Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Cerber 5 Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
Attention. Attention. Attention. Your documents, photos, databases and other important files have been encrypted!
Cerber is a ransomware infection that just refuses to go away. New versions of the original program keep popping up. And, Cerber 5 is the newest. It still follows the same programming. Invade. Corrupt. Extort. The tool is your standard ransomware infection. It finds a way to slither into your system undetected. And, once it does, takes over. The application spreads its clutches throughout, and your data gets locked. Oh, yes. Cerber 5 targets each file you keep on your computer, and encrypts it. Pictures, videos, music, documents, everything falls. The tool adds a special extension at the end of each file, which further solidifies its hold. And, once that happens, you can no longer access your data. Moving or renaming them does nothing. The only way to free them is with a decryption key. And, you’ve guessed it. To get it, you have to pay up. But there are so many things that can, and will, go wrong with the exchange. That’s why experts advise against payment. Yes, do NOT pay. Do NOT comply! The people behind the infection WILL double-cross you! They’re cyber criminals, who cannot be trusted to keep their word. To follow their demands is to bury yourself deeper in troubles. So, don’t. It may be difficult to forsake your files, but it’s the right thing to do. Say goodbye to your data, so you don’t have to say goodbye to your privacy. Make the smart choice.
How did I get infected with?
Like most cyber threats, Cerber 5 tricked you into installing it yourself. The tool turned to the old but gold means of infiltration to sneak in undetected. Yes, undetected. Because, even though, they get you to approve them in, they keep you oblivious to it. How? Well, as was stated already, they trick you. Ransomware applications have an array of methods to use for that sole purpose of fooling you. They can hide behind spam email attachments or corrupted links. They can pretend to be a false system or program update. Like, Java or Adobe Flash Player. But the most common means of deception is freeware. For reasons unknown, web users throw caution to the wind when going through its install. Instead of reading the terms and conditions, they just agree to everything in haste. That’s a strategy that gets you stuck with infections. Don’t give into distraction and haste. Don’t be careless. And, instead of hoping for the best, and leaving your fate to chance, do your due diligence. Attention goes a long way. Remember that next time you’re installing a tool or an update.
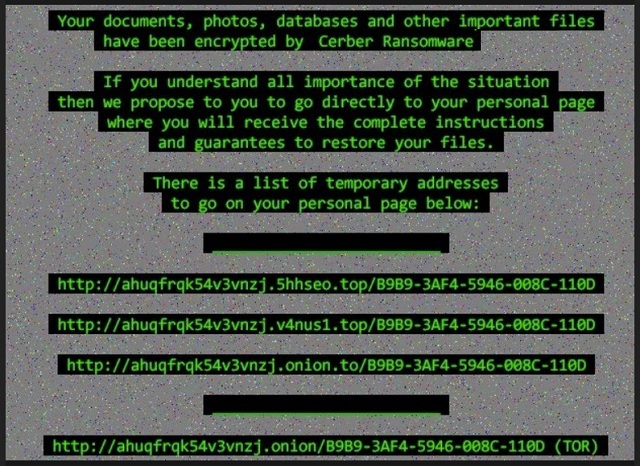
Why is Cerber 5 dangerous?
As was already mentioned, Cerber 5 is a newer version of the same old threat. It follows the standard ransomware programming. After is sneaks into your system, it gets to work. The tool doesn’t waste time, and quickly encrypts everything. By using the AES encryption process, it locks all the files you have stored on your PC. And, make no mistake. Once Cerber 5 finishes, your files become inaccessible. It leaves you a ransom note with explanation and instructions. It’s a README.TXT or README.hta file on your Desktop, as well as in each encrypted folder. The tool also changes your Desktop picture to display its note. Its demands haven’t changed. The ransomware asks for a ransom payment of 0.6967 Bitcoins. That’s about $500, which is no small amount. But, here’s the thing. Even if the infection demanded you pay a single dollar, you still shouldn’t pay. And, here’s why. If you go through with the payment, what do you do? You give your personal and financial information. And, the cyber criminals behind Cerber 5 can access it. You’ll give extortionists access to your private life. Name a single scenario where that ends well for you. Don’t be naive. There isn’t one. Think of the consequences of paying the ransom. There are several possible outcomes. One, you get the decryption key and free your files. But, then what? The key does not get rid of the infection, just the encryption. So, Cerber 5 will remain. And, what’s to stop it from locking your data once more? Nothing. There are NO guarantees you won’t be back to square one even the next day. Other possible outcomes include you NOT receiving a key at all, or getting one that doesn’t work. Understand that the battle against a ransomware cannot be won. You can just cut your losses. So, cut your losses, and say goodbye to your data. Files are replaceable. Privacy is not.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Cerber 5 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Cerber 5 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Cerber 5 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Cerber 5 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



