Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Payday Ransomware?
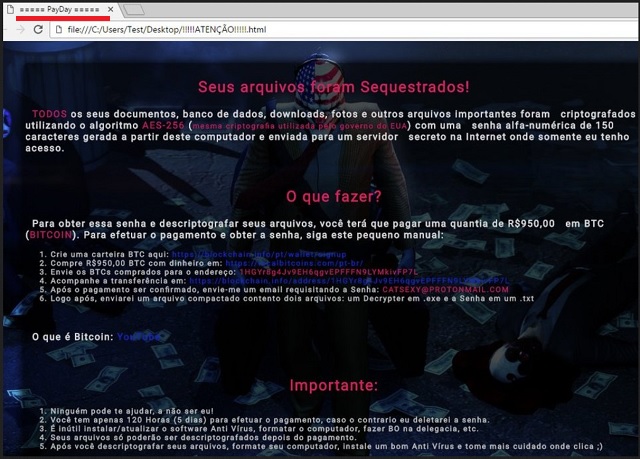
Readers recently started to report the following message being displayed when they boot their computer:
Your files have been hijacked!
ALL of your documents, database, downloads, photos, and other important files were encrypted using the AES algorithm (same encryption used by the US government) with a 150 character alpha-numeric password generated from this computer and sent to a server Secret on the Internet where only I have access.
What to do?
To get this password and decrypt your files, you will have to pay an amount of $ 950.00 in BTC (BITCOIN). To make the payment and obtain the password, follow this small manual:
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
1. Create a BTC portfolio here: *** blockchain.info/***
2. Buy R $ 950,00 BTC with money in: ***
3. Send the purchased BTCs to the address: *****
4. Follow the transfer on: *** blockchain.info/address/***
5. After payment is confirmed, send me an email requesting the Password: CATSEXY@PROTONMAIL.COM
6. Soon after, I will send a compressed file containing two files: a decrypter in .exe and the Password in a .txt
What is Bitcoin:
Important:
1. No one can help you but me!
2. You only have 120 Hours (5 days) to make the payment, otherwise I will delete the password.
3. It is useless to install / update the AntiVirus software, format the computer, do BO in the police station, etc.
4. Your files can only be decrypted after payment.
5. After you decrypt your files, format your computer, install a good AntiVirus and be more careful where you click;)
Ransomware parasites are deadly. They enter your computer unnoticed and before you know it, they wreak havoc on it. The newest member of their malicious family is a virus named .Payday Ransomware. This pest works in the shadows. It won’t betray its cover, not until it’s too late. Luckily, we can help you deal with this pest. But first, let’s take a moment to explain how this parasite works. Upon installation, the Payday Ransomware scans your HDD for target files. It is after user-generated files, such as your pictures, videos, documents, databases, archives, and music. The virus locks such files with a strong AES encryption algorithm. Once the encryption process is finished, you will be able to see the icons of your files, you won’t be able to open or use them. You can recognize an encrypted file by its extension. Payday adds the .sexy suffix at the end of all encrypted files. Thus, if you have a document named example.odt, the virus will rename it to example.odt.sexy. When all target files are successfully locked, the ransomware drops its ransom note at the victim’s desktop. It is a simple HTML file named !!!!!ATENÇÃO!!!!!.html. The note is written in Portuguese. It contains a brief explanation of what had happened you your files and that you should pay in order to restore them. Payday demands R$950 in Bitcoins (about $300 USD). In case you have questions, the hackers have proved an email address (CatSexy@protonmail.com.) We recommend against contacting the crooks. These people are criminals. They know what to say in order to trick you into paying. Don’t rush Take a moment to consider the situation. You should not pay! There is no need to. You can use file backups to restore your files for free. Be advised, though. Your first step should be the removal of the virus. Otherwise, it will re-encrypt your newly restored files. For detailed instructions, scroll down to our step-by-step manual removal guide. You can also use a trustworthy anti-virus app to clean your computer for you.
How did I get infected with?
To reach its victims, Payday Ransomware relies on spam email attachments. The scheme is simple, yet, brilliant. The crooks write on behalf of well-known organizations, companies, banks, post offices, police departments, etc. They will attach malicious files to their letters. Once you opened these attachments, a malicious code executes. It downloads the ransomware payload file from a remote server and installs it. Only your caution can keep your PC clean. When you receive a message from a stranger, verify the sender’s contacts. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone must have complained. Even if you cannot find any evidence online, don’t let your guard down. Look for suspicious signs. Reliable companies would use your real name to address you. If you receive a letter starting with “Dear Customer,” or “Dear Friend,” proceed with caution. Don’t follow any links. They can be corrupted too. If the sender writes on behalf of some company, go to their official website. Compare the email address there with the one you have received a message from. If they don’t match, delete the pretender immediately. The Internet is a dangerous place. You can never know where an infection might strike you from. Having a powerful anti-virus on board is a must nowadays.
Why is Payday dangerous?
The Payday Ransomware is a menace. It sneaked into your machine and locked your files. The ransomware promises a recovery tool in exchange for a hefty ransom. Yet, these are false promises. You are dealing with criminals. They will not keep their part of the deal. It is not unheard-of victims who paid but got nothing in return. You should get rid of the virus fast. With Payday running loose on your PC, you cannot get any work done. If you create new files, the virus will lock them. You cannot even shop online. If you do, your usernames, passwords, credit card details and other paying information will get recorded by the virus. What you should do is to remove the parasite immediately. As this virus is quite sophisticated, we recommend you to use a powerful anti-virus app. Of course, you can try to delete it manually, we have proved a detailed removal guide down below!
Payday Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Payday Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Payday encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Payday encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



