Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove SnakeLocker Ransomware?
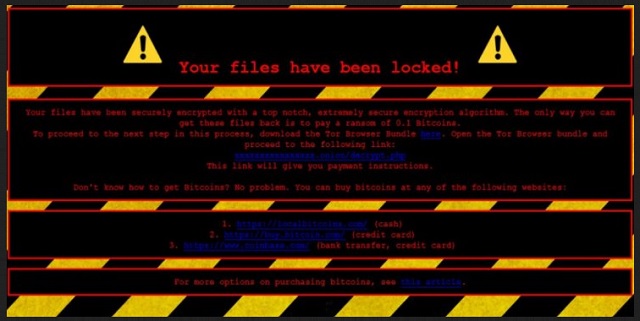
Readers recently started to report the following message being displayed when they boot their computer:
Your files have been securely encrypted with top notch, extremely secure encryption algorithm. The only way you can
get these files back is to pay ransom of 0.1 Bitcoins.
To proceed to the next step in this process, download the Tor Browser Bundled here . Open the Tor Browser Bundle and proceed to the following link:
[.ONION DOMAIN]
This link will give you payment instructions .
Don’t know hot to get Bitcoins? No problem. You can buy bitcoins, at any of the following websites:
[LINKS TO POPULAR BITCOIN SITES]
SnakeLocker is the newest member of the Ransomware family. This parasite is a classic in its field. Just like its name suggests, SnakeLocker sneaks into its victims’ computers and spreads its poison. The ransomware was first detected on July 2017 and since then is spreading like wildfire. Once on board, the virus scans your HDD for target files, locks them and then displays its ransom note. SnakeLocker targets user generated files like your pictures, documents, videos, databases, etc. The reason for its preferences is quite obvious. Victims are much more likely to pay for their memories and work than for anything else. If you see the dreaded “Your files have been securely encrypted” message, you are in some serious trouble. SnakeLocker has managed to encrypt your precious files. You can still see the icons of your documents, pictures, etc., yet, you cannot open or use them. The ransomware uses a combination of the RSA and AES encrypting algorithms. These two are the strongest known. Currently, there are no decryption tools for this ransomware. Security experts, however, are working on a solution. So, don’t lose hope. And most importantly, do not pay the ransom. SnakeLocker demands 0.1 Bitcoins (about $420 USD). This currency is untraceable. If things don’t go as planned, no one can help you. You cannot ask for a refund. You are dealing with cyber criminals. Never forget that. These people have proven to be smart. They created their ransomware in two deadly variants. SnakeLocker Ransomware is one. It uses the “.snake” extension to mark all encrypted files. The other version uses a “.TGIF” extension. Both ransomware variants are deadly. So, consider discarding your files.
How did I get infected with?
SnakeLocker Ransomware is mainly distributed via spam messages. Yes, even today, the good old spam emails are the number one cause of virus infections. The virus itself does not travel via email. The spam emails distribute corrupted attachments, usually MS office files, which contain macro scripts. Once you open these files, the scripts are executed. They download the virus. For this reason, your anti-virus program wasn’t able to detect the files as dangerous. Therefore, do not download anything. Don’t even open emails from strangers. Check the sender contacts first. It is quite a simple task. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone might have complained. Yet, this method is not flawless. New emails are created every day. Double-check the sender. The crooks tend to write on behalf of well-known organizations and companies. If you receive such an email, go to the company’s official website. You can find their authorized email addresses there. Compare them with the one you have received a message from. If they don’t match, delete the pretender immediately. Also, keep in mind that reliable companies will use your real name to address you. If you receive a letter starting with “Dear Customer” or “Dear Friend,” continue with caution. Only your vigilance can keep your PC clean!
Why is SnakeLocker dangerous?
SnakeLocker Ransomware is quite dangerous. Currently, files locked by this ransomware cannot be decrypted. We strongly recommend against paying the ransom. You are dealing with criminals. Practice has shown that they tend to ignore the victims once the ransomware is paid. Furthermore, paying the ransom demonstrates your willingness to negotiate. The hackers can target you. They can include you in scam campaigns and reinfect your device. How many times are you willing to pay for your files?! One more thing to mention here. If you use your PC to settle the ransom, the virus can record your paying details. Credit card details, bank account, usernames, passwords, email addresses, these details should not become a possession of hackers. Therefore, use a trustworthy anti-virus program to clean your device ASAP! If you have system backups saved on external devices, you can use them to restore your files. Be advised, however. If you plug any device into your infected PC, the ransomware will infect it too. As you can see, your best course of action is the removal of the virus. The sooner SnakeLocker Ransomware is gone, the better!
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
SnakeLocker Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover SnakeLocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with SnakeLocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate SnakeLocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



