Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Parisher Ransomware?
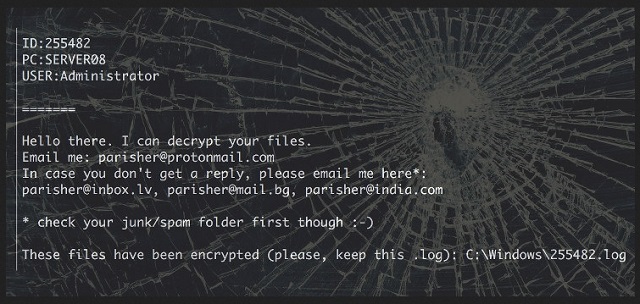
Readers recently started to report the following message being displayed when they boot their computer:
ID:[6 digit number]
PC:[name of the machine]
USER:Administrator
=========
Hello there. I can decrypt your files.
Email me: parisher@protonmail.com
In case you don’t get a reply, please email me here*:
parisher@inbox.lv, parisher@mail.bg, parisher@india.com
* check your junk/spam folder first though 🙂
These files have been encrypted (please, keep this .log): C:\Windows\[6 digit number].log
Parisher belongs to the worst category of cyber threats – ransomware. Why would ransomware be the worst, you wonder? Well, these infections have certainly earned their reputation. They slither into your system cloaked. And, once inside, proceed to corrupt it. They target your data, take it hostage, and extort you. They follow a standard programming. Invade. Encrypt. Extort. Parisher does not differ from that programming. After the tool sneaks into your PC undetected, it doesn’t waste much time. It goes to work. And, all of a sudden, you find your files locked. There’s an unknown extension at the end of each picture, video, document, etc. You can’t open any of them. And, moving or renaming them does nothing. Then you see the note. The ransomware left you a ransom note. It reads that your data got encrypted, and you have to pay up if you want to decrypt it. Only after, you complete the payment, will you get the decryption key you need to unlock your files. But, here’s the thing. Even if you ignore everything else, all the signs and red flags, think of this. The people behind Parisher are strangers. They unleashed a dangerous tool onto unsuspecting web users. They programmed it to target your data, and extort you for monetary gain. Unknown individuals with malicious, self-serving interests. Do you truly think these people will keep their word? That they’ll keep their end of the bargain? That, somehow, the exchange will go smoothly, and they’ll keep their promises? Don’t be naive! Don’t fool yourself! These are shady, wicked people, and you can’t trust them! Do NOT pay! Following their demands only worsens your predicament. By paying, you jeopardize your private life. Do yourself a favor, and cut your losses. As difficult as it may seem, say goodbye to your data. Pictures aren’t worth your privacy.
How did I get infected with?
Parisher seems to pop up one day on your PC as if by magic. You have no idea how it got there, and why you’re just seeing it now, after the damage is done. Well, it’s your fault. You’re to blame. Let’s elaborate. Ransomware tools enter by exploiting the user and the user’s carelessness. Your carelessness. The tool attaches itself to a spam email, and waits for you to click on it, download it, open it, etc. There are plenty of ways to allow it into your system. Like, hiding behind corrupted links or sites. Or, freeware. Or, pretending to be a fake system or program update. Like, Java or Adobe Flash Player. Whichever method the sneaky infection uses, it needs one thing. A key ingredient to a successful invasion. It cannot succeed without your carelessness. Parisher, like most cyber threats, preys on your distraction. It needs your naivety and haste. Don’t make it easier for the tool to invade your PC! Be extra thorough! Always take your time to read the terms and conditions before agreeing to anything. Sometimes even a little extra caution can save you a ton of troubles. Be cautious. Be attentive. Don’t rush.
Why is Parisher dangerous?
Parisher gets its name from the email addresses it provides you with in the note. We mean the ransom note, you receive after encryption. It’s a TXT file called 1NFORMATI1ONFOR.YOU or HELLO.0MG. And, it’s rather basic. It leaves one main email, which you need to contact – parisher@protonmail.com. And, gives three other ones as back-up options – parisher@inbox.lv, parisher@mail.bg, parisher@india.com. Supposedly, that’s how you get in touch with the extortionists. And, then they give you further instructions. But they’re always the same with each ransomware tool. Pay us in Bitcoin, and use the following address to do so. Parisher demands a ransom of 5 Bitcoin. Now, a single Bitcoin fluctuates between 500 and 600 US Dollars. So, it’s no small amount. But, even if it was, you still shouldn’t pay! Why? Well, think about it. If you go through the transfer process, you leave private information. Information, which the people behind Parisher can get a hold of. We’re talking your personal and financial data falling into the hands of extortionists! Do you think that’s a good idea? That it will end well for you? Don’t fool yourself. Yes, losing all your files is terrible. But it doesn’t compare to losing your private life to these people. Don’t let that happen. Don’t comply. Don’t pay. Choose the lesser evil, and forsake your data. It can be replaced. Can you say the same about your privacy?
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Parisher Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Parisher Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Parisher encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Parisher encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



