Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Money Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
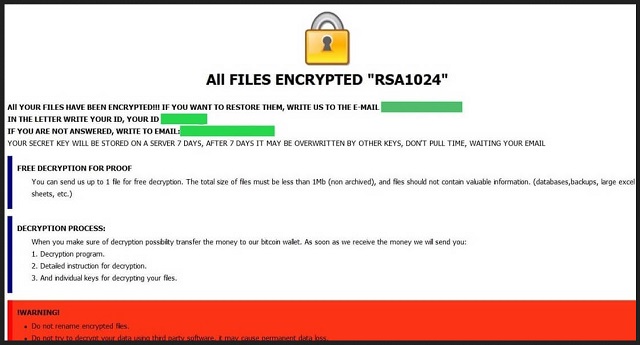
All FILES ENCRYPTED “RSA1024”
All YOUR FILES HAVE BEEN ENCRYPTED!!! IF YOU WANT TO RESTORE THEM, WRITE US TO THE E-MAIL cmdroot@airmail.cc
IN THE LETTER WRITE YOUR ID, YOUR ID 1E857D00
IF YOU ARE NOT ANSWERED, WRITE TO EMAIL:cmdroot@airmail.cc
YOUR SECRET KEY WILL BE STORED ON A SERVER 7 DAYS, AFTER 7 DAYS IT MAY BE OVERWRITTEN BY OTHER KEYS, DON’T PULL TIME, WAITING YOUR EMAIL
FREE DECRYPTION FOR PROOF
You can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
DECRYPTION PROCESS:
When you make sure of decryption possibility transfer the money to our bitcoin wallet. As soon as we receive the money we will send you:
1. Decryption program.
2. Detailed instruction for decryption.
3. And individual keys for decrypting your files.
!WARNING!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Money is a malicious ransomware threat. It belongs to the Dharma (CrySis) family. It’s hazardous and harmful, and an utter plague on your PC. It invades via trickery, then spreads its corruption throughout. The tool uses strong encryption algorithms to take your data hostage. And, then, extorts you for monetary gain. Don’t allow the nasty threat to profit off of your fear and gullibility! Understand that you’re dealing with an opponent that has rigged the game against you. And, you’re set up to lose. So, the best thing you can do, would be not to play at all. The infection tries to convince you, that your only option, is to comply. It claims that if you follow its instructions, and pay the ransom, you’ll get the key you need. The decryption key that unlocks your data. But you have to realize that you have NO guarantees that will happen. All, you have to go on, is the word of cyber kidnappers, extorting you for money. And, these are hardly trustworthy individuals. To trust them, is a mistake. Don’t make it. Don’t pay them. Don’t contact them. Don’t reach out in any way. Compliance is not the way to go.
How did I get infected with?
Infections, like the Money one, invade via deception. They resort to every known trick in the book to try to slip past you, unnoticed. There’s an array of methods, they can resort to, that assist with their attempts. For example, the tool can lurk behind corrupted links, sites or torrents. It can use freeware and spam emails. And, it can pretend to be a bogus system or program update. These methods may seem prolific, but they share a common denominator. Neither one can prove successful, without your assistance. That’s right. The infection needs your carelessness, when it comes to invading your system. It needs you to rush, and throw caution to the wind. To give into naivety, and not bother doing due diligence. Don’t oblige! Don’t leave your fate to chance, and ease the infection’s infiltration! Take the opposite approach, and be extra careful. Always be attentive and thorough. And, remember that caution allows you to keep infections pout. And, carelessness invites them in. Make the right choice.

Why is Money dangerous?
The infection uses the ‘.money‘ extension to lock your data. Alongside a unique identifier number. It attaches these at the end of each file, you keep on your computer. That includes, documents, archives, videos, music, and photos. Say, you have a pictures called ‘dog.jpg.‘ After the infection finishes with it, it becomes ‘dog.jpg.id-1E857D00.[cmdroot@airmail.cc].money.’ Once the extension gets appended, that’s it. Your files are no longer accessible. And, the only way to change that, and regain control, is to pay up. The infection demands a ransom in Bitcoin. The Money threat claims that, once it receives your payment, you’ll get the key you need. But what if you don’t? What if you pay the price, and get nothing in return? Or, do get a key, but it proves useless, and your files remain locked? These are actual possibilities. After all, you’re dealing with strangers with malicious intentions. You can’t trust them to keep their word. Also, think about it. Even if you do get the right decryption key, and free your files, what then? Yes, you remove the encryption, but the tool that forces it on you, remains. So, what’s to stop it from doing it again? The Money ransomware can strike a mere minute after you apply the key, and unlock your data. Then, you’re back to square one. Only this time, you have less money. Don’t waste your time, energy and resources dealing with these people. Complying with cyber extortionists is ill-advised, to say the least. Don’t do it.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Money Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Money Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Money encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Money encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.