Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove FileCoder Ransomware?
FileCoder is a malicious ransomware. To call it “intrusive” would be an understatement. This hazardous infection slithers its way into your system and completely overtakes it. Once it dupes you into unknowingly agreeing to install it, the tool starts causing you all kinds of grievances. FileCoder is named “ransomware” for a reason. The tool sneaks into your system undetected, and when it wishes to reveal its presence, encrypts everything you have stored on your computer. That means all of your data is no longer your. Every file – photo, video, music, document, everything, now belongs to FileCoder. To get it back, you’ll have to comply with its demands. Oh, yes. It has demands. As soon as it’s done with the encryption process, it displays a ransom note, which explains what you have to do so as to reclaim the possession of your data. Do NOT go through with these demands! If you do, the most likely scenario ends up with you regretting your choice to comply. It may seem crude, but the best course of action you can take is to accept that your files are lost to you and cut your losses. If you give into FileCoder, you’re only setting yourself up for a bad time. So, don’t.
How did I get infected with?
FileCoder slithers its way into your system quite deceptively. It resorts to slyness and subtlety and uses every trick in the book so as to dupe you into installing it. And, not only does it succeed, but it also manages to keep you oblivious to the fact that you agreed to install a hazardous infection on your computer. By the time you realize the mistake you’d made, it’s too late as the damage is already done. The tool tends to sneak in with the help of the old but gold methods of invasion. More often than not, it hitches a ride with freeware. It provides possibly the easiest access point as most users pay little to no attention during its installation. They rush the process and don’t even bother reading the terms and conditions. Instead, they agree to everything and hope for the best. Well, that’s a decision you’ll most certainly regret once you turn on your PC and find it on lockdown with a ransom note on the desktop. Don’t give into distraction and haste! Don’t throw caution to the wind as a little extra attention today can save you a lot of headaches and troubles tomorrow.
Why is FileCoder dangerous?
As was already stated, FileCoder is a damaging, intrusive, and malevolent infection. It sneaks into your system through deceit and treachery and jeopardizes your personal and financial information. How? Well, once the tool slithers in, it encrypts all of the data you have on your PC. You can no longer open your files, access the internet, or anything really. After the encryption is complete, it greets you with a ransom note, listing its demands for the “release” of your files. If you do everything it asks of you, it sends you a decryption key that you can use to free your data. When you see the ransom note, you have two choices. One, do everything the tool asks of you, and pray it keeps its promise, and gives you the said key. And, two, decide to cut your losses, and say goodbye to every file you have on your PC. Option two seems harsh, but it’s the better one. It’s preferable, considering option two places your personal and financial information in grave jeopardy. Even though, option one seems like it cannot do any harm, it can. It doesn’t solve your problems, only creates more. More often than not, ransomware asks that monetary payments are made for the release of your files. If you pay the tool, you risk malicious third parties to get a hold of your private details. Do you want strangers to have access to your personal and financial information? Furthermore, even if you comply with each of the ransomware’s demands, it can still choose to NOT give you the decryption key. After all, it’s hardly a reliable tool. It’s untrustworthy and deceptive. Also, if it, by any chance, decides to give you the key, there’s nothing stopping it from encrypting your data again the very next day. It’s a never-ending loop. Don’t you want to break it? Each path you take when dealing with ransomware doesn’t end well. The best way to protect yourself from tools such as FileCoder is to create back-ups for all of your files. That way, if one does manage to sneak in, it’s not the end of the world.
FileCoder Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
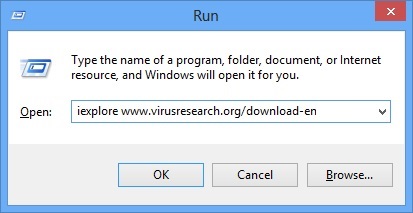
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove FileCoder Manually
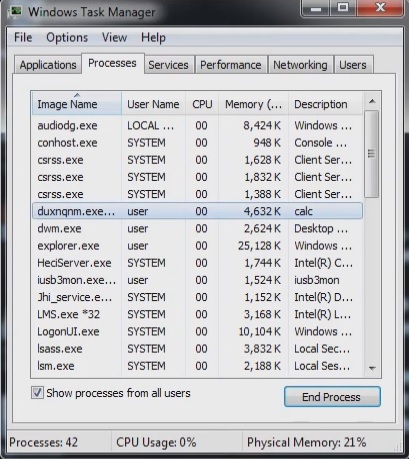
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.
STEP 3: Restore Encrypted Files
There are several methods you can use, however nothing is guaranteed.
Method 1 – recover the encrypted files by hand:
You can try to use the built in feature of Windows called System Restore. By default the system restore feature is automatically turned on. Windows creates shadow copy snapshots that contain older copies since the system restore was performed. These snapshots will let us to recover any previous version of your file, although it will not be the latest one, still you can recover some important information. Please note, that Shadow Volume Copies are only available with Windows XP SP2, Vista, Windows 7 and Windows 8.
Method 2 – partially restore the encrypted files by using Microsoft Office junk files:
Basically you need to show your hidden files. The fastest way to do that is:
- Open Folder Options by clicking the Start button .
- In the search box type “FOLDER OPTIONS”.
- Select View TAB
- Under Advanced settings, find Show hidden files and folders and select it and then click OK.
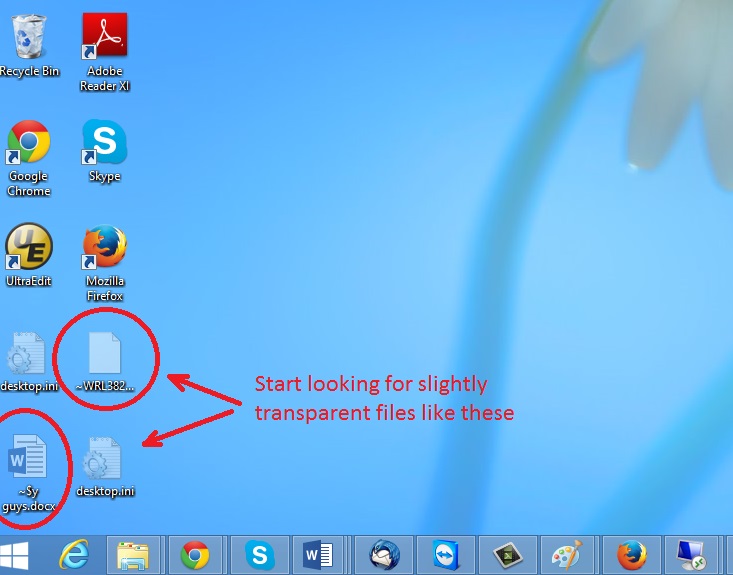
In the picture above I marked two hidden files. You are interested in every file that looks like ~WRL382.tmp This is actually a Microsoft office junk file that contains the previous version of the Word document itself. The Cryptowall parasite will not encrypt these files. The name of the file will be unknown, but you can recover a lot of lost documents using this method. This can be utilized for Microsoft Word and Microsoft Excel. In addition you can try to match the file sizes in order to figure out what is what and eventually you can restore a slightly older original document. In the picture on the left there is another method you can locate the files in question.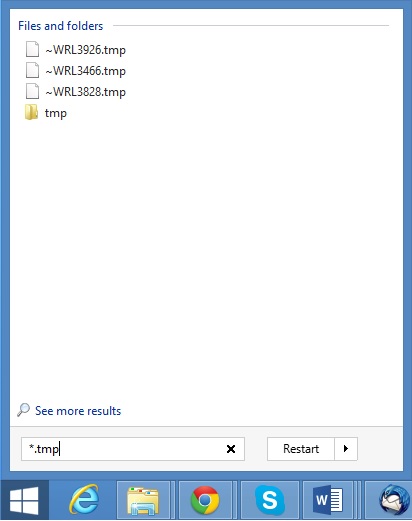 All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
Method 3 – Decrypt Encrypted Files
A few tools has been developed to try that – like the Panda Ransomware Decrypt Tool or Kaspersky lab standalone decryptors, however nothing is guaranteed. If you go that way you should know that there are some limitation like you have to have an original and encrypted file in order to try to find a proper decryption key.