Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Mischa Ransomware?
Readers recently start to report the following message being displayed when they boot their computer:
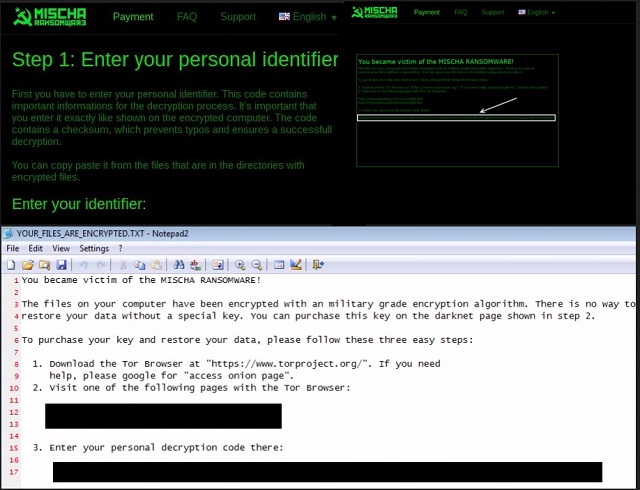
You became victim of the MISCHA RANSOMWARE!
The files on your computer have been encrypted with an military grade encryption algorithm. There is no way to
restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download the Tor Browser at “https://www.torproject.org/”. If you need
help, please google for “access onion page”.
2. Visit one of the following pages with the Tor Browser:
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
http://mischapuk6hyrn72.onion/1MZKMy
http://mischa5xyix2mrhd.onion/1MZKMy
Do you remember Petya ransomware? This pest gained immense popularity for all the wrong reasons last month and it managed to cause many PC users a headache. Well, Petya’s developers enriched the Web with yet another vicious ransomware infection. Meet Mischa. This brand new parasite doesn’t lock the target computer like Petya does but it is incredibly efficient when it comes to locking files. After all, that’s the reason ransomware-type programs get developed in the first place – to extort money from gullible people by blackmailing them. As you could imagine, it’s very difficult to remain calm when all your personal files get encrypted. Unfortunately, a lot of people would panic seeing such sudden, unauthorized modifications on their machines. This is what ransomware relies on. Giving into your panic and anxiety might easily cost you a hefty sum of money. Hackers are aiming directly at your bank account so make no mistake. If you get stuck with Mischa ransomware, remember that panicking would not fix the issue. Immediate, adequate action will. Now, how does this program work? It begins by creating and launching a malicious executable. Your entire PC system gets thoroughly scanned afterwards so the parasite could locate your personal information. That includes a great variety of file formats such as .mp3, .mp4, .jpg, .jpeg, .pdf, .gif, .txt, .doc, .docx, .xls, .wmv, .ppt, .odt .zip, .rar, .bin, etc. Clearly, a huge percentage of your private data gets modified and, eventually, locked. Mischa ransomware uses the AES-265 and RSA encrypting algorithm. And yes, it’s effective. All files modified by the parasite receive a random file extension which replaces the original one. Mischa ransomware adds .cRh8, .3P7m, .aRpt, .eQTz or .3RNu appendixes. If you notice files with some of the aforementioned extensions, you should know you’re in serious trouble. Why? Because your computer is unable to recognize this new file format. Respectfully, you’re unable to use your own data. Mischa ransomware practically denies you access to anything of value you might have stored on your machine – music, pictures, videos, MS Office documents, etc. Now that your files are unreadable and inaccessible, the parasite drops YOUR_FILES_ARE_ENCRYPTED .txt and .html files. You will find these files in all folders that contain encrypted data because they give you detailed payment instructions. At the end of the day, Mischa ransomware revolves solely around money. According to these aggravating ransom notes, “the files on your computer have been encrypted with an military grade encryption algorithm”. However, the situation is about to get worse. You’re supposed to pay 1.9 Bitcoin as hackers promise you a highly questionable decryption key. For those of you who aren’t familiar with online currency, that equals about 860 (!!) USD. The problem is, you’re probably going to receive nothing in exchange for your money.
How did I get infected with?
Mischa ransomware mainly travels the Web via spam email-attachments or spam messages. You might think you’re opening a perfectly legitimate email from a shipping company, for example. In reality, though, you’re installing a ransomware. Keep your curiosity under control when you come across such questionable emails. The Web is infested with malware and cyber criminals are impressively creative when it comes to virus distribution methods. Other popular infiltration techniques include fake job applications, fake torrents, corrupted web links, malicious websites, freeware/shareware bundles, etc. Stay away from anything you don’t trust online because all you need is a single careless click to seriously compromise your machine. Preventing virus installation is a much less challenging task than removing a parasite later on. Do the right thing concerning your safety and be cautious while browsing the Internet.
Why is Mischa dangerous?
Mischa ransomware belongs to one of the most dreaded types of infections out there. Yes, you’ve gotten yourself stuck with a notoriously harmful, resourceful and problematic program. Its one goal is to scam you, and ultimately, to steal about 860 USD of yours. Of course, hackers could always increase the sum demanded. The parasite’s ransom message also contains links to TOR websites which you’re supposed to use in order to complete the payment. Many other ransomware infections (Locky, Cerber) work the same way. As mentioned already, it’s extremely important that you restrain yourself from giving your money away. Paying guarantees you nothing. Keep in mind that you’d be making a deal with greedy, dishonest cyber criminals who rarely follow the rules. Don’t allow crooks to involve you in their fraudulent trickery. Instead, get rid of the virus. To delete Mischa ransomware manually, please follow the detailed removal guide you’ll find down below.
Mischa Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Mischa Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Mischa encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Mischa encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



