Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Commonransom Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
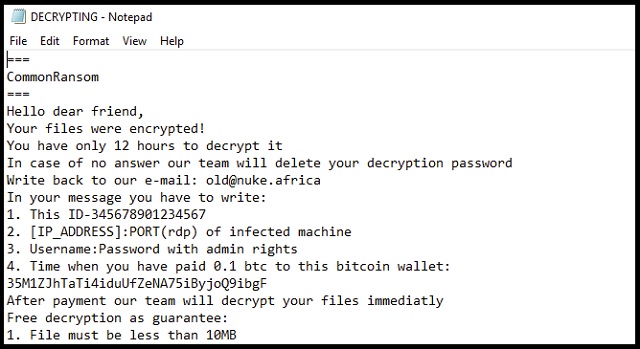
===
CommonRansom
===
Hello dear friend,
Your files were encrypted!
You have only 12 hours to decrypt it
In case of no answer our team will delete your decryption password
Write back to our e-mail: old@nuke.africa
In your message you have to write:
1. This ID-345678901234567
2. [IP_ADDRESS]:PORT(rdp) of infected machine
3. Username:Password with admin rights
4. Time when you have paid 0.1 btc to this bitcoin wallet:
35M1ZJhTaTi4iduUfZeNA75iByjoQ9ibgF
After payment our team will decrypt your files immediatly
Free decryption as guarantee:
1. File must be less than 10MB
2. Only .txt or .lnk files, no databases
3. Only 5 files
How to obtain bitcoin:
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Commonransom is a destructive ransomware virus that locks your files. It sneaks into your computer and corrupts everything. The virus targets your files, but to get them, it infects your entire system. The ransomware modifies the Registry, corrupts essential directories, drops files, and starts malicious processes. This, of course, happens in complete silence. Without any noticeable symptoms, the virus spreads its roots around your entire OS. Once it gets your system under control, the virus starts a scan. It is after the user-generated files. It locates your pictures, database, music, videos, documents and encrypts them. Commonransom Ransomware uses advanced encryption algorithms to lock your files. You can recognize the corrupted files by the .[old@nuke.africa].CommonRansom file extension. The ransomware adds it at the end of the corrupted files (thus, if you have a file named “example.txt,” the ransomware would rename it to “example.txt.[old@nuke.africa].CommonRansom”). When the encryption process is complete, the ransomware drops its ransom note. It briefly explains the situation and lists the hackers’ demands. The threat actors want 0.1 Bitcoin (approximately $645USD) paid within 12 hours. Do not panic! The time limit is a classic psychological trick. The hackers want you to act impulsively. They want you to jump into conclusions and make wrong decisions. Do not make their job easier. Do not follow their instructions. You are dealing with criminals. Do not fall for their lies.
How did I get infected with?
Commonransom Ransomware infects your device through trickery. The parasite lurks in the shadows and waits for you to let your guard down. All it needs to succeed is one moment of carelessness. Do not give it a chance to strike. No anti-virus app can protect you if you act recklessly. Only your caution can keep your device secure and virus-free. Viruses like Commonransom Ransomware are usually distributed through spam campaigns. That’s right! The good old spam emails are still the number one cause of virus infections. The emails, however, are not what they used to be. The scheme is different. The hackers attach safe documents. They lure you into downloading them. You, however, know better than to open mysterious files, so you scan the downloads. The files seem clean, so open them. At this point, you would be asked to enable the “Editing” mode of your file-editor. If you click on the “Accept” button, a script would download the virus. Only your caution can prevent this scenario from unfolding. Treat all unexpected messages as potential threats. Do not open them even if they are from well-known organizations. Verify their senders first. Thus, if you receive an unexpected email from your bank, for example, visit their official website. Compare the email addresses listed there to the questionable one. If they don’t match, delete the pretender!

Why is Commonransom dangerous?
Commonransom Ransomware corrupts various types of files: pictures, documents, databases, etc.. The virus wrecks your system and threatens to destroy your precious files if you don’t pay. Do not swing into action, though. You are dealing with a nasty virus. Its owners are not better. They promise a decryption key that is supposed to restore your files. There, however, are many cases where the victims paid and received nothing in return. Once they get what they want, the hackers are very likely to ignore you. But they may also try to get you to pay more. Also, bear in mind that the file-decryption process restores your file, but it doesn’t remove the virus. What will you do if Commonransom Ransomware re-locks your files? How many times are you willing to pay? Do not play games with criminals. To get your decryption key, you are supposed to contact these hackers via email. Do you think that’s a good idea? Don’t give these people a way to contact you. You’ll only prove yourself an easy target. The hackers may attempt to cause you more harm by hacking your email, for example. Do not risk it! Do not test your luck. Your best course of action is the immediate removal of the ransomware. Do not waste time in debates. Delete Commonransom Ransomware ASAP!
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Commonransom Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Commonransom Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Commonransom encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Commonransom encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.