Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Pizza Crypts Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
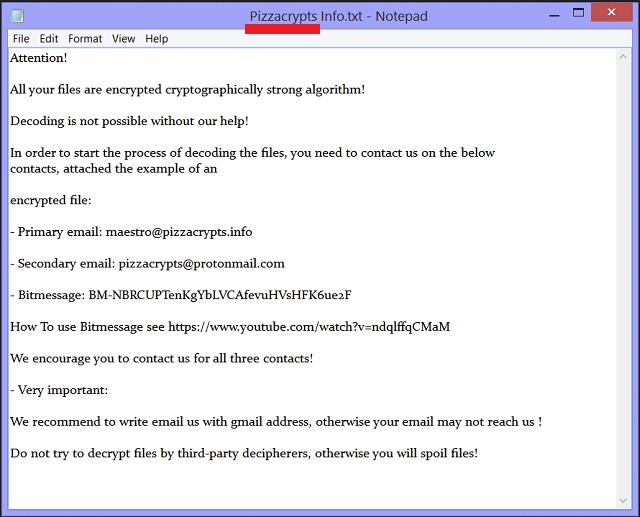
Attention!
All your files are encrypted cryptographically strong algorithm!
Decoding is not possible without our help!
In order to start the process of decoding the files, you need to contact us on the below
contacts, attached the example of an
encrypted file:
– Primary email: maestro@pizzacrypts.info
– Secondary email: pizzacrypts@protonmail.com
– Bitmessage: BM-NBRCUPTenKgYbLVCAfevuHVsHFK6ue2F
How To use Bitmessage see https://www.youtube.com/watch?v=ndqlffqCMaM
We encourage you to contact us for all three contacts!
– Very important:
We recommend to write email us with gmail address, otherwise your email may not reach us !
Do not try to decrypt files by third-party decipherers, otherwise you will spoil files!
Pizza Crypts is part of the ransomware family. That’s, arguably, one of the worst cyber threats you can catch. It’s invasive and a plague on your PC. After it slithers its way in via deception and trickery, its programming kicks in. And, you won’t like it. These infections follow simple instructions. Invade system, encrypt everything, demand ransom for decryption. It’s as simple as that. Once it completes the infiltration stage, the tool places your files on lock-down. It encrypts every single one you have stored on your computer. Pictures, videos, music, etc. Nothing is safe from the application’s reach! It leaves no stone unturned and encrypts your data. Upon completion of the encryption process, you’ll see the added extension .id-[id number]-maestro@pizzacrypts.info to each of your files. Then, it proceeds to stage two. That is, clue you into its presence, and display its demands. They contain a form of monetary payment, usually in Bitcoin. They provide you with the instructions, need to complete the payment, and wait. These people, who corrupted your PC and threatened your privacy, sit and wait. Their program lurks in the background. It’s looming over your personal and financial details, and your data. Once it shows you the requirements, it claims that if you pay up, you’ll receive the decryption key, and free your files. Supposedly, after payment, you rid yourself of the infection. But do you? Do you honestly believe that? Don’t buy a single promise the tool makes! After all, it’s a dangerous cyber threat! It’s a plague on your system! A bane on your browsing! It not only encrypts every single file you have on your PC but also threatens to expose your private life! Oh, yes! Ransomware programs present the risk of your private information getting stolen. And, not just that! But also hand it to strangers with agendas. The question is, are you going to allow that? Here’s a hint: don’t! When faced with the choice data or privacy, pick privacy! It may be the more difficult choice, but it’s the right one. Forsake your files, and protect your personal and financial information. You won’t regret it, and your future self will be grateful.
How did I get infected with?
Pizza Crypts didn’t just show up on your computer as if by magic There’s nothing magical about it. These tools slither in undetected with your help. In reality, they ask for your permission to install themselves. And, if you don’t grant it – no admittance! In other words, you give the infection the green light. But how? How does a cyber threat manage to get your approval, and still enter without you realizing it? Well, it’s pretty straightforward. The tool tricked you. It doesn’t openly pop up, and ask permission. Oh, no. It does it via slyness and subtlety. More often than not, by hiding behind corrupted sites or links. It can also hitch a ride with spam email attachments or freeware. It can even pose as a fake update. For example, you may believe you’re updating your Java or Adobe Flash Player, but you’d be wrong. In actuality, you’re installing a ransomware program. So, if you wish to avoid that, be more thorough and vigilant when installing a tool or an update! Infections prey on carelessness, so don’t provide it! Do your due diligence, and be more cautious. Even a little extra attention goes a long way.
Why is Pizza Crypts dangerous?
Pizza Crypts is horrendous. Once it settles into your system, you’re in trouble. There will be consequences, and you will not like them. As is the case with all ransomware applications, you can’t win. It’s a fight, which you’re bound to lose. No matter which scenario you follow, you won’t come out on top. Let’s explore your options. First, the most obvious one, you comply. Say, you decide to follow the captors’ demands. You pay the ransom and patiently await the decryption code. What do you expect will happen? In a perfect world, you receive the key. Then decrypt your data, move on, and forget about the entire experience. However, we don’t live in a perfect world. There are several ways the exchange can go down. One, you pay and receive the key. But when you try to apply it, it doesn’t work. Your files are still locked. Only, now, you’ve lost money and exposed your private life to strangers. That’s no good. Two, you apply the key, and it works! You release your files from the captors’ clutches. You justify the payment and go on with your day. But, what’s to stop the kidnappers from forcing you back to square one? Nothing. There are no guarantees that the program won’t activate again the very next day. Even though, you’ve paid and decrypted everything. And, then what? You find yourself with less money, encrypted data, and exposed privacy. That scenario is somehow worse than the previous one. Whichever way you look at it, you lose! So, don’t play the game at all! As unlikely as it may seem, that’s your best option. It’s the best course of action you can take. How come? Well, while you do lose your data, at least, you protect your private information. And, don’t you think privacy is more important than pictures?
Pizza Crypts Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Pizza Crypts Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Pizza Crypts encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Pizza Crypts encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



