Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
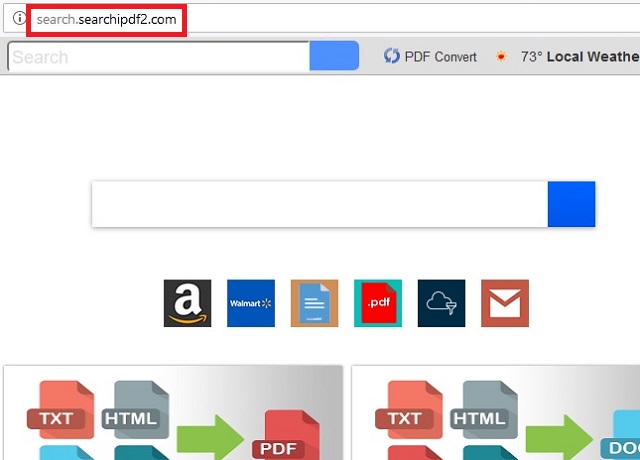
Can’t Remove Search.searchipdf2.com hijacker virus? This page includes detailed Search.searchipdf2.com Removal instructions!
There’s a browser hijacker on your computer. The nasty cyber threat slithered its way into your system, undetected. And, with the display of the Search.searchipdf2.com page, clues you into its existence. Consider its display a clue, a warning. The page announces the infection’s presence. Don’t discard its announcement, but heed it. Hijackers are quite the hazardous threats. They’re an utter plague on your system. Once they invade, prepare for problems. The infection wastes no time, and begins its corruption at once. So, it doesn’t take long before you get flooded with issues. At first, they seem minor, almost insignificant. But if you don’t take immediate action against the threat, they evolve. That’s right. The longer the tool remains, the worse your situation gets. Problems escalate, and worsen with time. What begins as an online interference grows into a privacy hazard. Don’t allow that! Don’t extend the hijacker’s stay beyond the point of discovery. Get rid of the menacing infection as soon as you become aware of its existence. There aren’t enough ways to stress the importance of urgency. Do NOT delay! Delays have repercussions, and lead to regrets. The appearance of the Search.searchipdf2.com page is your sign of action. Heed it! Locate where the hijacker lurks, and delete it when you do. Do it ASAP.

How did I get infected with?
Hijackers are sneaky. They turn to trickery, and via slyness and finesse, invade your PC. Not only do they manage to slither in undetected, but they get you to give them the green light, too. Oh, yes! And, so did the one, using Search.searchipdf2.com as a face. It may seem a bit confusing, but it’s rather simple. Let’s explain. No hijacker can enter a system without user’s consent. The tool has to ask if you, the user, agree to admit it into your PC. Only if you do, can it proceed. But, then, how did it manage to invade undetected? Well, easy. It sought your permission in the sneakiest way possible. It was so covert with its inquiry, that you didn’t even realize you gave consent to an infection. Here’s the thing. Yes, a hijacker has to seek your permission on its admission. But, no, it doesn’t have to do it outright. So, it doesn’t. It’s not straightforward, but the exact opposite. The tool chooses the most covert way it can. And, the old but gold invasive methods assist with its sneakiness. Corrupted sites, fake updates, spam emails, freeware, the usual antics. However, neither of these methods can prove successful without a key ingredient. You. Well, rather, your carelessness. The hijacker needs you to throw caution to the wind, and rely on luck. To skip doing due diligence, and agree to the terms and conditions in blind faith. It needs you careless, and not cautious. Why oblige? Why make its invasion easier? Protect your PC from harmful threats, and always choose caution over carelessness. Don’t give into naivety, haste, and distraction. Be thorough. Be vigilant. Attention goes a long way.
Why is this dangerous?
As soon as the hijacker sneaks into your system, be wary. It doesn’t take long before its havoc-wreaking begins. And, you start to get flooded with issues, non-stop. Your grievances tend to begin with your browsing. All of a sudden, you can’t seem to make a single move, without interference. You face countless disruptions. And, you have the hijacker to ‘thank’ for that. It redirects you to the obnoxious Search.searchipdf2.com site, at every turn. As well as, floods your screen with in-text, pop-up, and banner ads. Open a new tab? Search.searchipdf2.com is there to greet you, alongside an array of ads. Ads, which are “Powered by Search.searchipdf2.com.” Or, “Brought to you by Search.searchipdf2.com.” Type in a search, and it’s the same thing. Among the suggested results, you’ll see the bothersome page. As well as, countless ads scattered across the screen. If you so much as touch your browser, the hijacker interferes. Going online becomes quite the dreadful experience. But the browsing intrusions are the least of your concerns. The nasty threat takes aim at your privacy. It follows programming to spy on you, and collect data from your actions. And, that’s what it does. It monitors your online activities, and records everything you do. When it deems it has gathered enough information, it sends it. The nasty tool hands it over to the cyber criminals that published the infection. Let that sink in for a moment. Strangers with malicious intentions. Those are the people, who get a hold of your personal and financial details. Are you going to allow that? Or, would you rather, avoid the risks that follow a hijacker? As soon as you spot Search.searchipdf2.com, accept the danger, you’re in. Acknowledge the hijacker’s presence, and act towards its prompt removal. The sooner you find and delete it, the better.
How to Remove Search.searchipdf2.com virus
The Search.searchipdf2.com infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Search.searchipdf2.com infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Track down Search.searchipdf2.com related processes in the computer memory
STEP 2: Locate Search.searchipdf2.com startup location
STEP 3: Delete Search.searchipdf2.com traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Search.searchipdf2.com related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Search.searchipdf2.com startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Search.searchipdf2.com virus from the windows registry
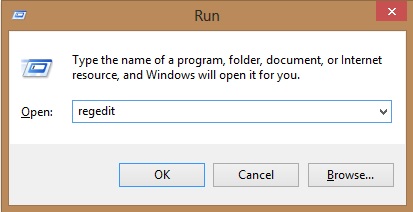
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
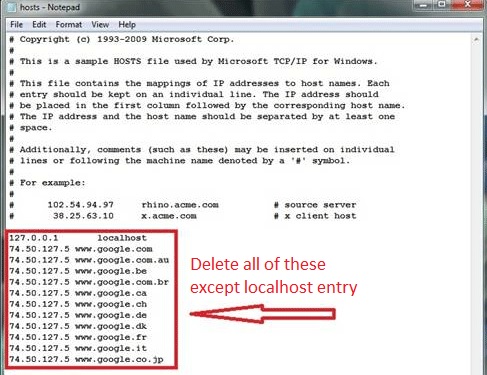
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
STEP 3 : Clean Search.searchipdf2.com traces from Chrome, Firefox and Internet Explorer
-
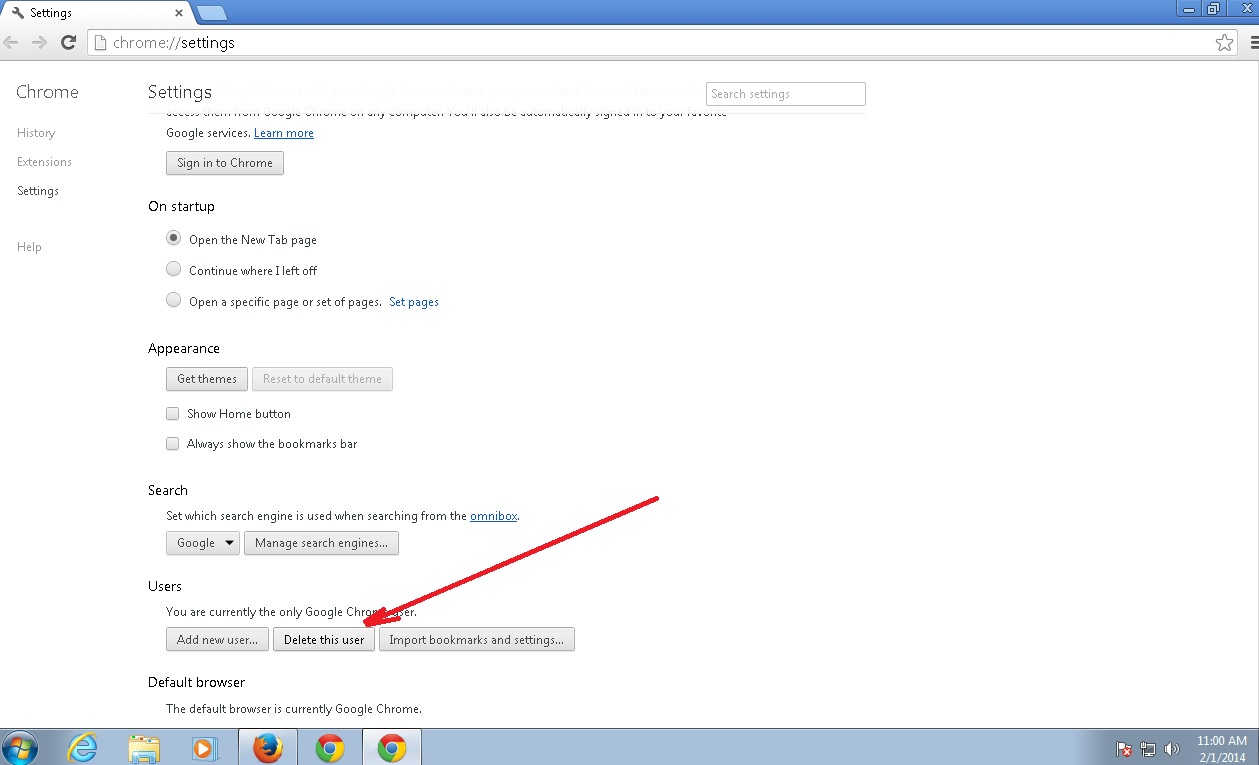
Open Google Chrome
- In the Main Menu, select Tools then Extensions
- Remove the Search.searchipdf2.com by clicking on the little recycle bin
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
-
Open Mozilla Firefox
- Press simultaneously Ctrl+Shift+A
- Disable the unwanted Extension
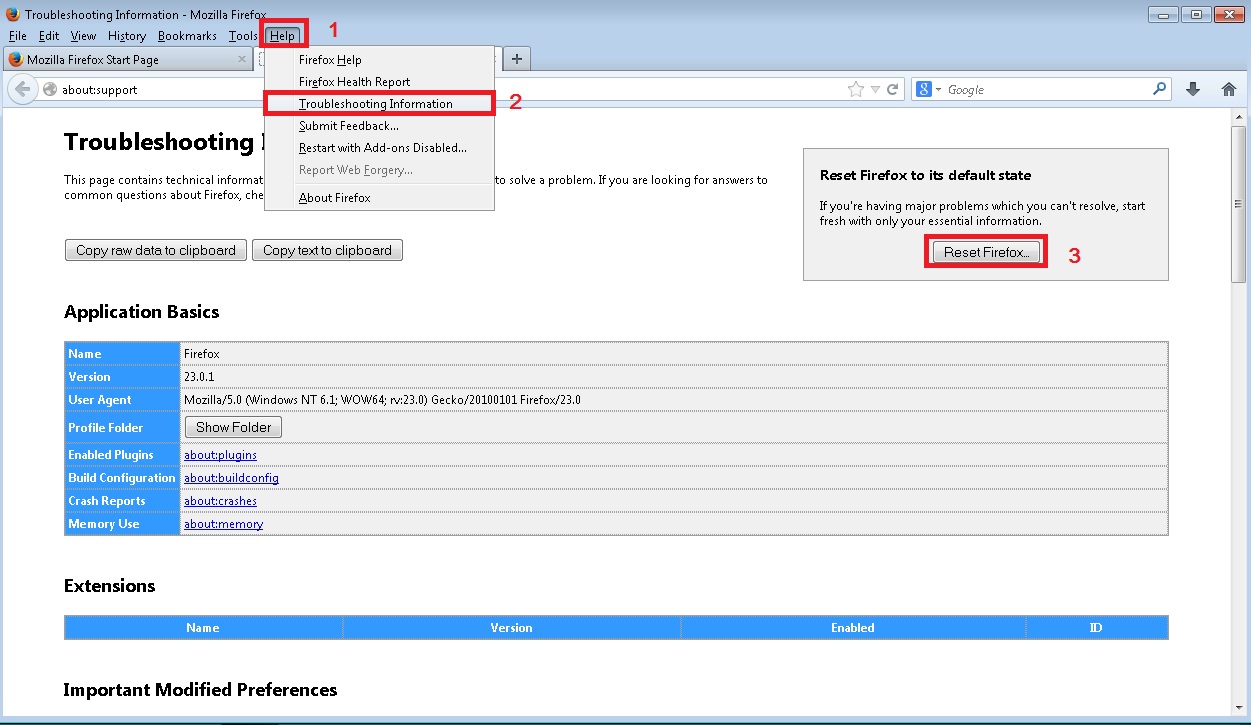
- Go to Help
- Then Troubleshoot information
- Click on Reset Firefox
-
Open Internet Explorer
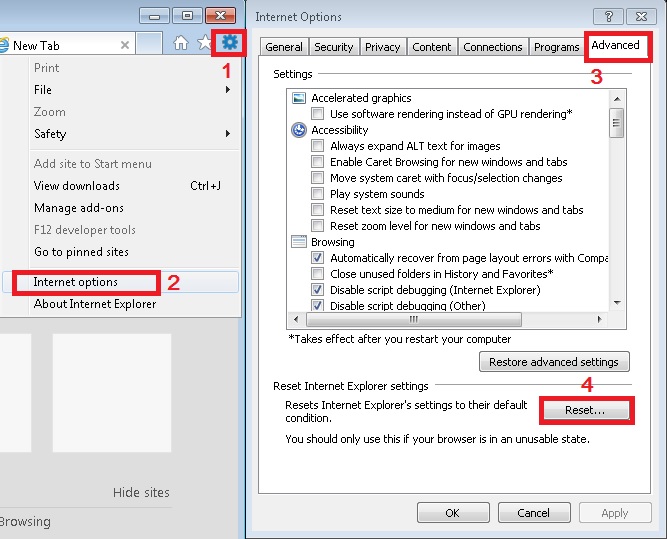
- On the Upper Right Corner Click on the Gear Icon
- Click on Internet options
- go to Toolbars and Extensions and disable the unknown extensions
- Select the Advanced tab and click on Reset
- Restart Internet Explorer
Step 4: Undo the damage done by Search.searchipdf2.com
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Search.searchipdf2.com, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
You must clean all your browser shortcuts as well. To do that you need to
- Right click on the shortcut of your favorite browser and then select properties.
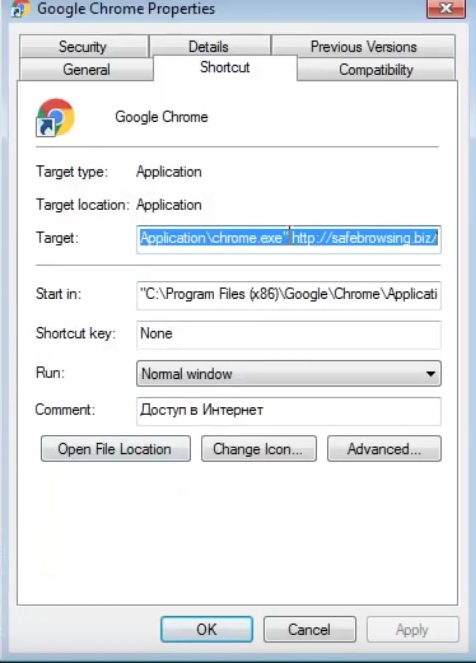
- in the target field remove Search.searchipdf2.com argument and then apply the changes.
- Repeat that with the shortcuts of your other browsers.
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Search.searchipdf2.com Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible registry leftovers or temporary files.