Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Krypte Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
Krypte Ransomware
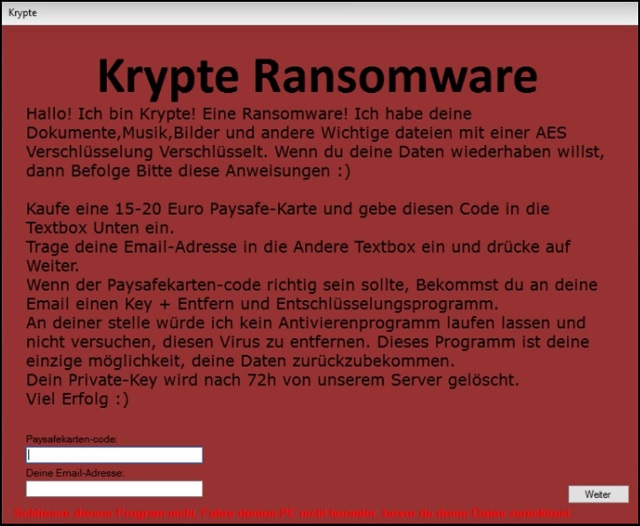
Hallo! Ich bin Krypte! Eine Ransomware! Ich habe deine Dokumente,Musik,Bilder und andere Wichtige dateien mit einer AES Verschlüsselung Verschlüsselt. Wenn du deine Daten wiederhaben willst, dann Befolge Bitte diese Anweisungen 🙂
Kaufe eine 15-20 Euro Paysafe-Karte und gebe diesen Code in die Textbox Unten ein. Trage deine Email-Adresse in die Andere Textbox ein und drücke auf Weiter. Wenn der Paysafekarten-code richtig sein sollte, Bekommst du an deine Email einen Key + Entfern und Entschlüsselungsprogramm. An deiner stelle würde ich kein Antivierenprogramm laufen lassen und nicht versuchen, diesen Virus zu entfernen. Dieses Programm ist deine einzige möglichkeit, deine Daten zurückzubekommen. Dein Private-Key wird nach 72h von unserem Server gelöscht. Viel Erfolg 🙂
This is a brand new German version of the Razy Ransomware. Now, when it comes to ransomware, most viruses follow the classic pattern. If you’ve seen one infection, you’ve seen them all. The Krypte Virus, for example, works the exact same way hundreds of programs do. This is a typical file-encrypting parasite. It starts wreaking havoc as soon as it lands on board and gets out of hand very quickly. Krypte starts with performing a thorough scan on the PC system. As a result, the ransomware locates all your personal files. We’re talking pictures, music, MS Office documents, videos, presentations, etc. You know what happens next, don’t you? Encryption begins. Krypte Ransomware uses the strong AES encrypting cipher. Whatever it locks, remains locked. That includes .jpeg, .jpg, .pdf, .txt, .docx, .ppt, .xls and many more file formats. Ransomware is a particularly nasty PC infection. Some researchers even go so far as to say this is the most destructive kind of virus online. As already mentioned, Krypte denies you access to your own personal files. It renames the target data and adds a .fear extension. The minute you spot this extension, know you’re in trouble. The .fear appendix only means one thing – your files are inaccessible. By changing their format, Krypte makes your data unreadable. You won’t be able to view or use your precious information. It goes without saying you might have stored very important data on board. Do you know why this program locks your files? Because ransomware aims at your bank account. In order to scam you, the virus needs to lie to you first. This is where encryption comes in handy. It’s all part of crooks’ scheme to blackmail you. Now, Krypte Ransomware uses its complicated algorithm to lock your files. These modifications are completely unauthorized and out of the blue. Then the virus starts forcing a ransom note on you. While encrypting your data, this program creates .txt files and modifies your desktop wallpaper. You now see payment instructions everywhere. The ransom message itself is in German and it offers you a deal. According to this note, you have to buy a 15-20 euros Paysafe card. In exchange for its code, you will receive a decryptor. Or so hackers claim. Do you think making a deal with cyber criminals is a good idea? It’s a terrible one and you know it.
How did I get infected with?
The oldest infiltration method out there is spam messages. However, it’s also the most effective technique at the moment. Ransomware usually travels the Web as a corrupted email or some spam email-attachment. Crooks rely on the fact that many people open everything they receive in the inbox. That’s a crucial mistake because you might set some vicious parasite free. Ransomware pretends to be legitimate mail from a shipping company, for instance. It may claim to be a perfectly harmless job application too. Be careful what you click open and watch out for malware. Also, keep in mind that illegitimate torrents/software bundles are often malicious. Stay away from third-party pop-up ads as well. As if that wasn’t enough, ransomware might pretend to be a program update. It also travels the Web with the help of a Trojan horse. There’s a rich variety of installation methods so you can’t afford a single moment of haste. Be cautious online and don’t take unnecessary chances.
Why is Krypte dangerous?
You only have 72 hours to complete the payment. Unless you pay the money demanded on time, hackers will destroy your decryptor. Does that seem like a fair deal to you? It’s a nasty attempt for a cyber fraud. Yes, crooks are trying to blackmail you. Their ultimate goal is to steal your money so don’t let them scam you. If you pay the ransom, you fall straight into hackers’ trap. This might cost you quite a lot of money. You should never negotiate with cyber criminals. In fact, even if you pay the entire ransom, you may still receive nothing. Following instructions doesn’t guarantee you that crooks will keep their end of the bargain. As mentioned, this is just an attempt for a fraud. Helping you restore your encrypted files was never hackers’ goal. Paying the ransom should never be yours. To delete this pest manually, please follow our removal guide down below.
Krypte Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Krypte Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Krypte encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Krypte encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



