Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Herbst Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
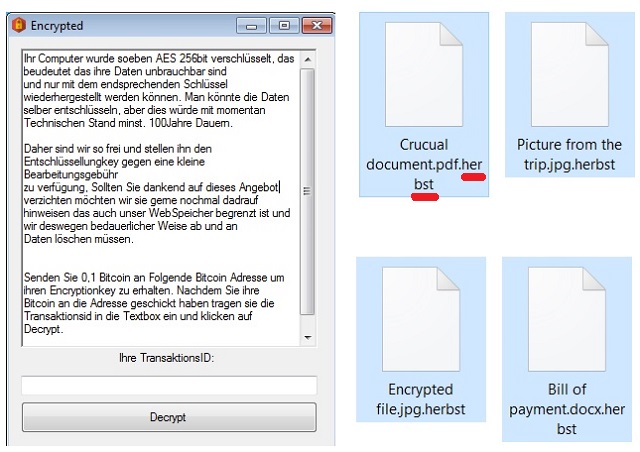
Your computer was just encrypted with the help of AES 256, against which any type of measures is useless, your data can be restored only with the help of a unique key. You can decipher the data yourself, but in today’s time, it would technically take 100 years.
This is why we won’t to as a not so big payoff for the decryption key. If you are agree to this proposal, we want to make you happy sooner, because our internet-database is limited in size and even if we do not want it, soon we will be driven into deleting your files.
After we have received the payment, we will send you a Transaction ID, which you need to paste in the text field and press on the button Decrypt.
Herbst is a ransomware infection, and if you come across it, you’re in for a pretty unpleasant experience. There’s a reason most web users cringe at the mere mention of the word ‘ransomware.’ These tools are intrusive, malicious, and immensely harmful. They’re designed to slither into your system undetected, and once in – corrupt it entirely. The nasty program takes over, and gets a hold of every single file you have stored on your PC. It encrypts it and, thus, renders it inaccessible for you. Then, once all of your data is locked, it demands you that if you wish to unlock it, you have to pay a ransom. And, here’s their primary objective – ransomware tools are programmed to take your files hostage, and demand monetary payment for their release. Above all else, you have to understand this: these are untrustworthy, unreliable people! Do NOT pay them even a single cent! If you comply with their requests and send them the desired amount, you will only find yourself in a worse situation later. For one, you’d expose your personal and financial details to these strangers, and that’s a risk you mustn’t take! So, don’t do it! Don’t pay! Don’t jeopardize your private life! Yes, it seems harsh and unfair that you’d lose your data because of a dangerous, damaging infection, but don’t you think that’s the better option than losing your privacy?
How did I get infected with?
Ransomware doesn’t just show up on your computer one day. Such tools cannot install themselves unless they ask for your permission first, and receive it. If you don’t green-light their installment, they cannot enter. In other words, Herbst is currently on your computer because you allowed it you be. But don’t be too hard on yourself. After all, these types of programs don’t just openly ask for approval. They do it covertly via deception and finesse. Otherwise, they leave too much to chance, and they can’t have that. More often than not, they turn to the old but gold means of invasion to sneak into your system undetected. That usually includes hitching a ride with spam email attachments or freeware or hiding behind corrupted links or sites. Also, these cyber threats can pose as fake updates. For example, you may be utterly convinced you’re updating your Adobe Flash Player or Java, but you’d be wrong. In actuality, you’ll be installing a dangerous infection without even realizing it. To prevent that from happening, you must be extra vigilant. Always do your due diligence, and never rush or give into naivety. Remember that infections prey on carelessness to gain entry, so make sure not to provide it.
Why is Herbst dangerous?
Once Herbst slithers into your system, it goes to work and proceeds with encrypting everything. And, we do mean everything. Its reach extends to every part of your system as it leaves no stones unturned in its quest to take control of every single file you have stored on your computer. Pretty soon, your documents, pictures, videos, music, etc., has fallen victim to the nasty tool and is rendered inaccessible. You’ll find your data is bearing a new name, and can no longer be opened. That’s right. To complete the encryption process, the tool adds the .herbst files extension. And, you can try to change the name as many times as you want, but it won’t accomplish anything. The ransomware clues you in that the one way to free your files, from its captivity, is to pay the ransom. By paying the requested monetary amount, you’ll receive a decryption key, and when you apply it – voila! You’ll have your files back! But is it truly that simple? No. No, it’s not. Because, here’s the thing. These people that unleashed the cyber threat onto the web and its users are malicious, and they cannot be trusted. You cannot possibly believe that they’ll keep their end of the bargain, just because they say so. There are countless ways the exchange can go down, and they all end badly for you. Say, for example, you transfer the money. Here’s what can potentially happen. So, the kidnappers want 0.1 Bitcoin from you, which is less than a hundred dollars, and most people can afford to part with them. So, you pay and wait to receive the decryption key. There are two ways that can end. One, they send it, and you get it. And, two – they don’t. And, as much as you might think that option one is preferable, it can also go two ways. The key can certainly work and decrypt your files, but it can also flop. Then you’d be left with less money and still-encrypted data. But, here’s one more thing you need to consider. Even if everything goes splendidly with the transaction, and you free your files, you’ll still have a ransomware infection on your computer. And, what’s to stop that infection from acting up again the very next day, and send you back to square one? Nothing. So, when you take everything mentioned so far into consideration, it should truly be evident that paying is not an option. Do what’s best for you and your PC, and discard your data to protect your privacy. It’s for the best.
Herbst Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Herbst Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Herbst encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Herbst encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



