Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Clouded Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
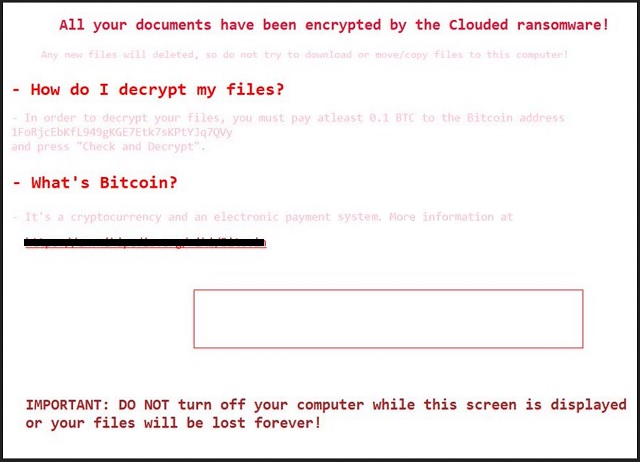
All your documents have been encrypted by the Clouded ransomware!
Any new files will deleted, so do not try to download or move/copy files to this computer!
– How do I decrypt my files?
– In order to decrypt your files, you must pay atleast 0.1 BTC to the Bitcoin address
1FoRjcEbKfL949gKGE7Etk7sKPtYJq7QVy and press “Check and Decrypt”.
– What’s Bitcoin?
– It’s a cryptocurrency and an electronic payment system. More information at
https://en.wikipedia.org/wiki/Bitcoin
Check and Decrypt
IMPORTANT: DO NOT turn off your computer while this screen is displayed or your files will be lost forever!
Cloudy days are coming if you have to deal with the Clouded Ransomware. This piece of software has managed to sneak into your computer and is now holding your files as hostages. Clouded is based on an open source ransomware project named HiddenTear. There are many ransomware viruses based on this project. All of them are proven to be efficient and deadly. Clouded was discovered quite recently. It has managed to infect PC users mainly in North America. The ransomware targets the users’ most precious files. Their documents, pictures, and videos. However, it can encrypt over ninety types of files, including .zip, .docx, .html, .pdf, .mp4, .jpeg, etc. Clouded ads the “.cloud” extension to the name of the encrypted files. Thus, if you have a file named example.txt, the ransomware will rename it to example.txt.cloud. You will be able to see the icons of your files, however, you won’t be able to open or use them. Once all your files are successfully encrypted, the virus will drop a ransom note. The note states that all your files will be “forever” lost if you turn off your machine. It also reads that you can’t create new files. If you do, they will be deleted. Basically, this virus makes your computer useless. Be rational. The crooks are trying to scare you. They need you to act impulsively. Consider the situation. You must remove this threat as soon as possible.
How did I get infected with?
Clouded, just like most ransomware viruses, relies on spam email campaigns to travel the internet. The hackers would add a malicious script to a document. Then, they would attach this file to an email and hope for you to be careless. Once you downloaded such a corrupted file, it will download and install the Clouded ransomware. All this will happen in the background. You will not notice those processes. Your computer may become a bit more sluggish, but nothing more. The virus is designed to be stealthy. It runs as couded.exe process which you can see in your Task Manager. If you stop this process on time, there is a chance to save some of your precious files. However, if you have seen the ransom note, it is already too late. Clouded has encrypted all target files on your PC. Spam emails are not the only way Clouded uses to travel the Internet. It can also be distributed via file-sharing networks, corrupted links, and freeware apps. Be vigilant! The Internet is bursting with parasites. If you think that something is wrong, there probably is a good reason for that. Avoid suspicious websites, advertisements, and applications. And don’t forget your anti-virus software. Keep it up to date.
Why is Clouded dangerous?
Clouded locked your files. It now demands an enormous sum of money to decrypt them. In exchange for 0.1 Bitcoins (about 182 USD), the crooks will send you a decryption key. Don’t do it. Don’t sponsor those people. First of all, they will use the money to further develop their virus. Second, there is no guarantee that they will send you a working key, if they send you anything at all. Those people have penetrated your computer’s security and locked your files. They want money to restore your personal pictures and documents. Do they seem like fair people to you? You can’t win a game against cyber criminals. You will only lose money and time. Besides, maybe there is a chance to restore your files without paying the ransom. If you have system backups, you can use them. However, before you take any action, remove the infection! Otherwise, your newly restored files will be encrypted too. Be rational. Consider your options. Even if you decide to pay the ransom, you must remove this virus. The decryption tool will only restore your files. It will not delete the ransomware. There are cases where the victims paid and restored their files just to have them re-encrypted hours later. Therefore, we recommend against any dealings with the hackers. Consider discarding your data.
Clouded Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Clouded Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Clouded encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Clouded encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



