Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Protected Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
What happened to your files ?
All of your data has been encrypted
What does this mean ?
The data within your files has been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
Decrypting of your files is only possible with the help of the private key and the decription tool, which is available for a small fee.
What do I do?
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
If you remove this program your data will NOT be decrypted, additionally you will loose the opportunity to ever decrypt your files.
How do I decrypt my files?
To receive the decryption tool and the associated decryption key, you will have to pay a fee of 0.5 BTC (Bitcoin) which is equivalent to around $200.
The fee has to be paid within 7 days. If you fail to pay the fee in time, the decyption key will be destroyed and you will loose your files forever!
How do I get Bitcoin?
There’s several ways to buy Bitcoin, please have a read through one or multiple of the following guides:
https://localbitcoins.com/guides/how-to-buy-bitcoins
https://en.bitcoin.it/wiki/Buying_Bitcoins_%28the_newbie_version%29
Please note: Most of these guides will tell you to create a Bitcoin wallet. You can skip this step and use the provided Bitcoin wallet address below.
You can copy and paste these links into your browser to open the sites.
The fastest way to buy Bitcoin is to use an Bitcoin ATM, Bitcoin ATM’s can be found all over the world, a list / map of Bitcoin ATM’s can be found here:
Bitcoin ATM Map
On some systems this page may take a while to load, please be patient.
When using a Bitcoin ATM we will receive the payment instantly and thus, your files can be decrypted as soon as today!
Where to send the payment to?
Your personal Bitcoin wallet address: –
Please use only this wallet address when making the payment of 0.5 BTC
What happens after the payment?
After you have made the payment, please click the check payment button below. After successful receipt of payment you will receive the decryption tool and associated decryption key.
Thanks, have a lovely day.
Ransomware infections have earned the title ‘worst cyber threat you can catch.’ And, they certainly deserve it. These tools are notoriously invasive and harmful and are designed to put you through cyber hell in the hopes of exploiting you for monetary gain. That’s their end game – getting you to transfer money to them. And, here’s how they do it. After the infection makes its way to your computer and settles, it hardly wastes time before it attacks. The tool’s programming promptly kicks in, and it commences the encryption process. Then, a message is displayed, which informs you of your current state, and demands payment for it to revert to what it was before the infection. And, you’d be surprised how many users give in, and fall victim to the scheme. Hear us loud and clear: Do NOT pay these people! Do NOT allow yourself to become just another victim in the never-ending string of tricked users! These are individuals, who cannot be trusted! They have countless ways to deceive you, and not go through with their end of the bargain. If you pay, you only put yourself into a worse situation. So, don’t. It may seem harsh, but forsake your files because if you choose them, you WILL regret it as you have much more to lose than gain. Pick privacy over data. It’s much more important. Pictures and music can be replaced, can you say the same for your personal and financial details?
How did I get infected with?
Ransomware infections don’t just pop out of the blue one day, and neither did this one. The malicious tool didn’t magically appear. In fact, ransomware programs cannot enter your system unless they gain your permission to do so. In other words, the tool is bound to ask whether you agree to install it on your PC or not and if you deny it – no admittance. But, seeing as how you’re currently plagued by it, evidently, you complied. You are behind its installment. If it weren’t for you, you wouldn’t be in this predicament. However, don’t beat yourself up too hard. These infections are crafty and positively masterful in the arts of deceit. They employ every known trick in the book to dupe you into permitting them in and, at the same time, keep you oblivious to it. Yes, it not only fools you into giving it the green light but also keeps its presence a secret from you until it decides otherwise. And, how do you suppose the cyber threat pulls off that deception? Well, it usually sneaks in undetected by hiding behind freeware or spam email attachments, corrupted links or sites, or by pretending to be a bogus update. If you hadn’t noticed, there is indeed a common denominator between all of these methods. Every means of infiltration relies on your carelessness. So, if you wish to keep your PC infection-free, don’t be careless! Don’t give into distraction, naivety, and haste but, instead, always be vigilant and do your due diligence. Even a little extra caution goes a long, long way.
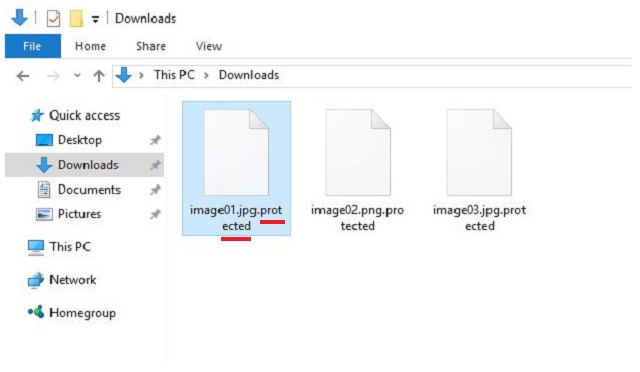
Why is Protected dangerous?
Turning on your computer, and seeing every single file you have stored on it with an added .protected extension is bad news. If that occurs, you are infected. And, not with just any infection. Oh, no! But with ransomware. These tools are immensely hazardous. Once they sneak in and settle, they corrupt your system. Shortly after infiltration, they proceed with the encryption of your data and lock every one of your files. Nothing is beyond its reach, and nothing escapes it. Once it’s done, you’ll find everything renamed and inaccessible. The added extension is like the last nail in the coffin. It renders your pictures, videos, music, documents, and everything else, utterly unreachable. The only way to get them back, and free them from their captor is by applying the decryption key. And, here’s the ringer – to get it, you have to pay up. If you wish to receive the key and decrypt your data, you have to transfer to the kidnappers a sum of 0.5 Bitcoin in seven days’ time or your decryption key is destroyed. Yes, you even have a time limit. 0.5 Bitcoin is roughly around $270. That’s close to $300! It’s no small amount, for sure. But, here’s the deal. Even if it was, indeed, significantly less, even if was just a single dollar, you still mustn’t pay! Refuse to abide by the rules set by malicious people who have an utter disregard for your best interest! You’ll severely regret it if you give in and comply as it will result in an even bigger mess. Consider this. To pay, you must provide these strangers with your personal and financial information, and even if you ignore every other red flag, do not overlook this one. Don’t take chances with these people. It’s not worth th risk. It’s best to lose your files rather than expose your private life to wicked individuals with agendas. Make the wiser choice – don’t pay.
Protected Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Protected Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Protected encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Protected encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



