Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove DMA Locker 4.0 Ransomware?
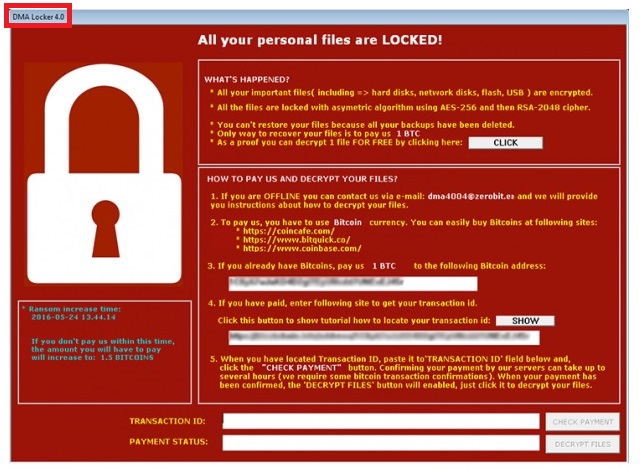
Reader recently start to report the following message being displayed when they boot their computer:
All your personal files are LOCKED!
WHAT’S HAPPENED?
* All your important files (including => hard disks, network disks, flash, USB) are encrypted.
* All the files are locked with asymmetric algorithm using AES-256 and then RSA-2048 chipper.
* You can’t restore your files because all your backups have been deleted.
* Only way to recover your files is to pay us 1 BTC
* As a proof your can decrypt 1 file FOR FREE by clicking here:
HOW TO PAY US AND DECRYPT YOUR FILES?
1. If your are OFFLINE you can contact us via e-mail: dma4004@zerobit.en and we will provide you instructions about how to decrypt your files.
2. To pay us, you have to use Bitcoin currency. You can easily buy Bitcoins at following sites:
*https://coincafe.com/
*https://bitquick.co/
*https://www.coinbase.com/
3. If you already have Bitcoins, pay us 1 BTC to the following Bitcoin address:
4. If you have paid, enter following site to get your transaction id.
Click this button to show tutorial how to locate your transaction id:
5. When you have located Transaction ID, paste it to ‘TRANSACTION ID’ field below and, click the “CHECK PAYMENT” button. Confirming your payment by our servers can take up to several hours (we require some bitcoins transaction confirmations). When your payment has been confirmed, the ‘DECRYPT FILES’ button will enable, just click it to decrypt your files.
We first came across DMA Locker at the beginning of 2016. However, this infection has improved immensely and hackers now present us the brand new 4.0 version. It’s more complicated, more aggressive, more harmful and much more problematic than all the previous DMA Locker editions. Ransomware infections in general are on the rise right now so crooks tirelessly keep on working on new programs of this kind. Why? Because ransomware is profitable. These infections are used so crooks could harass, upset, deceive and, ultimately, blackmail gullible PC users. Ransomware-type viruses are considered to be the most dangerous type of virus currently on the Web for numerous reasons. That means you’re now stuck with a particularly dreaded cyber parasite. As mentioned, ransomware offers cyber criminals quite a convenient way to gain illegitimate profit online. Therefore, it’s only logical hackers would mainly focus on these exact infections. That is how DMA Locker 4.0 was created. Following the classic ransomware pattern, DMA Locker 4.0 drops a malicious executable. Now, when this executable gets launched, trouble begins. The parasite performs a thorough scan on your device searching for personal files to encrypt. Pictures, music, Microsoft Office documents, videos – anything of value on the PC falls victim to this virus. Furthermore, DMA Locker 4.0 works with all Windows versions. Unfortunately, once the parasite’s scan is complete, consider your data gone. Ransomware infects a huge variety of file formats so practically all your valuable files are now locked. However, even before you attempt to open your files, something will draw your attention. You’ll notice a random !DMALOCK4.0 extension at the end of each file’s name. That’s a sign for a brand new file format. The problem is, your computer is not able to recognize it. As you could imagine, DMA Locker 4.0 turns all your personal information into useless gibberish. The parasite actually copies your files and deletes the originals; what you’re left with are the encrypted copies. Just like many similar ransomware infections, DMA Locker 4.0 uses AES-265 and RSA-2048 encryption algorithm. Thanks to this sophisticated method, your data is unreadable. How upsetting is the fact you’re denied access to your very own information? Wait till you hear the rest of it. While encrypting your files, DMA Locker 4.0 provided you with comprehensive payment instructions. You’re supposed to pay 1 Bitcoin (about 530 USD) in exchange for a decryption key. Do you see the scheme already? Ransomware is entirely money-oriented and the whole fiasco with your encrypted files aims at stealing money. It goes without saying that you shouldn’t even consider paying the ransom.
How did I get infected with?
It’s been reported that DMA Locker 4.0 travels the Web via Neutrino Exploit Kit. Of course, that doesn’t mean hackers have abandoned some of the older infiltration methods. For example, ransomware often gets spread with the help of Trojan horses, spam messages or spam email-attachments. That’s why it is highly recommended to avoid anything suspicious-looking you may find in your inbox. Simply delete what you don’t trust and make sure you don’t jeopardize your cyber safety. DMA Locker 4.0 often gets disguised as a perfectly legitimate email from a shipping company, for instance. Also, it might attempt to sneak in via corrupted torrents or malicious websites. Always watch out for potential threats when surfing the Web. Otherwise, you might accidentally infect your own computer will all types of parasites imaginable. Last but not least, stay away from unverified freeware/shareware bundles as those might include various parasites as well.
Why is DMA Locker 4.0 dangerous?
Ransomware is most certainly the type of infection you don’t want to have on board. This thing is very misleading and works in an extremely unfair way. Once all your data gets encrypted, DMA Locker 4.0 creates .txt and .html files which you will find in every single folder that contains infected data. Trust us when we say, those are a lot of folders. Hackers are forcing their ransom message on you because many people would give into their anxiety. Ultimately, they might follow the instructions given and pay the ransom. That is why you should not pay anything. Do the exact opposite of what hackers want from you and don’t let cyber criminals fool you. Remember, there’s no guarantee you would ever receive the decryption key crooks promise. Instead of making a deal with them, proceed to delete their parasite and make sure you never have to deal with ransomware again. To remove DMA Locker 4.0 manually, please follow the detailed removal guide you’ll find down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
DMA Locker 4.0 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover DMA Locker 4.0 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with DMA Locker 4.0 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate DMA Locker 4.0 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



