Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove GrodexCrypt Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
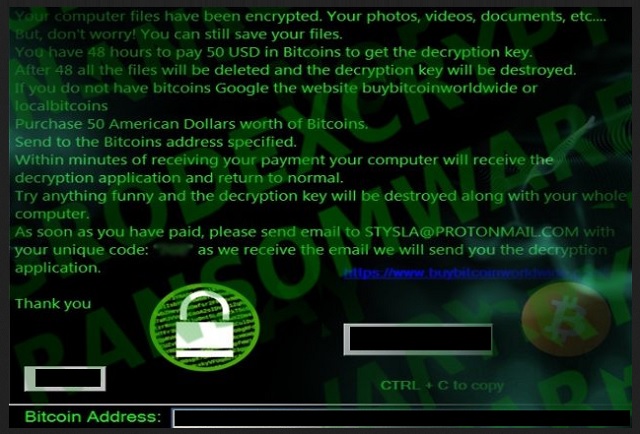
Your computer files have been encrypted. Your photos, videos, documents, etc….
But, don’t worry! You can still save your files.
You have 48 hours to pay 50 USD in Bitcoins to get the decryption key.
After 48 all the files will be deleted and the decryption key will be destroyed.
If you do not have bitcoins Google the website buybitcoinworldwide or localbitcoins
Purchase 50 American Dollars worth of Bitcoins.
Send to the Bitcoins address specified.
Within minutes of receiving your payment your computer will receive the decryption application and return to normal.
Try anything funny and the decryption key will be destroyed along with your whole computer.
As soon as you have paid, please send email to STYSLA@PROTONMAIL.COM with your unique code: “7C8” as we receive the email we will send you the decryption application.
Thank you
The GrodexCrypt tool falls under the ransomware umbrella. Ransomware is the absolute worst type of cyber threat, you can encounter. That’s a statement, corroborated by users, who’ve had the misfortune of dealing with such a tool. These infections are malicious. They invade through deceit and subtlety, and then take over. They target your data. All of it! The hazardous tool uses a special encryption algorithm to lock your files. Pictures, documents, videos, everything. Once it all gets encrypted, guess what happens next? The ransomware proceeds to demand you pay ransom. The scheme goes as follows. Pay the ransom, get the necessary decryption key, free your files. And, it seems simple enough, doesn’t it? Well, it’s not. There’s about a dozen ways the ransomware can double-cross you. Understand that you’re dealing with a cyber plague. It’s an infection, designed by cyber criminals. People, who don’t care about your best interest. People, whose main objective is money. Your money getting into their hands. Don’t, for one second, believe they care about you getting your data back. They don’t. With that in mind, do you honestly believe they’ll keep their end of the bargain? Can you trust them to go through with it? No. The answer is ‘No!’ Do yourself a favor, and don’t fall for the lies. You’d avoid an avalanche of troubles if you don’t. If you do, you’re setting yourself up for a bad time. As harsh as it may seem, say goodbye to your files. It’s the best possible scenario. Data is replaceable.
How did I get infected with?
GrodexCrypt turns to the usual tricks when it comes to infiltration. Though, spam email attachments are among the most common ones, there are plenty more. There’s an entire myriad of methods, ransomware can use as a way to invade your PC. That includes hiding behind freeware. As well as, corrupted links or sites. The tool can also pretend to be a fake update. For example, you may believe you’re updating your Java, but you’d be wrong. In actuality, you’re installing a dangerous cyber menace. Do you know what helps prevent that scenario? Caution. Doing your research. Always opt to do your due diligence. It does go a long way. Take the time to read the terms and conditions. Don’t skip them, and head straight for the YES. That naivety almost always leads to infections. Know what you allow into your system beforehand. Even a little extra attention today saves you a ton of troubles tomorrow.
Why is GrodexCrypt dangerous?
The GrodexCrypt tool is an updated version of the MIRCOP one. After it’s done encrypting your data, you’ll find everything renamed. For example, if you had a picture called ‘me.jpg’ it turns into ‘Lock.me.jpg.’ Once that phase is complete, you can no longer access your files. Try as you might but it won’t work. Moving them, changing back the names, it all does nothing. The only way to regain control of them is via decryption key. And, that costs you. As you discover in the ransom note, GrodexCrypt left for you. 50 Dollars in Bitcoins, to be precise. And, though, that seems an insignificant amount, don’t make rash decisions. If you pay these people, you WILL regret it. And, here’s why. What happens when you transfer the ransom amount? You lose money, yes. But it’s more than that. You leave your personal and financial information so the transfer can go through. Information, which the cyber kidnappers can, then, get a hold of. You, essentially, give them a key to your private life. You open the door yourself, and leave them free to invade. What do you think follows after? Strangers with agendas should not get access to your private details. No files are worth that. And, even if you lie to yourself, and decide that your data is too precious to discard, halt! Paying the ransom guarantees you nothing. GrodexCrypt promises to send you the needed key upon receiving your transfer. Well, what if it doesn’t go through with that promise? What if it sends you nothing? Or, sends you a key that doesn’t work? And, even if it does work, and frees your files then what? You still have a ransomware on your computer. The decryption key does not remove the infection, only the encryption. These are all valid questions. You shouldn’t ignore them for a blind faith in cyber extortionists. Be better. Don’t give into naivety. Make the tougher, wiser choice, and forsake your files. It’s the better thing to do.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
GrodexCrypt Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover GrodexCrypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with GrodexCrypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate GrodexCrypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



