Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove “Oops your files have been encrypted” Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
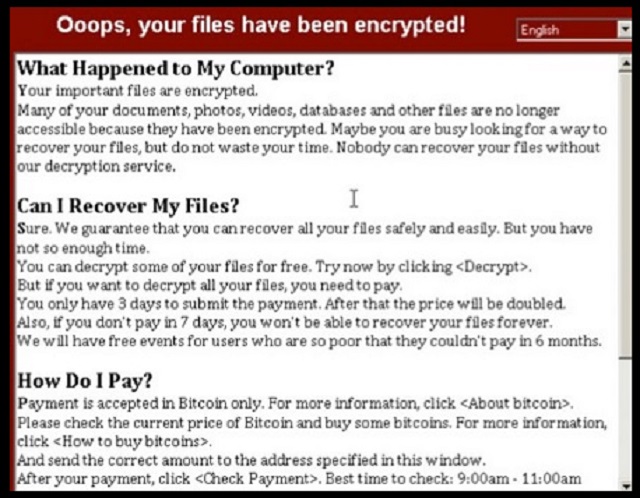
Ooops, your important files are encrypted.
If you see this text, but don’t see the ”Wana Decrypt0r” window,
then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files you have to run the decrypt software.
Please find an application file named “@WanaDecryptor@.exe” in any folder or restore from the antivirus quarantine.
Run and follow the instructions!
“Oops your files have been encrypted” reads the ransom note of the newest cryptovirus. This ransomware is a pest that can turn your computer into a useless machine. You can use your PC to browse the Internet, but that is all. You can’t save anything on it because the cryptovirus will lock it. All your personal files are still on your machine. Yet, you cannot open or use them. You are not alone. This virus is spreading like fire. Worldwide, there are thousands of infected computers. It has been reported that the Russian Ministry of Interior Affairs, as well as, a number of airports have fallen victims to this ransomware. The threat is real. “Oops your files have been encrypted” uses strong encrypting algorithms. There are no description tools. This parasite can modify your system registry. It can add or delete entries in it. Which means one thing, the virus will load together with your OS. The cypovirus also deletes the shadow copies of your system, which complicates the file recovery. Otherwise, “Oops your files have been encrypted” works as a typical ransomware. It enters your computer unnoticed, scans your HDD for target files and encrypts them. All this will happen behind your back. Only after the encryption process is complete, will the virus notify you about its presence. It will drop a ransom note that explains what had happened to your files. Don’t panic. The note will present the information in a way that will make you act impulsively. Be rational. Take a minute to consider your options.
How did I get infected with?
“Oops your files have been encrypted” is using the good old spam emails to travel the web. Nowadays, it is hard to tell which emails are spam, and which are legit. Scammers tend to write on behalf of well-known organizations. They will not hesitate to steal logos and fabricate stamps. Their only goal is to lure you into downloading a corrupted document. Be vigilant! The crooks will disguise the virus as something irresistible. Invoices, job applications, tickets, or something entirely different. The attachment is not the only thing that can be corrupted. The email itself may contain malicious links. Don’t click on any. Before you open an email from a stranger, check the sender’s contacts. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone must have complained online. Unfortunately, this method is not flawless. You are responsible for your computer’s security, therefore, double check the address. If the letter is from an organization, for example, visit their official website. You can find their authorized email dresses there. Compare them with the once you have received a letter from. If they don’t match, you know what to do. Delete the spam message immediately. The “Oops your files have been encrypted” ransomware could have arrived via torrents, corrupted links or fake software updates. The hackers are quite imaginative. Yet, to enter your computer, they rely on your negligence. You can spare yourself many problems if you are vigilant. Download software from reliable websites only. And when you are installing software, use the advanced installation wizard. Last but not least, read the terms and conditions.
Why is “Oops your files have been encrypted” dangerous?
The “Oops your files have been encrypted” is holding your files as hostages. It gives you limited time to pay an enormous amount of money as a ransom. It forces you to pay for your own files. This is extremely obnoxious. Don’t negotiate with the hackers behind this virus. They are criminals. You can’t expect them to play fair. They will double-cross you. First of all, they may not send you the decryption tools. Second, if they contact you, the decryptor may not function properly. And, of course, the virus on your computer can be programmed to spy on you. When you use your credit card to pay the ransom, the virus can record your payment credentials. You wouldn’t wish the hackers to have such information about you, will you? We are talking about real criminals here. Use a trustworthy anti-virus program and clean your machine. The sooner, the better.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
“Oops your files have been encrypted” Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover “Oops your files have been encrypted” Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with “Oops your files have been encrypted” encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate “Oops your files have been encrypted” encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



