Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to remove FessLeak Ransomware?
FessLeak is classified as a ransomware infection and as such what it does is to encrypt all the files on your PC. This means that you will not be able to open your photos, videos, or text documents if FessLeak has gained access to your system. Shortly after infiltration, FessLeak will present you with a message informing you about the encryption of your files and asking you to pay a ransom in order to get them back. No matter how worried you are and how important the encrypted files are, you should not spend the requested amount money because we can assure you that it will be useless. Instead, you should do your best to get rid on the malicious ransomware infection and start using your PC as you usually do.
How did I get infected with?
Same as other infections, ransomware is distributed in several ways. The most common one is by attaching the infection to a spam email and disguising the email as a real and urgent message. Then, when the user opens it and downloads the attached file, he or she automatically installs the malicious infection. Researches show, however, that FessLeak mainly takes advantage of the vulnerabilities of the Adobe Flash player. If this program is not kept up-to-date, it creates opportunities for cyber criminals to exploit it and make you a subject to infections by FessLeak. Also, if there is no active legitimate security tool to protect your system, it is very likely that you will soon end up with a bunch of infections on your PC, and pray that they are not ransomware like FessLeak.
Why is FessLeak dangerous?
There is a group of ransomware infections called Crypto, and FessLeak is the newest member of this group. Unfortunately unlike its predecessors FessLeak will fully encrypt your files, so it will be practically impossible to decrypt them. Hence, you should not fall for the lies in the warning message that assures you that purchasing a special key or a code will restore your files. The only thing that can help you in this situation is file back-up, if you have done any prior to infecting your system with FessLeak. Another problem that may occur concerns your privacy. FessLeak will collect information about you that can be used for all kinds of purposes by the cyber criminals who created this ransomware. The moment you see a message by FessLeak on your desktop, do not panic but immediately remove the infection from the PC.
FessLeak 2015 Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

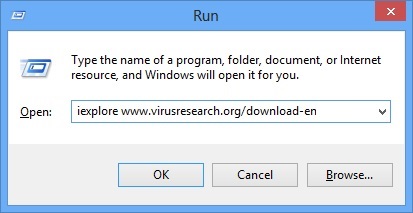
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove FessLeak Manually
Restart your computer into Safe Mode
Use msconfig to locate the startup location of the the virus
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Delete all files in your TEMP directory.
Carefully check the APPDATA directory for unknown programs.
Please, have in mind that the names generated by the virus are random, that’s why it is recommended to run the professional scanner above to identify the files. A few tools were developed to decrypt the encrypted files, however there is NO guarantee it will work at all.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.