Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Spectre Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
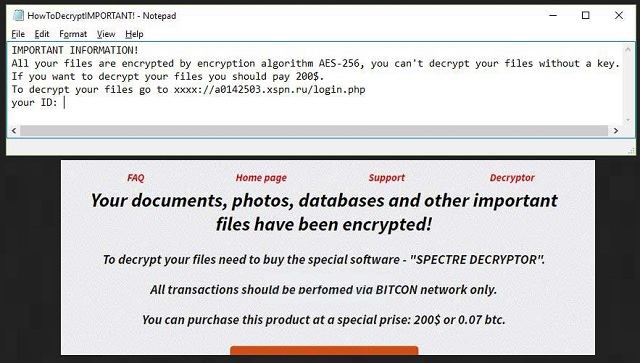
IMPORTANT INFORMATION!
All your files are encrypted by encryption algorithm AES-256, you can’t decrypt your files without a key.
If you want to decrypt your files you should pay 200$.
To decrypt your files go to hxxp://a0142503.xsph.ru/login.php your ID:12052
This time, Spectre has nothing to do with James Bond. The Spectre Ransomware is yet another file-encrypting pest. It attempts to blackmail gullible PC users. Hence, as soon you realize you’re stuck with ransomware, you have to take action. Do not waste time as ransomware is rightfully considered to be the most problematic type of virus out there. Not only is it aggressive but is also uses lies and deceit. Long story short, there is a reason why nobody wants to be dealing with file-encrypting infections. Make sure you uninstall this nuisance before you fall right into hackers’ trap. Spectre Ransomware firstly initiates a scan of your computer. By doing so, the parasite successfully locates your private files. We’re talking photos, videos, music files, documents. Ransomware targets all the information you’ve stored on board. Do you have backup copies of your valuable data? You definitely should. Now that you’ve seen for yourself how dangerous ransomware is, do not let it cause harm again. Protecting your files in advance is strongly recommended. Once Spectre Ransomware finds your data, the encryption process begins. This particular parasite uses the infamous AES-256 encrypting algorithm. Such a strong cipher could easily lock all your important, favorite files. And that’s not even the end of your problems. You see, Spectre Ransomware modifies the format of the target information. It also renames your files with a random combination of symbols. You will notice the .spectre file extension as well. If you come across this brand new appendix, know your data is no longer accessible. Instead, it’s being held hostage by greedy cyber criminals. Crooks actually encrypt your data in order to trick you into paying for a decryptor. It goes without saying that you probably want your files back. Conveniently enough, hackers have a solution. They offer you a rather simple deal. Unfortunately, the decryption key doesn’t come for free. Spectre Ransomware drops the “HowToDecryptIMPORTANT!.txt” files which contain detailed payment instructions. You’re supposed to buy a decryptor at the “special” price of 200 USD. However, there’s absolutely no guarantee crooks will ever provide the tool you were promised. Yes, you may make the payment right away and still remain unable to open your files. To put it mildly, negotiating with cyber crooks wouldn’t be a bright idea. Hackers are so focused on gaining money that freeing your data isn’t even part of the picture. Don’t allow crooks to scam you and tackle the ransomware ASAP.
How did I get infected with?
The most commonly used method involves fake email-attachments. Many people make the mistake of clicking open all emails they receive. Obviously, you’d be taking a huge risk that way. Hackers often present malware as perfectly safe job applications, for example. They even include various logos and emblems in the bogus email to make it appear legitimate. Always watch out for potential parasites. If you stumble across an email or message you don’t trust, don’t open it. It only takes one single click to let loose a vicious infection. Hence, don’t be gullible and save yourself the trouble. Stay away from spam messages and random email-attachments. Whether your machine will remain safe or not is entirely up to you. Ransomware also travels the Web via exploit kits, fake torrents, fake program updates, fake software bundles. Do you see the pattern? There are plenty of opportunities for crooks to cause you damage. All you have to do in order to protect your device is be careful. Don’t forget to pay close attention to everything you’re about to click open or download. The Internet is full of harmful parasites which are more than capable of causing you a headache. If you let hackers compromise your security, there’s nobody to blame.
Why is Spectre dangerous?
This infection locks all your information. It practically denies you access to your files and then attempts to charge you for the privilege to use them. Ransomware gets solely developed to create confusion. The thing is, though, giving into anxiety and panic is exactly what you shouldn’t do. Agreeing to follow hackers’ malicious instructions would only make matters worse. Instead of becoming their sponsor, ignore the empty promises Spectre Ransomware makes. Remember, hackers are trying to involve you a cyber fraud. Crooks are aiming at your bank account so you cannot afford to negotiate with them. If anything, you’d also jeopardize your privacy by paying the ransom. You’d also be wasting 200 USD. Do the right thing and get rid of this deceptive parasite right away. You will find our detailed manual removal guide down below.
Spectre Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Spectre Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Spectre encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Spectre encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



