Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Diablo6 Ransomware?
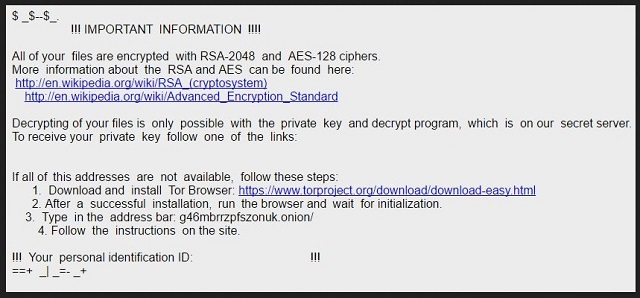
Readers recently started to report the following message being displayed when they boot their computer:
!!! IMPORTANT INFORMATION !!!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
http://en.wildpedia.org/wiki/RSA_(cryptosystem)
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
To receive your private key follow one of the links:
If all of this addresses are not available, follow these steps:
1. Download and install Tor Browser: https://www.torproject.org/downIoad/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: g46mbrrzpfszonuk.onion
4. Follow the instructions on the site.
!!! Your personal identification ID: !!!
Diablo6 is an inheritor of the dreaded Locky Ransomware. It has nothing to do with the Diablo video game or the El Diablo comics character. As mentioned, it has a lot to do with Locky – one of the most destructive and harmful infections out there. This is its newest variant. Just knowing that this pest is associated with Locky should make you realize how bad things are. The Diablo6 Ransomware works as a typical file-encrypting infection. It uses a combination of AES-128 and RSA-2048 ciphers to lock your files. Yes, all your files. That includes all your personal data such as photos, music, videos, presentations, documents. Most PC users store some immensely valuable files on their machines. It goes without saying that would be a mistake because you become a target for ransomware. These programs lock information and take advantage of your panic. However, if you have backup copies of your files, there’s going to be no panic. In the future always keep copies of your precious data so you don’t have to deal with ransomware again. The Diablo6 parasite firstly scans your PC searching for files to encrypt. Then it begins to lock your favorite pictures, important work-related documents and other files. It gets ugly before you even realize something has invaded your device. Ransomware is considered to be the worst kind of virus out there. Its malicious glory is perfectly deserved, as you can see. Diablo6 renames the target files. It replaces their original names with a combination of characters and adds the .diablo6 extension. As soon as you notice this extension, know your information is no longer accessible. The virus is now holding your files hostage for one very simple reason. Money. This program’s developers are aiming for illegal profit and ransomware offers an effective scheme. It uses a strong algorithm to lock your valuable, perhaps even irreplaceable data. Then it drops detailed payment instructions in all folders that contain encrypted information. You’ve already noticed that your desktop wallpaper has been modified as well. The aggravating diablo6.html and diablo6.bmp files inform you about the situation. They also try to convince you to pay for a certain decryption key. What you have to keep in mind is to ignore this infection’s ransom messages. The very last thing hackers are interested in is letting your files free. Instead, crooks focus on scamming you and stealing a hefty sum of your money in Bitcoin.
How did I get infected with?
The virus gets downloaded as a .zip email-attachment. How did it manage to land on your machine behind your back? It actually applies an incredibly simple technique. Hackers often disguise the infection as a perfectly safe email or message. They rely on the fact you’d be curious enough to click it open. If you do, you let loose the pile of viruses that may be hiding in the fake email. Remember to delete anything you receive in your inbox that you don’t trust. Watch out for bogus job applications or spam messages from unknown intruders. Ransomware might also pretend to be sent from shipping companies. Keep an eye out for potential intruders. Make sure no infection gets to your machine because you’re the one who will have to fight it afterwards. Save yourself the hassle that is removing malware. In addition, the virus might have used a fake program update or a malicious torrent to land on board. Those usually provide a convenient virus infiltration tactic. Stay away from illegitimate websites, third-party pop-up ads and unverified program bundles as well. Last but not least, check out your PC for more infections. The ransomware could be having some malicious company from a Trojan horse, for example.
Why is Diablo6 dangerous?
This cyber virus asks for 0.5 Bitcoin in exchange for a decryptor. That equals 2104 USD at the moment. Furthermore, paying doesn’t guarantee you anything because hackers don’t tend to play by the rules. Especially the rules that involve money. Giving your Bitcoin away would automatically make matters worse as crooks would get access to your bank account data. Not to mention, you’d lose about 2000 dollars. Cyber criminals are certainly not the people to make negotiations with so don’t let them scam you. Buying their decryption key isn’t the way to regain access to your encrypted files. Thus, don’t become a sponsor of greedy crooks and ignore their ransom notes. To delete the ransomware manually, please follow our detailed removal guide down below.
Diablo6 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Diablo6 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Diablo6 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Diablo6 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



