Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Hakuna Matata Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
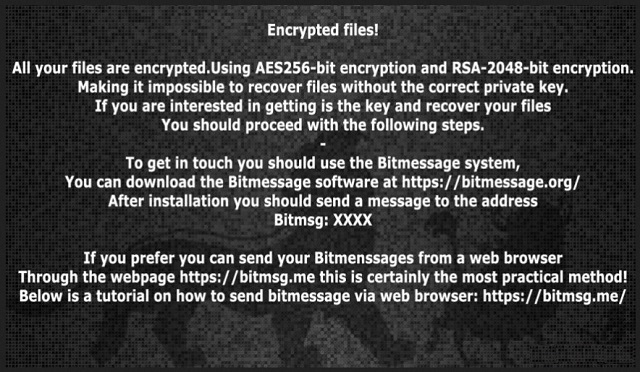
Encrypted files!
All your files are encrypted.Using AES256-bit encryption and RSA-2048-bit encryption.
Making it impossible to recover files without the correct private key.
If you are interested in getting is the key and recover your files
You should proceed with the following steps.
–
To get in touch you should use the Bitmessage system,
You can download the Bitmessage software at https://bitmessage.org/
After installation you should send a message to the address
Bitmsg: BM-2cWcp***
If you prefer you can send your Bitmenssages from a web browser
Through the webpage https://bitmsg.me this is certainly the most practical method!
Below is a tutorial on how to send bitmessage via web browser: https://bitmsg.me/
1 B° Open in your browser the link
https://bitmsg.me/users/sign_up
Make the registration by entering name email and password.
2 B° You must confirm the registration, return to your email and follow the instructions that were sent.
3 B° Return to site sign in
https://bitmsg.me/users/sign_in
4 B° Click the Create Random address button.
5 B° Click the New massage button
6 B° Sending message
To: Enter address: BM-2cWcp***
Subject: Enter your key: afe299***
Menssage: Describe what you think necessary
Click the Send message button.
Your message will be received and answered as soon as possible!.
Send message to: BM-2cWcp***
Your Key: afe299***
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Hakuna Matata, what an unfortunate name for a ransomware infection. But it is what it is. And, one of the newest players in the ransomware category bears the name Hakuna Matata. It’s kind of ironic, don’t you think? Considering the fact tat it means ‘no worries.’ And, if you get stuck with it, you should definitely worry. It’s not a pleasant experience dealing with that program as it’s an utter plague on your PC. It slithers in via slyness and subtlety. Then, once it settles, all hell breaks loose. The nasty tool takes control of your data, and locks them. It appends a special extension at the end of each of your files. Thus, making sure, you cannot open or access them in any way. The application backs you into a corner. Then, provides you with an escape route – pay a ransom and it all goes away. You’ll be given the tools to remove the encryption, and regain control over your data. But is it really that simple? Well, no. Nothing ever is. The ransomware does its best to cut your every path and leave you with just one option – compliance. It wants you to give up and pay the ransom. Do NOT! It’s a trap. Ans, once you fall from it, you can’t recover. That’s because if you pay the ransom, you expose your privacy. The cyber criminals behind Hakuna Matata get access to your personal and financial details. Don’t let them! When it comes to choosing between your data and your privacy, it’s a pretty obvious choice. One is replaceable. The other is not.
How did I get infected with?
The Hakuna Matata tool turns to the usual antics to invade your PC. The old but gold methods of infiltration tend to do the trick. That includes hiding behind corrupted sites or links. Or, hitching a ride with spam email attachments. Freeware is also a preferred method since users are quite careless during its install. Instead of reading the terms and conditions with care, they skip them. And, just say ‘Yes’ to everything with no regard of consequences. Other means of invasions involves the use of fake updates. For example, you may believe you’re updating your Java, but you’re not. In reality, you’re giving the green light to a dangerous cyber threat. Carelessness leads to infections. Hazardous tools just like the Hakuna Matata ransomware. They prey on distraction, gullibility, and haste. Don’t grant them. Don’t throw caution to the wind when installing a tool or update. Vigilance is crucial if you wish to keep an infection-free PC.
Why is Hakuna Matata dangerous?
As soon as the infection makes its way into your system, it gets to work. It locks your data with help of AES256-bit and RSA-2048 encryption algorithms. It adds the “.HakunaMatata” extension to each file. So, say you had a document called “important.” After the ransomware’s done with it, you’ll find it as “important.hakunamatata.” Once your data gets renamed, that’s it. You can no longer open them. And, trying to change back their names or moving them around does nothing. The only way to regain access is with a decryption key. A key, which only the cyber criminals, behind the infection, have. And, for them to give it to you, you have to follow their demands. Demands, which are thoughtfully laid out in the ransom note, they leave for you to find. It’s called “Recovers files yako.html.” It contains an explanation on your current predicament, and instructions on payment. If you wish to receive the decryption key that frees your files, you have to pay in Bitcoin. The amount varies between 1 and 3 Bitcoins. And, that’s quite the sum! A single Bitcoin is around 600 US Dollars. But the ransom amount is irrelevant when dealing with ransomware. It doesn’t matter if the infection wants one dollar or ten thousand dollars. Whatever the case, you mustn’t pay! Payment leads to exposing your privacy to cyber criminals. Think about it. To transfer the money, you have to provide personal and financial I information. Information, which these extortionists can then use as they wish. No pictures or documents are worth that risk. So, don’t take it. Make the wiser, more difficult, choice – discard your data.
Hakuna Matata Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Hakuna Matata Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Hakuna Matata encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Hakuna Matata encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



