Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Gryphon Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
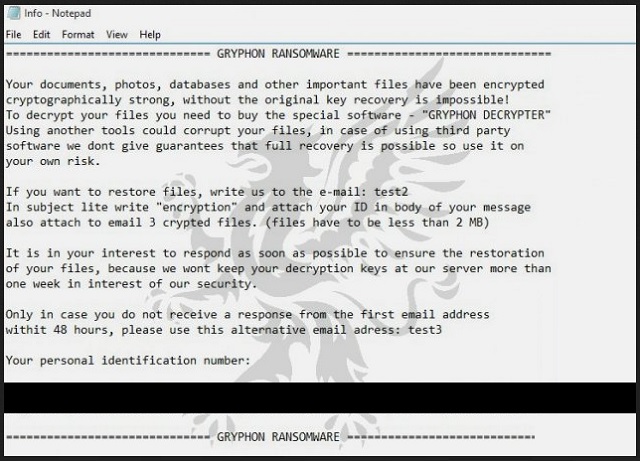
=== GRYPHON RANSOMWARE ===
Your documents, photos, databases and other important files have been encrypted
cryptographically strong, without the original key recovery is impossible!
To decrypt your files you need to buy the special software – “GRYPHON DECRYPTER”
Using another tools could corrupt your files, in case of using third party
software we dont give guarantees that full recovery is possible so use it on
your own risk.
If you want to restore files, write us to the e-mail: test2
In subject lite write “encryption” and attach your ID in body of your message
also attach to email 3 crypted files. (files have to be less than 2 MB)
It is in your interest to respond as soon as possible to ensure the restoration
of your files, because we wont keep your decryption keys at our server more than
one week in interest of our security.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Only in case you do not receive a response from the first email address
withit 48 hours, please use this alternative email adress: test3
Your personal identification number: –
=== GRYPHON RANSOMWARE ===
Ransomware viruses are nothing new. These parasites are stealthy and highly destructive. The Gryphon Ransomware is not an exception. This pest was recently discovered. In its rather short existence, it has managed to infect hundreds of computers. And the number is still growing. It appears that Gryphon is still under developments. It usually adds the “.[decr@cock.li].gryphon” extension at the end of all encrypted files. However, variants of the virus also add “.[test].gryphon” and “.[bravobravo@cock.li].gryphon” extensions. The Gryphon Ransomware operates like a typical member of its malicious family. It enters its victims’ computers unnoticed and scans their hard drives. It targets user-generated files such as your archives, pictures, music, documents, videos, and databases. Once the encryption process is complete, the virus drops its ransom note. Do not expect something sophisticated. The ransom note is a simple text file named “!## DECRYPT FILES ##!.txt.” It contains general information about the virus, such as what has happened to your files. Yet, it doesn’t give details about the nature of the ransomware and the exact amount of the demanded ransom. All it states is that the victims should contact the crooks within one week. The note reads that you need special “decryptor” which only the crooks can provide. It also states that third party software may lock your files permanently. Unfortunately, there is no free description tool for this parasite. However, malware experts linked this virus to the infamous BTCWare Ransomware and are working on description applications. So, have some hope. Meanwhile, do not let the Gryphon Ransomware roam your system. Even though you cannot notice it, the virus is active. You cannot create new files as the ransomware will lock them immediately. If you connect external devices to your PC, the virus will infect them too. Therefore, clean your computer. Gryphon Ransomware is a complicated virus. So is its removal. We recommend you to use a trustworthy anti-virus application.
How did I get infected with?
The good old spam emails are the main cause of ransomware infections. The crooks add Gryphon Ransomware as an attached file. They would also add a download link in the letter. In some cases, the crooks embed malicious code in the body of the letter itself. This code executes the moment you open the corrupted messages. So, do not open emails from strangers. Check the sender’s contacts first. You can simply enter the questionable address into some search engine. If it was used for shady business, someone might have complained. Yet, this method is not flawless. New emails are created every day. If you are a part of the first wave of spam messages, there may not be any evidence online. So, double-check the sender. Scammers tend to write on behalf of well-known organizations and companies. If you receive such a message, go to the company’s official website. You can find their authorized email address there. Compare them with the one you have received a letter from. If they don’t match, delete the pretender immediately. The Internet is a dangerous place. It is roamed by many nasty parasites. They wait for you to make a mistake. Always keep your guard up. Keeping your anti-virus program up to date is also a good idea.
Why is Gryphon dangerous?
Gryphon Ransomware sneaks into your PC uninvited, locks your files and blackmails you. The ransom note of the virus does not specify the exact amount of the demanded ransom. The crooks want you to contact them. Do not do it. Do not get in touch with cyber criminals. These people will threaten you. They will use psychological tricks to get your money. Besides, no one can guarantee you that they will keep their part of the deal. They may not send you a working decryption tool, if they send you anything at all. Practice shows that the hackers tend to ignore the victims once the ransom is paid. If such an event occurs, you cannot ask for a refund. The crooks demand Bitcoin. This currency is untraceable. Even authorities cannot help you get your money back. One more thing to mention here. If you use your infected PC to pay the ransom, the Gryphon Ransomware may record your paying details. The hackers can use this information to drain your bank account and even to steal your identity. You are dealing with criminals. You cannot win a game against them. Consider discarding your data. Clean your machine and start backing up your files regularly. This way you will be prepared if a ransomware strikes again.
Gryphon Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Gryphon Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Gryphon encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Gryphon encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



