Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Master Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
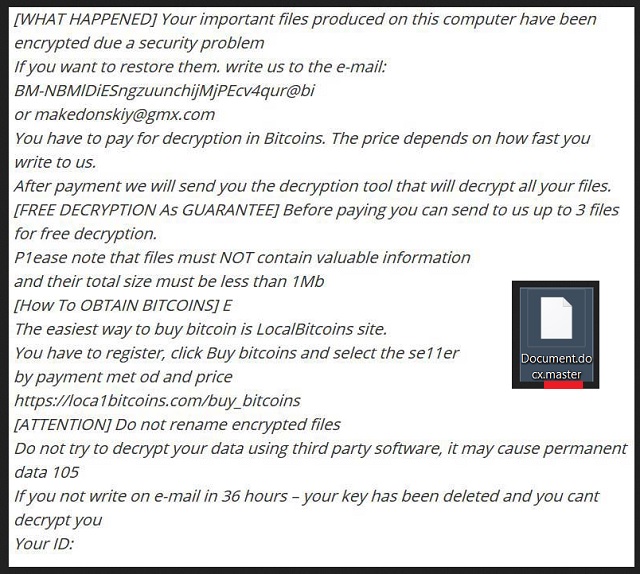
[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due to a security problem
If you want to restore them, write us to the email: BM-NBM1DiE52wgzUUnzcRPwjMjPEcV4qfpr@bitmessage.ch or makedonskiy@gmx.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
You’re stuck with a new version of the BTCWare Ransomware. It goes without saying that your situation is a rather problematic one as ransomware is notoriously dreaded. These file-encrypting pests sneak onto the victim’s device and lock their files. Yes, all their files. That is what the Master Ransomware does too. Being a typical ransomware infection, this program follows the classic rules. It firstly needs your permission to land on board. However, you don’t necessarily have to know that you’re giving your permission. Ransomware is famous for being stealthy so it mainly uses secretive tactics. To learn how this nuisance managed to get downloaded, please keep on reading. The Master Ransomware initiates a thorough scan of your machine. By doing so, it locates all files that it’s about to encrypt. Consider all your data locked because ransomware is immensely aggressive. It goes after a huge variety of file formats including the most popular ones. Your pictures, music, MS Office documents, videos, etc. all fall victims to the virus. In fact, you’ll notice right away which files are encrypted. If you come across the “.master” extension, know that your data is locked. The parasite successfully denies you access to your very own private information. If you thought that was nasty, wait till you hear the rest of it. Not only does the Master Ransomware lock your files. It also demands that you pay a certain sum of money in Bitcoins. You see, while encrypting your data, the parasite drops ransom notes. The ‘!#_RESTORE_FILES_#!.inf’ file is now placed on your desktop. Your desktop wallpaper might get modified as well. Hackers are bombarding you with the ransom messages for one very simple reason. They are trying to trick you into buying a special decryption key. What you have to keep in mind is that paying the ransom would be a terrible mistake. Restrain yourself from giving crooks your money. Ignore their empty promises and bogus threats. If anything, paying for the decryptor would make matter worse because hackers would get access to some personal details. Trust us when we say, this poses an enormous threat to your further safety and privacy. Ransomware is nothing but a clever way for crooks to blackmail you. They are taking advantage of the fact you’d be anxious and upset seeing your files locked out of the blue. Do not give into despair, though, Paying the ransom isn’t how you’d restore your data.
How did I get infected with?
Most ransomware infections travel the Web via fake emails. For instance, the virus pretends to be a job application or an email from a shipping company. Even though hackers make them believable, you should know better than to click such devious emails open. It only takes one single moment of distraction and haste to compromise your safety. Removing a cyber intruder, on the other hand, takes much more time and energy. In order to save yourself the hassle, be cautious. You definitely won’t regret paying attention. If you receive some email-attachment or a message in social media that you don’t trust, just delete it. Remember, there might be a whole bunch of parasites hidden there. Preventing malware installation is your job and yours only. Another popular technique involves exploit kits. The parasite might even get some help from a sneaky Trojan. Also, ransomware often uses fake torrents and bogus program updates to get distributed online. Always keep an eye out for potential intruders. Avoid unverified websites as well and keep your machine safe.
Why is Master dangerous?
The ransomware uses a complicated cipher. Thanks to this strong algorithm, your data ends up inaccessible. You’re no longer able to open, view or use your very own files. To make the mess even greater, the Master Ransomware covers your PC screen with ransom notes. This pest of a program attempts to convince you that you need to make a payment. Hackers offer you a deal. According to the ransom messages, they will provide you a decryptor after you pay. The demanded sum is in Bitcoins and is usually quite a large one. Unfortunately, paying it doesn’t guarantee hackers will keep their end of the bargain. Instead of freeing your encrypted data, crooks might not send you the decryption key you were promised. After all, ransomware’s only purpose is to help crooks gain illegal revenue. Helping you out isn’t even part of the picture. Keep your Bitcoins and get rid of the infection ASAP. To do so manually, please follow our detailed removal guide down below.
Master Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Master Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Master encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Master encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



