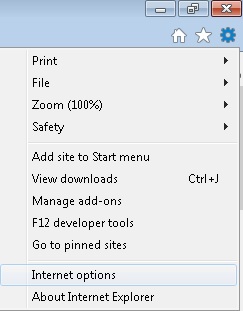
Remove from Internet Explorer
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
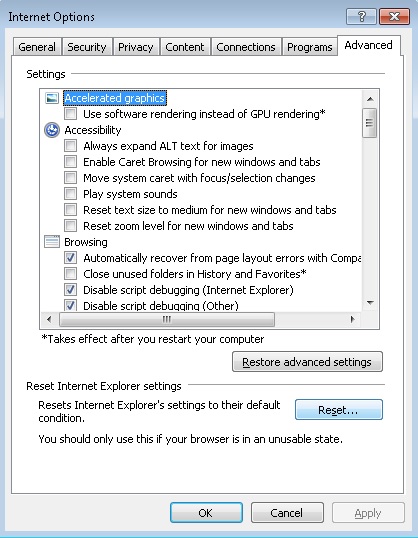
- Check the “Delete Personal Settings Tab” and then Reset
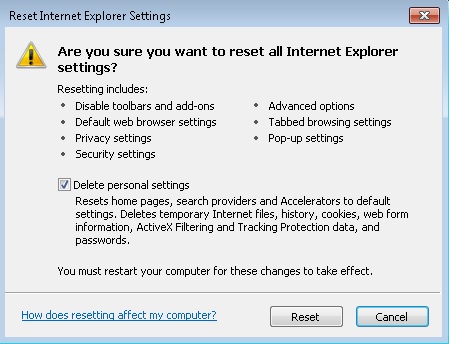
- Close IE
Permanently Remove Total Access Network Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.