Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Surprise File Extension Ransomware?
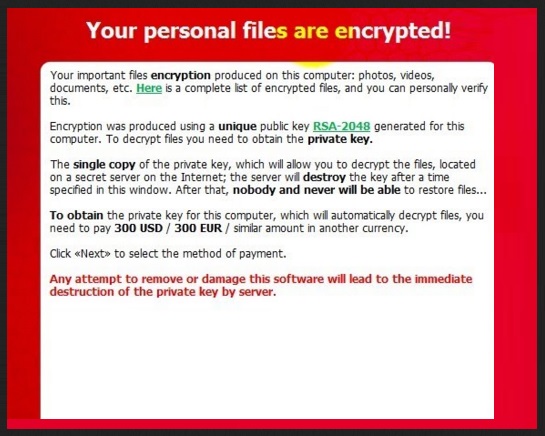
The .SURPRISE file extension will indeed surprise you. In a bad way. This thing is a clear sign for serious virtual trouble. As you could imagine, your files have been modified because you currently have a virus on board. To be exact, you’re now stuck with one of the most harmful, problematic, deceptive and resourceful infections on the Web. Are you surprised already? Your computer has been infected with ransomware. You will be greeted by this message:
Quote
What happened to your files ?
All of your files were protected by a strong encryption.
There is no way to decrypt your files without the key.
If your files not important for you just reinstall your system.
If your files is important just email us to discuss the price and how to decrypt your files.
You can email us to nowayout@protonmail.com and nowayout@sigaint.org
Write your Email to both email addresses PLSWe accept just BITCOIN if you dont know what it is just google it.
We will give instructions where and how you buy bitcoin in your country.
Price depends on how important your files and network is.it could be 0.5 bitcoin to 25 bitcoin.
You can send us a 1 encrypted file for decryption.
Feel free to email us with your country and computer name and username of the infected system.
That means you have to take adequate measures before the virus manages to cause you irreversible damage. It’s perfectly capable of doing so. Ransomware offers an extremely convenient method for hackers to gain illegal profit online. Obviously, crooks love using unfair monetizing tactics which is why they keep developing ransomware programs. Now, how does the scheme work? First of all, your computer gets compromised. It goes without saying that this happens completely behind your back because nobody would install such a vicious infection voluntarily. Once this stealthy installation is complete, the ransomware gets activated almost immediately. It performs a full scan on your computer searching for personal data to encrypt. Keep in mind that this parasite infects a rich variety of files – .mp3, .mp4, .pdf, .jpeg, .png, .txt, .doc, .docx, .xls, .xlsx, .rar, .zip, etc. That means a huge percentage of your personal information falls victim to the parasite’s trickery. You will notice that the surprising .SURPRISE file extension has replaced the original one thus making your date unreadable. You computer won’t be able to recognize this new file format. Your data is now practically useless. By adding its malicious file appendix, ransomware locks out your access to your own information. That includes pictures and music and videos and Microsoft Office documents and presentations and anything else of value you may have stored on your device. Ransomware uses a complicated encrypting algorithm to lock all files it has located. Then it starts manipulating you. While it was encrypting your information, the parasite also created random .txt files in every single folder that contains infected data. And, as you could imagine, those are a lot of folders. Why are hackers so persistent in showing you these .txt files? Because they give you thorough payment instructions. And yes, hackers want you to follow them. According to this ransom note, you have to contact the parasite’s developers if you wish to restore your encrypted files. Supposedly, after paying a certain sum of money, you will receive a decryption key which will allow you to regain access to your files. The ransom message provides you two equally unreliable email addresses – nowayout@protonmail.com and nowayout@sigaint.org. Obviously, you have to stay away from both of them. Paying the money demanded guarantees you absolutely nothing. Therefore, don’t let cyber criminals blackmail you and don’t make your already bad situation worse.
How did I get infected with?
Unfortunately, there are a lot of efficient virus infiltration techniques on the Web. The parasite’s unwanted presence on board means you fell victim to one of them. For example, you might have stumbled across a malicious spam email-attachment or a spam message from some unknown/known sender. You might have also installed the ransomware by clicking a corrupted third-party ad or by visiting a malicious website. Keep in mind that infections could also get attached to safe programs. That means you always have to watch out for potential threats when installing freeware and shareware bundles. Don’t trust unverified websites because the illegitimate program bundles offered there, are usually dangerous. Also, opting for the advanced/custom option in the Setup Wizard might easily prevent virus installation on time. In addition, stay away from suspicious executables and make sure you pay attention to your machine. Otherwise, you’re practically jeopardizing your very own safety. You could simply never be too cautious online.
Why is Surprise File Extension dangerous?
You should know that ransomware is notoriously problematic. It’s aiming directly at your bank account and allows hackers to make easy money by scamming you. Therefore, there’s absolutely nothing safe about the situation you’re in right now. And it’s time to take action. As we already mentioned, the virus you’re stuck with attempts to charge you for your own personal files. Furthermore, the ransom demanded is usually quite a hefty one. The parasite not only encrypts your data by adding a nasty .SURPRISE file extension; it also tries to play mind games with you. That’s why you’re seeing its aggravating ransom message. What you have to do is ignore all empty promises and lies the parasite has prepared for you. Paying and ransom only guarantees that you will lose your money and crooks will get it. Do you want to become a sponsor of greedy cyber criminals? If not, keep your money. Hackers have no reason whatsoever to provide you any decryptor or decryption key. So don’t let hem deceive you. To get rid of the ransomware manually, please follow the detailed removal guide that you will find down below.
Surprise File Extension Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover Surprise File Extension Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Surprise File Extension encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Surprise File Extension encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



