Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove ShinoLocker Ransomware?
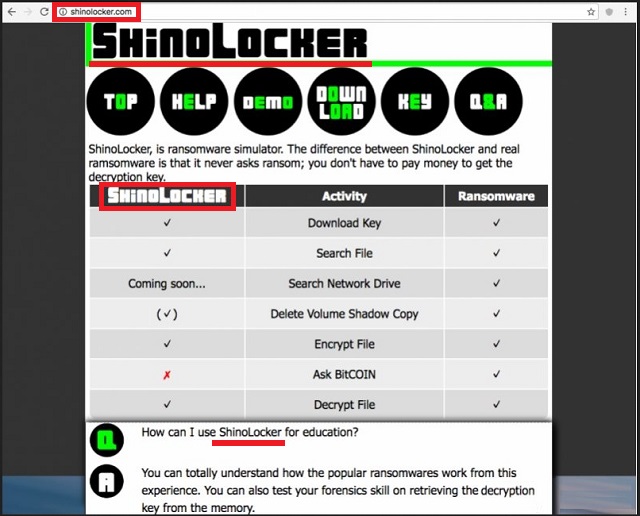
ShinoLocker is a ransomware simulator. It’s supposed to help you understand how ransomware-type programs work. Eventually, you should be able to protect yourself from these virulent infections. You see, ransomware viruses are probably the most worrisome type of malware out there. They are just as sneaky and cunning as they are aggressive. What’s even worse is that ransomware is currently on the rise. Hackers keep on tirelessly working on new malicious programs. Logically, our research team comes across new ransomware-type infections every single day. What makes ransomware so popular among cyber criminals? These programs are aiming directly at your bank account. Other parasites use more subtle, devious methods to steal your money. Ransomware, however, does none of that. As soon as the parasite gets installed, it performs a thorough scan on your machine. This way it locates all your personal files. Music and picture and videos and MS Office documents. Anything of value you may store on the device falls victim to the parasite. Do you now see why these infections are so immensely dreaded? Ransomware goes after your personal files. It attacks all your private information, including your most precious and important data. Next step is encryption. By using a highly complicated encrypting cipher, the parasite locks your data. It creates a random extension and renames the target files. Anything modified by the ransomware is left completely inaccessible and useless. The virus changes your files’ formats thus making them unreadable. Then it asks for money in order to free your encrypted files. Ransomware hits where it would hurt the most – at your personal data. This is a particularly harmful kind of infection which could cause you inexplicable damage. Furthermore, the Web is infested with ransomware. Installing some infection of this kind is a very easy task. Now, back to your problem. ShinoLocker was created solely to help you in the never-ending battle against ransomware. This program’s developer, Shota Shinogi, says you can use it for education purposes. It basically allows you to create ransomware so you could learn more about these pests. As you can see, this sounds like a great idea. You could lock your files with the AES-128 encrypting algorithm. You also choose what kinds of file formats the parasite locks. According to its official website, ShinoLocker “nevers asks for ransom”. However, not all people have Shinogi’s good intentions and lots of customized versions have appeared online. You see where this is going, don’t you? There are malformed ShinoLocker programs which look identical to the original. And these modified programs are incredibly dangerous.
How did I get infected with?
The real ShinoLocker program could be downloaded from its official website. Its malicious versions, however, travel the Web quietly. They may be sent directly to your inbox as an email-attachment. Stay away from anything questionable you may come across and don’t click open spam. The most popular infiltration method is spam messages so make no mistake. Instead of being careless, make sure you know what you’re opening. Delete what you don’t trust and take your time. Ransomware also gets spread online using Trojans. Hence, if your machine ends up infected with ransomware, check out the PC. Chances are, there will be more parasites on your computer. Some viruses might get attached to freeware/shareware bundles. Avoid illegitimate programs and unverified torrents. Last but not least, avoid third-party ads and illegitimate websites. You have to always keep an eye out for potential threats. Remember, uninstalling a virus is problematic. Preventing installation in the first place is indeed the better option.
Why is ShinoLocker dangerous?
ShinoLocker’s malicious versions are practically ransomware infections. They get spread using deceit and they encrypt private files. Any well-intentioned program may become dangerous when it gets into the wrong hands. ShinoLocker is yet another example of that. Even though it was originally meant to protect PC users, hackers have found a way to misuse it. Once the parasite gets installed, it causes the same harm a typical ransomware does. That includes file encrypting, a ransom note and some bogus encryption key. Instead of giving your money away, though, you have to tackle the parasite. There’s no reason to keep a malicious copy of ShinoLocker on board. It attempts to blackmail and scam you. Do the right thing. Don’t overlook hackers’ creativity and don’t be careless. To delete this pest, please follow our detailed removal guide down below.
ShinoLocker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover ShinoLocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with ShinoLocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate ShinoLocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



