Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Korean Ransomware?
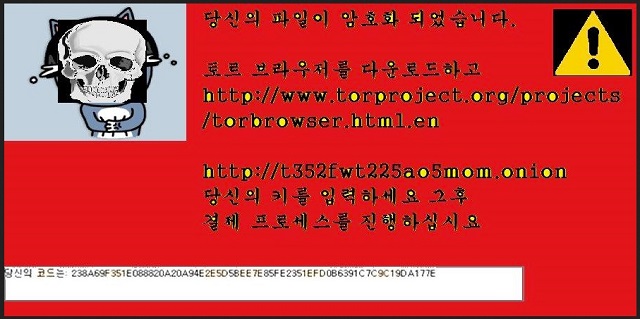
Reader recently start to report the following message being displayed when they boot their computer. The text is in Korean, but the English translation reads:
Your files have been encrypted.
Download and install https://www.torproject.org/projects/torbrowser.html.en
and enter your ID-code.
[Website and code given] Follow the instructions on the site.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Korean ransomware is a new menace, plaguing the cyber users. It goes by the name ‘Korean’ because the ransom message reads in Korean, and it mostly targets Koreans. But don’t breathe in relief just yet. That doesn’t mean you’re safe from the infection’s clutches. Even if you’re outside Korea, you can still find yourself its victim. And, let’s just say, you won’t like it. That’s quite the understatement. And, we’ll explain why. After the tool invades your system, it wastes no time but quickly goes to work. It encrypts every single file you have on your PC. No exceptions. Pictures, documents, videos, music, etc. Once it’s done, all your data is beyond your control. It adds the .암호화됨 extension at the end of your files. Thus, rendering them inaccessible. You cannot open them, and moving or renaming them won’t help. The only way to free your files from their ‘hostage’ status is with a decryption key. And, you’ve guessed it! You have to pay up to get it. That’s how ransomware works, and that’s how Korean is programmed to proceed. It sneaks in undetected, corrupts your data by encrypting it, and extorts you. The end-game is profit. The infection uses your naivety for monetary gain. But if you trust the tool to go through with its promises, you’re not just gullible. You’re a fool. Korean is a dangerous cyber threat. The people that unleashed it are malicious. They have agendas that don’t keep your best interest at heart. Do you honestly trust them to keep their word? Don’t kid yourself. They will betray you. Even if you comply fully, you will not win. Do you know why? The game is rigged against you from the start. It’s a colossal mistake to pay these people. If you do, you won’t just lose money. You’ll also expose your private life to strangers with questionable intentions. Don’t waste money. Don’t jeopardize your security. Do the wiser thing. Do NOT comply. Do NOT pay. It’s a difficult choice to make to forsake your files. But it’s the right one.
How did I get infected with?
Ransomware doesn’t just pop up one day and take over. Neither did the Korean one. It had to be approved into your PC. Applications like it have to seek your permission to enter. But don’t think they just show up and ask for it out in the open. Oh, no. They do it in the most covert way possible. More often than not, they turn to freeware or spam email attachments. They can also pose as bogus updates, like Java or Adobe Flash Player. And, before you know it, you’re dealing with a dangerous ransomware. That is, if you’re careless enough to allow it. Infections, like Korean, prey on distraction, naivety, and haste. So, if you wish NOT to get stuck with such a tool, be more cautious. Take your time, and always do your due diligence, when installing a tool or an update. Even a little extra attention can save you a ton of troubles.
Why is Korean dangerous?
Korean is a new HiddenTear crypto-virus variant, roaming the web. It’s a true menace. The ransomware locks your data via the AES-256 encryption algorithm. It leaves no stone unturned, so in the end everything on your PC is inaccessible. You cannot open a single file. PNG, DOC, DOCX, TXT, ZIP, RAR, JPEG, PDF, etc. You get the point. All your photos and documents, and everything else, is on lock down. And, it’s used as leverage against you. Korean uses your locked data as a hostage. After the encryption, it leaves a desktop message and a ReadMe.txt file, which state the same thing. Both explain, you’re the victim of a ransomware infection. And, if you wish to change that and free your files, you have to follow its requirements. It demands you transfer an amount ranging between .5 and 1.5 Bitcoin. Now, today, 1 Bitcoin is about 580.4 USD. That’s no small amount. But even if the requested sum was 1 USD, DO NOT PAY! Paying these people leads to an avalanche of troubles. If you complete the transfer, you open the door to your privacy to these people. And, once opened, it cannot be closed. So, ask yourself the following. Is your data worth your personal and financial information? That is what you’ll be gambling with. The stakes are high. Here’s experts’ advice: pick privacy over pictures. Files are replaceable. Your privacy is not.
Korean Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Korean Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Korean encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Korean encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



