Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Mole03 Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
!_! INFORAMTIONS !_!
All of your files are encrypted with RSA_2048 and AES_128 ciphers.
More information about the RSA and AES can be found here:
URL1: https://en.wikipedia.org/wiki/RSA_numbers
URL2: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting your files is only possible with
he private key and decrypts program, which is on our secret server.
Follow these steps:
1. Download and install Tor Browsers: https://www.torproject.org/download/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar:
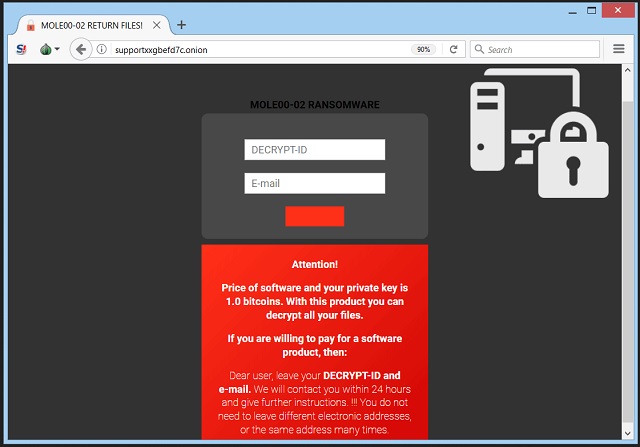
URL1: http://supportxxgbefd7c.onion/
URL2: http://supportjy2xvvdmx.onion/
4. Follow the instructions on the site.
!_! Your DECRYPT-ID: XXXXXXXX-XXXX-XXX-XXXXXX-XXXXXXXXXXXXX !_!
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Mole03 program belongs to the ransomware category. It’s an updated version of the Mole ransomware, based on the CryptoMix infection. The tool uses trickery to slither into your system. Then, once inside, takes over and corrupts it. The infection uses RSA and AES encryption algorithms to lock your data. Once under lock down, you can no longer access it. The tool even attaches a special extension at the end of each file, to solidify its grip. Pictures, documents, videos, music. All of it has the ‘.mole03’ appended at the end. After the extension is in place, and your files locked, you see a ransom note. It’s called ‘_HELP_INSTRUCTION.TXT,‘ and it’s pretty standard. It explains your situation, and provides instructions. If you wish to decrypt your data, yo have to pay a ransom. It has to be in Bitcoin, and only after payment gets made, will you receive a key. Apply that key, and your files get unlocked. It seems simple, right? Well, wrong. There’s more to it than meets the eye. Heed experts’ advice, and do NOT comply! Compliance only worsens your predicament. It’s NOT worth the risk to even reach out to these extortionists, let alone, give them money. It seems harsh, but it’s the right thing to do. A fight against a ransomware is a fight you will lose. It’s a matter of cutting down your losses. Which do you prefer? Losing all your data? Or, losing your data, as well as your personal and financial information? Don’t play the infection’s game. Forsake your files in the name of your privacy. One is replaceable. The other is not.
How did I get infected with?
Mole03 turns to trickery to invade. Victims tend to get duped into inviting it inside, themselves. The ransomware uses a bogus font pretense to sneak in. The tool tries to convince you that you need a special font. Supposedly, Google Chrome needs it, if it’s to display certain websites. The fake font is found in a corrupted executable file. It’s called ‘2017-07-23-1st-run-Font_Chrome.exe.‘ If you choose to trust it, and run it, you’re in trouble. To download and install it, is to allow the Mole03 ransomware into your PC. When you run the file, you see a notification with the name ‘Display Color Calibration.‘ The exact text is: ‘Display Color Calibration can’t turn off Windows calibration management. Access is Denied.’ Its appearance triggers a User Account Control notification. And, asks you to allow the WMI Command Line Utility to run. If you press OK, you give the green light to the Mole03 infection. And, it’s free to attack. Of course, that’s not the only invasive method. The ransomware can also use the old but gold ones. Like, spam e-mails, freeware, corrupted links, fake updates. Always be cautious, and take the time to do your due diligence. It goes a long way.
Why is Mole03 dangerous?
It’s quite the poor decision to comply with the data kidnappers. The people behind Mole03, are hardly trustworthy. They’re malicious cyber criminals. Not the kind of individuals, you can rely on to keep their word. The odds are not in your favor. They WILL double-cross you. Say, you decide to pay the ransom. You transfer the requested sum, and wait. Well, what if they don’t send you the decryption key, they promised? That’s a valid possibility. They ca send you nothing. Or, even a key that doesn’t work. Understand, you have ZERO guarantees when it comes to dealing with ransomware. You rely on their promise to hold their end of the bargain. That’s foolish and naive. But, even if they do provide you with the proper key, what then? You remove the encryption, and free your files, but for how long? The decryption key removes only the encryption. The ransomware remains. It still lurks on your PC, ready to strike once more. And, even that’s not the biggest reason why compliance is a no-no. If you pay the ransom, you leave private details for the infection to find. You provide your personal and financial information. The extortionists can then steal, and exploit it for their malicious agendas. Do NOT allow that. It’s better to lose your data, and keep your private life private. Rather than lose both. Make the tough, but wise call. Discard your data.
Mole03 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Mole03 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Mole03 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Mole03 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



