Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
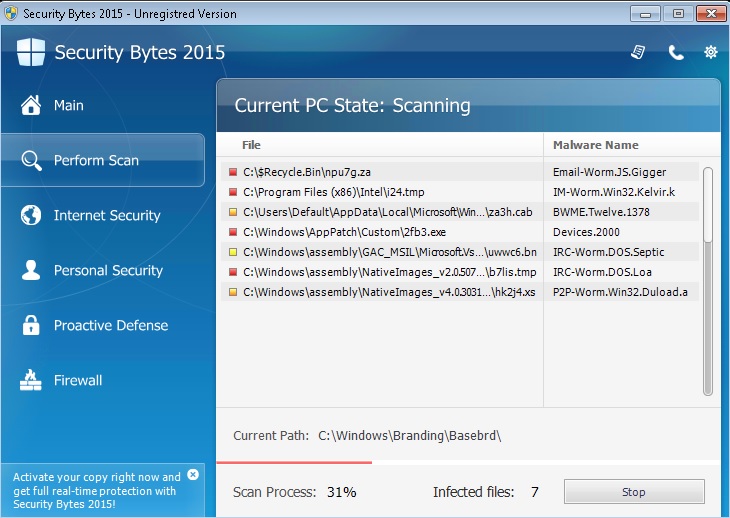
Remove Security Bytes 2015 immediately!
Security Bytes 2015 is an anti-virus program that infects your computer and, basically, blocks your entire system and prevents you from taking any course of action, unless you pay a fee. The fee will allow you to buy a security system, which would supposedly cleanse your system of all the threats found by Security Bytes 2015. Don’t be fooled by this notification! In reality, the program tricks you into paying money for something that you do not need and is of absolute no use for you. Security Bytes 2015 is utterly unreliable, because it is incapable of doing system scans. However, it’s designed to look as if it is doing just that, in order to convince you to pay for something you can go without. There are much better ways to spend your money, so do yourself a favor and don’t waste them on Security Bytes 2015. As soon as you find out that it has infiltrated your computer, get rid of it.
How did I get infected with Security Bytes 2015?
Security Bytes 2015 is a typical bogus anti-virus program that slithers into your system via the usual deceptive methods, as it doesn’t need your permission to enter your system. Also, more often than not, the infection is passed on through the use of compromised websites. Once you click on them, you get the not-so-exclusive opportunity to see how a program that is not capable of doing system scans, not only successfully does one, but also finds a ton of potential threats that your regular AV program missed. Like, Calculator, Skype, Notepad; basically everything on your PC. Sounds suspicious, right? Well, that’s because it’s all a stunt designed to trick you into believing the infection and paying for the program. What you should know is that all Braviax family programs are incapable of doing system scans, and you’ve guessed it – Security Bytes 2015 is part of the Braviax family.
Why is Security Bytes 2015 dangerous?
You should be wary of Security Bytes 2015, because as soon as its installation process is over, it goes to work. First it scans your system, and its scans always show that every program on your computer is full of Trojans that can do serious damages. Therefore, its next course of action is to prevent you from being able to open and use these infected programs, i.e. all the programs on your PC. The best advice you can follow is this: do NOT trust Security Bytes 2015 and make sure you get rid of it as soon as it first makes an appearance. By doing so, you’ll save yourself a lot of potential troubles and frustration.
Security Bytes 2015 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Infected Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your infected computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
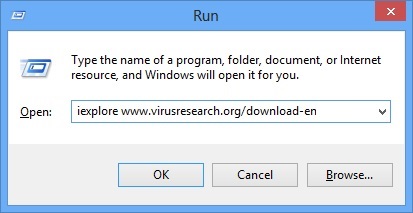
- your Internet Explorer will open and a professional scanner will start downloading
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
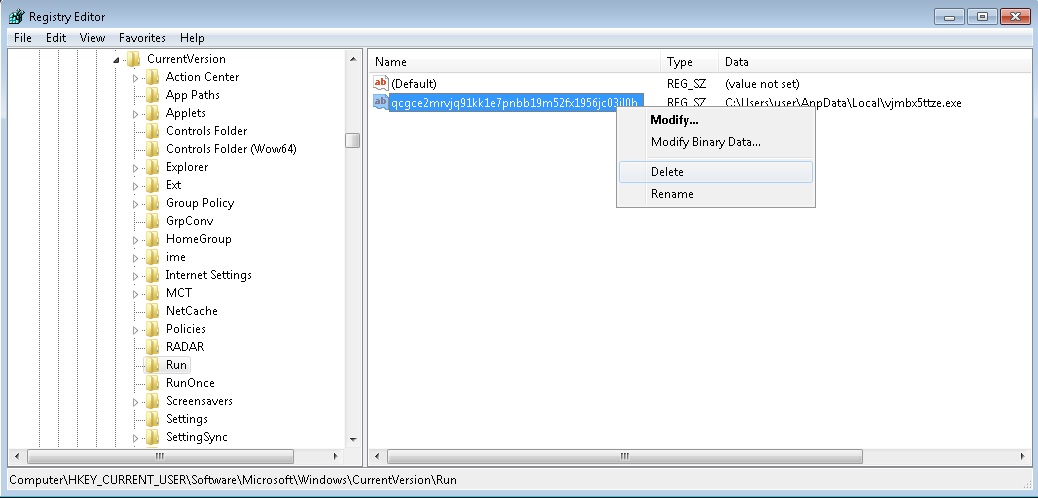
To perform Manual removal you need to delete the following files and registry keys. These were in our case:
- Open your registry editor and delete the randomly generated Run Subkey:
- Go to your local application data folder and delete the file: vjmbx5ttze.exe
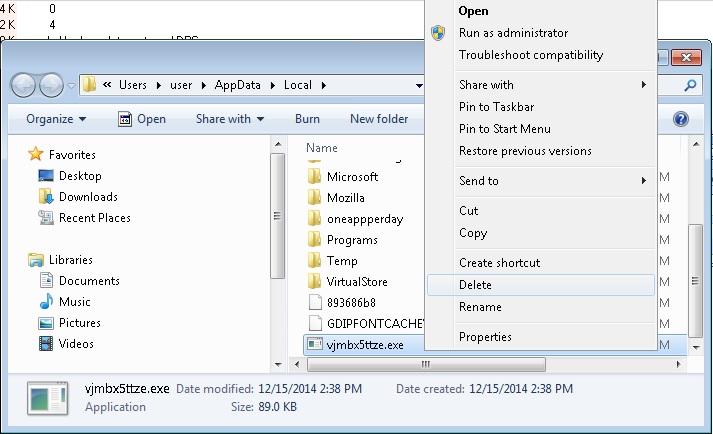
Use your msconfig program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they are generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to double check with a reputable anti-malware program after manual removal.



