Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Kostya Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
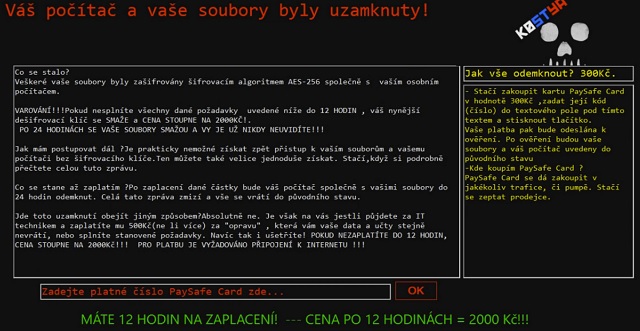
Co se stalo?
Veškeré vaše soubory byly zašifrovány šifrovacím algoritmem AES-256 společně s vaším osobním počítačem.
VAROVÁNÍ!!!Pokud nesplníte všechny dané požadavky uvedené níže do 12 HODIN , váš nynější dešifrovací klíč se SMAŽE a CENA STOUPNE NA 2000KČ!.
PO 24 HODINÁCH SE VAŠE SOUBORY SMAŽOU A VY JE UŽ NIKDY NEUVIDÍTE!!!
[…]
Jak vše odemknout? 300Kč.
– Stačí zakoupit kartu PaySafe Card v hodnotě 300Kč ,zadat její kód(číslo) do textového pole pod tímto textem a stisknout tlačítko.
Vaše platba pak bude odeslána k ověření. Po ověření budou vaše soubory a váš počítač uvedeny do původního stavu
-Kde koupím PaySafe Card ?
PaySafe Card se dá zakoupit v jakékoliv trafice, či pumpě. Stačí se zeptat prodejce.
Kostya Ransomware (K0stia) is a Czech cyber infection. Much like Mischa and Petya (which we’ve both tackled), this program is destructive. Of course it would be destructive, it’s ransomware. File-encrypting parasites are a complete and utter pest. Many researchers even claim this is the most virulent thing online. To put it mildly, you’re in for trouble. Kostya Ransomware uses the 256-bit encrypting algorithm. This way it denies you access to all your personal files. Yes, all of them. The virus targets a rich variety of file formats so it causes quite a hassle. Furthermore, it causes damage. Once your computer gets infected, Kostya performs a thorough scan on your device. As a result, it locates all personal information you’ve stored on board. We’re talking pictures, music, videos. Wave your favorite files goodbye as Kostya Ransomware effectively locks them. It might also lock some important work-related Microsoft Office documents. The parasite messes with their original file formats. By adding the .k0stya extension, it makes your data unreadable. Your computer won’t be able to recognize the new file format so you won’t be able to use your data. Voila. This virus encrypts anything of value that it finds on board. It then displays a worrisome ransom note that’s entirely in Czech. Kostya is country-oriented as it goes after PC users mainly in the Czech Republic and Russia. However, that doesn’t mean you living in the USA, for example, will stop the infection. This parasite’s ransom note is accompanied by the image of a skull. Hackers tend to be overly dramatic when it comes to ransomware. According to this message, there’s only one way for you to free your encrypted data. And it involves money. Do you now see where ransomware received its name from? These infections lock your files for one very simple yet aggravating reason. They are aiming at your bank account. The scheme goes like this – Kostya Ransomware strikes unannounced and out of the blue. It encrypts all your private files and leaves them useless. Most PC users wouldn’t remain calm and collected seeing these random unauthorized changes. Once they panic, hackers start playing mind games with them. Ransomware is nothing but a clever attempt for a cyber fraud. A nasty scam that might cost you a lot of money. The Kostya Ransomware is very humble in that department, though. It only demands 300 CZK which equals about 12 USD. This has to be one of the “cheapest” ransomware infections we’ve ever come across. Usually, the ransom varies between 0.5 and 1.5 Bitcoins. Keep in mind that 0.5 Bitcoin equals about 300 USD and 1.5 equals over 950 dollars.
How did I get infected with?
You probably clicked something open that you should have ignored. The most likely explanation is that Kostya Ransomware was sent straight to your inbox. Infections are sneaky like that. They pretend to be legitimate mail from a shipping company, for instance. This way, they trick you into thinking this is a harmless email. It isn’t. One careless click could easily set a vicious infection free. Eventually, you end up causing your own device harm. Stay away from suspicious emails and messages in the future. Also, avoid illegitimate websites/torrents/pop-ups. More often than not, those are corrupted. Ransomware also travels the Web with the help of other infections, usually Trojans. You should definitely check out the PC for more unwanted intruders. Last but not least, ransomware gets spread online via Exploit Kits. Always remember that preventing virus infiltration is much easier than deleting malware. Keeping your device infection-free should be your number one priority on the Web.
Why is Kostya dangerous?
Kostya Ransomware gives you a deadline. According to its nasty ransom note, you must complete the payment within 12 hours. This is an extremely small time frame. However, the money demanded isn’t large either. Crooks promise a decryption key in exchange for your money. They are supposed to help you unlock your inaccessible information. In reality, though, you’d be making a deal with greedy, dishonest cyber criminals. Does that sound like a good idea? Paying the ransom guarantees you NOTHING. Hackers tend to ignore their victims because, as mentioned, they are aiming for profit. Restoring your files was never part of the picture and neither is the decryptor. Regardless of whether the ransom is 12 dollars or 12 cents, do not pay it. If anything, you’d worsen your already bad situation furthermore. Don’t be a sponsor of crooks and don’t let them blackmail you. Also, stay away from the slothcbx@protonmail.com email address. You don’t need to contact this parasite’s developers. Get rid of their pesky infection instead. To do so manually, please follow our detailed removal guide down below.
Kostya Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Kostya Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Kostya encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Kostya encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



