Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RobinHood Ransomware?
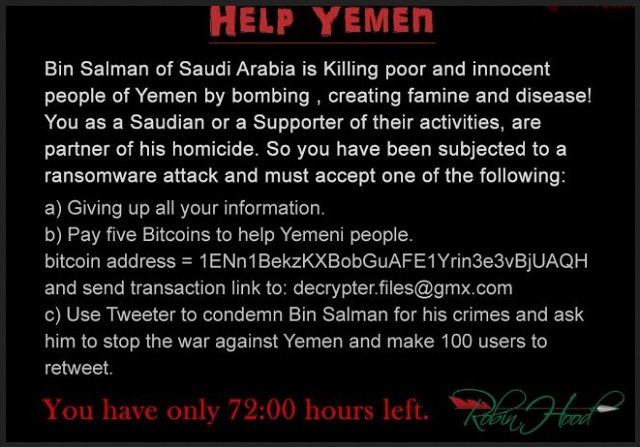
Readers recently started to report the following message being displayed when they boot their computer:
HELP YEMEN
Bin Salman of Saudi Arabia is Killing poor and innocent people of Yemen by bombing , creating famine and disease!
You as a Saudian or a Supporter of their activities, are partner of his homicide. So you have been subjected to a ransomware attack and must accept one of the following:
a) Giving up all your information
b) Pay five Bitcoins to help Yemeni people.
bitcoin address = 1ENn1BelaKXBotiGuAFE1Yrin3e3vBjUAQH
and send transaction link to: decrypter.files@gmx.com
c) Use Tweeter to condemn Bin Selman for his crimes and ask him to stop the war against Yemen and make 100 users to retweet.
The RobinHood Ransomware doesn’t steal from the rich to give to the poor. It steals from gullible PC users to help hackers gain illegal profit online. Even though crooks have chosen quite a curious name for their parasite, that doesn’t make it any less harmful. This program belongs to the most dangerous type of infections currently on the Web. Ransomware. Check out today’s article to know what you’re up against. Remember that there is a reason why this is the most dreaded and feared kind of program. RobinHood Ransomware sneaks itself on board in complete silence. It then scans your PC in order to locate your private files. Yes, all of them. Ransomware goes after various file formats including the most popular ones. That means RobinHood Ransomware targets photos, music, videos, documents, presentations. It successfully finds all your files and uses a string cipher to lock them. It adds a .RobinHood extension and changes the format of your data. Therefore, its new format is unrecognizable by your computer. You can no longer access or use any of the files stored on your machine. Once that is complete, RobinHood Ransomware makes modifications in your desktop wallpaper. The virus drops two files on your desktop – ROBINHOOD -TIMER.exe and READ_IT.txt. This is where it gets interesting. The READ_IT.txt file contains detailed payment instructions. It also claims your computer is infected because you’re a supporter of Bin Salman of Saudi Arabia. You’ve never heard of Bin Salmen? That only comes to show that the noble goal RobinHood Ransomware supposedly has is absolutely bogus. This program isn’t trying to help the people of Yemen. It is solely trying to scam you and steal your money. Now, many ransomware infections demand a sum between 0.5 (1749 USD) and 1.5 Bitcoin (5248 USD). The RobinHood virus asks for the dizzying sum of 5 Bitcoin which equals 17 485 dollars at the moment. Yes, you read that number correctly. You’re supposed to pay for the privilege to use your own files. Apart from the fact this is an extremely unfair deal, it doesn’t really guarantee anything. Hackers are certainly not famous for being honorable people so negotiating with them would be a bad move. The RobinHood Ransomware even provides you a timer thus making the mess greater. You are given 72 hours to pay 17 485 dollars. Otherwise, your encrypted files remain useless forever. As you could imagine, ransomware is using empty promises and bogus threats to get your money. Delete this parasite instead of letting it scam you.
How did I get infected with?
Ransomware uses many different infiltration methods. What they all have in common is that your permission has nothing to do with the installation. In other words, the virus lands on board behind your back. After all, not many people would agree to install a dangerous file-encrypting parasite. That’s why malware applies stealthy techniques and gets downloaded in silence. The easiest way involves spam messages or fake email-attachments. Be careful what you click open because hackers may send infections to your inbox. If they do, it is your responsibility to prevent infiltration. Always watch out for potential viruses and make sure no intruder gets installed. Avoid random third-party pop-up ads as well as unverified websites. Other popular tactics involve bogus software updates and malicious torrents. Ransomware also uses exploit kits to get distributed online. In the future, keep an eye out for dangerous parasites when installing program bundles too.
Why is RobinHood dangerous?
As mentioned already, the RobinHood infection locks your files. It renames them and leaves your data inaccessible and unusable. That means, unless you have backup copies, you’re in trouble. We’d recommend that you always keep backups in case another ransomware pest gets to your device. Don’t make the same mistake again and make sure your files are protected. Also, restrain yourself from following hackers’ malicious instructions. Crooks don’t intend to actually provide you the decryptor promised. Thus, paying would make matters worse and it might even disclose your bank account details. To prevent further damage, ignore the parasite’s aggravating ransom notes. Remember, you’re dealing with a dangerous infection that’s trying to blackmail you. Get rid of the ransomware for good. Please follow our detailed manual removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
RobinHood Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover RobinHood Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with RobinHood encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate RobinHood encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



