Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Redboot Ransomware?
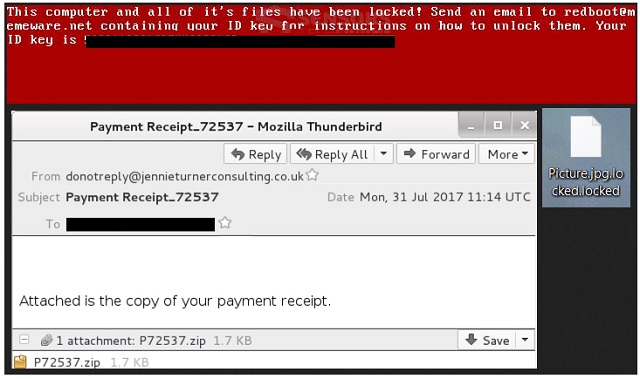
Readers recently started to report the following message being displayed when they boot their computer:
“This computer and all of it’s files have been locked! Send an email to redboot@memeware.net containing your ID key for instructions on how to unlock them. Your ID key is {Unique Victim ID}”
Today we’re focusing on the Redboot infection. Despite being one of the newest cyber threats out there, it has already caused many people a headache. This is ransomware. However, researchers warn that Redboot shows signs of a wiper too. Not only does the virus encrypt your personal files and hold them hostage. It also modifies the Master Boot Record (MBR) so you may never regain access to your locked data. Even though Redboot is indeed a very frustrating program, you have to remain calm. Panicking would only make matters worse and might cost you money. Ransomware is nothing but a clever attempt for hackers to blackmail you. Thus, the Redboot virus is aiming solely at your bank account. This pest uses a strong encrypting algorithm and locks your files. Yes, all your files. Pictures, music, videos, presentations, various documents. Ransomware-type infections pose a threat to all your private data. Redboot is no exception. It renames the target files and adds the .locked extension to them. For instance, Despacito.mp3 gets renames to Despacito.mp3.locked. Once you see this extension, it’s game over. Your favorite and probably important data is no longer accessible. You can’t view or use any of the files stored on your machine. Your very own files on your very own computer. If that seems unfair, wait till you hear the rest of it. Redboot encrypts your files out of the blue. By doing so, the parasite attempts to scare you into paying a certain sum of money. As mentioned, this whole thing revolves around the illegal profit hackers try to gain. To achieve their goal, crooks are more than willing to lock your precious files. The problem is, hackers have no intentions to set your data free. Redboot Ransomware drops some detailed payment instructions. According to these ransom notes, unlocking your files without a decryptor is impossible. Conveniently enough, hackers promise a decryption key in exchange for a ransom. They rely on the fact you’d desperately want your data back so be careful. Trusting the parasite’s ransom messages is how you get scammed.
How did I get infected with?
File-encrypting parasites usually travel the Web via fake emails. Thus, next time you receive something in your inbox you find untrustworthy, delete it. Remember that it only takes a single moment of negligence to infect your computer system. On the other hand, removing malware could take many long, long hours. Make an effort to protect your safety and you’ll see that is worth it. Delete the random email-attachments and messages you receive. Viruses might pretend to be job applications or other legitimate-looking documents. Keep in mind that spam emails from unknown senders are normally corrupted. Watch out for potential intruders next time you surf the Web. Pay attention so you don’t have to deal with ransomware again. Also, many infections get spread online via bogus torrents or software updates. They might use some help from other parasites too. More often than not, that help comes from a Trojan horse which is another destructive type of parasite. Check out your machine to make sure there are no additional infections.
Why is Redboot dangerous?
PC users rightfully fear ransomware. This is the kind of infection that causes sudden, sometimes irreversible harm. It goes without saying that nobody wants to have their files encrypted. If you keep backups of your most important data, ransomware can’t harass you. Thus, always make sure you have backup copies. The Internet is filled with various file-encrypting parasites so don’t underestimate the threat. Instead, be cautious online. Redboot Ransomware denies you access to your information. It renames your files and then attempts to involve you in a fraud. If you panic, you may allow cyber criminals to steal your Bitcoins. That means you have to constantly keep in mind Redboot is deceptive. Paying the sum crooks demand isn’t a solution and you know it. In the worst case scenario, your files will remain locked AND your money will be gone. Hackers are certainly not the right people to make negotiations with. Forget about the decryptor crooks promise and don’t let them scam you. Ignore the redboot@memeware.net email address too. To delete Redboot, please follow our detailed manual removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Redboot Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Redboot Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Redboot encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Redboot encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



