Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Flyper Ransomware?
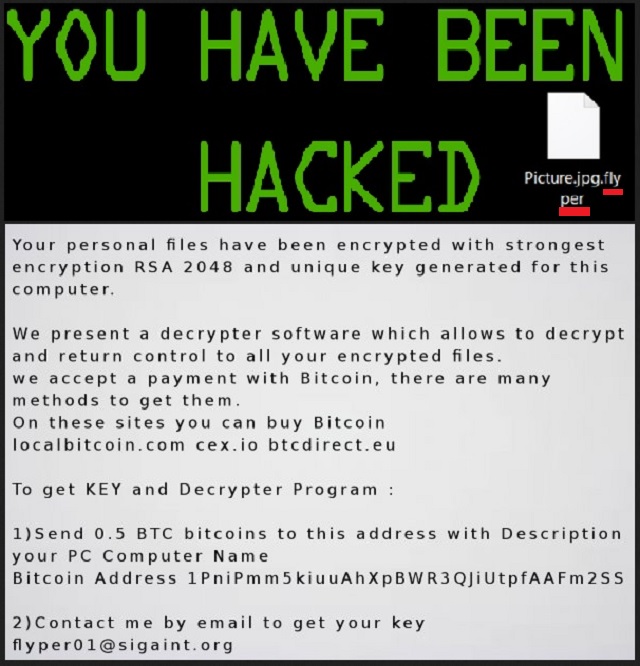
Reader recently start to report the following message being displayed when they boot their computer:
Your personal files have been encrypted with strongest encryption RSA 2048 and unique key generated for this computer.
We present a decrypter software which allows to decrypt and return control to all your encrypted files.
we accept a payment with Bitcoin, there are many methods to get them.
On these sites you can buy Bitcoin
localbitcoin.com cex.io btcdirect.eu
To get KEY and Decrypter Program :
1)Send 0.5 BTC bitcoins to this address with Description your PC Computer Name
Bitcoin Address 1PniPmm5kiuuAhXpBWR3QJiUtpfAAFm2SS
2)Contact me by email to get your key
flyper01@sigaint.org
Flyper Ransomware is yet one more file-encrypting program. This pest is related to the infamous Hidden Tear project. And it’s a particularly unpleasant piece of malware to be stuck with. If you didn’t know it already, ransomware is the most problematic type of virus currently on the Web. Now, there’s a reason why ransomware is so immensely dreaded. Numerous reasons, actually. You’ve managed to download an immensely devastating infection. It goes without saying you have to take action. It today’s article you’ll find all the information you need about the pesky Flyper. First of all, this parasite uses the RSA-2048 encrypting algorithm. It locks your files and adds a .flyper extension to them. As you could imagine, this file extension is malicious. What ransomware aims for is to encrypt the personal data you’ve stored on your PC. Unfortunately, Flyper takes down a huge variety of file formats. Starting with pictures and music, proceeding with MS Office documents, presentations, videos, etc. This infection practically encrypts all the important data you have. Needless to say that by doing so, Flyper Ransomware might cause you irreversible harm. Once encryption is complete, your files are renamed. You can no longer view or use the target data. That’s not even the worst part. While locking your information, the virus also creates payment instructions. It drops an instructions.txt file and modifies your desktop wallpaper. This way, Flyper Ransomware makes sure you’ve noticed its ransom note. Ransomware is quite skillful at catching your attention, don’t you think? According to the ransom message, “You have been hacked”. As if you didn’t know this already. Flyper provides an email address (flyper01@sigaint.org) which will contact you with hackers. Why would want to contact hackers, you may ask? Because they hold the decryption key. We’ve reached the sole reason why ransomware exists in the first place. These infections are nothing but unfair attempts for cyber frauds. Crooks lock your personal files and bombard you with empty promises and empty threats. Your files are now being held hostage so hackers could scam you. As you could imagine, there’s no guarantee you will receive a decryptor even if you make the payment. The sum demanded isn’t a small one either. Hackers want you to pay 0.5 bitcoin which is approximately 300 USD. Are you pictures really worth 300 UDS? Furthermore, are you willing to pay the ransom knowing you could decrypt all your files for free? Keep on reading.
How did I get infected with?
No one installs ransomware voluntarily, that’s a given. Hence, Flyper must have applied some secretive and stealthy technique to get downloaded. The most popular method involves spam messages. Keep in mind that sometimes hackers send malware straight to your inbox. One single click on a seemingly harmless message is all the virus needs. To prevent installation, constantly watch out for malware. This nuisance often pretends to be legitimate mail so make no mistake. Delete what you don’t trust. It is much easier to prevent installation than to uninstall a parasite afterwards. Also, ransomware might get installed with the help of a Trojan horse. That means Flyper Ransomware is probably not the only intruder on board. Check out the PC and be cautious in the future. Stay away from illegitimate torrents, random executables and unverified websites. There’s no such thing as being too careful on the Web.
Why is Flyper dangerous?
Flyper Ransomware is a deceptive, harmful infection. It denies you access to your very own personal files. Then the virus starts playing mind games with you. Hackers rely on the fact you’d give into despair and anxiety. Ultimately, they want to steal your money. That means the very last thing you should do is to pay the ransom. Why sponsor crooks? Why support their malicious business and give away your Bitcoins? Ignore all ransom notes this infection forces on you and don’t be gullible. Hackers are supposed to help you free the encrypted information. However, in reality, they are only interested in gaining profit. Don’t let them drag you into this illegitimate scheme and delete the virus instead. Remember, cyber criminals are trying to blackmail you so you have no reasons to trust them. To delete Flyper Ransomware manually, please follow our detailed removal guide down below.
Flyper Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Flyper Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Flyper encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Flyper encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



