Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Onyon Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
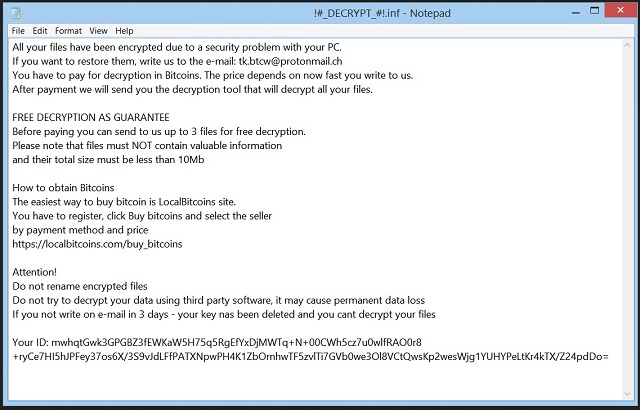
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: tk.btcw@protonmail.ch
You have to pay for decryption in Bitcoins. The price depends on now fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 10Mb
How to obtain Bitcoins
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 3 days – your key nas been deleted and you cant decrypt your files
It seems hackers do want to see their victims in tears. The WannaCry Ransomware is already spreading across Europe; now we’re about to tackle the Onyon Ransomware. This malicious program is actually a new version of the BTCWare Ransomware. As you probably know, the Internet is infested with file-encrypting viruses. These aggravating infections are aiming at your bank account so they are incredibly dangerous and problematic. What you’re stuck with is a classic member of the troublesome ransomware family. Luckily, most infections of the kind follow one pattern so at least you can’t expect originality out of Onyon Ransomware. You can (and should) expect it to be destructive, though. As soon as your computer gets infected, the ransomware initiates a scan. Once this task is complete, you could wave your private files goodbye. File-encrypting infections attack your personal data in order to wreak havoc. Do you store important files on your machine? If you do, it’s recommended that you also have backup copies of your data. Remember, ransomware is on the rise right now. You could save yourself the trouble in the future by protecting your files in advance. The Onyon Ransomware locates all your private information. That includes music, photos, videos, documents. This pest works with some of the most commonly used formats so imagine the damage it’s capable of. By using a strong encrypting algorithm, Onyon Ransomware locks your files. All your files. Just to make matters worse, the virus encrypts your data in silence. There are little to no signs that a ransomware has been downloaded while it’s locking data. However, pay attention to the PC speed. If your device starts crashing or freezing all of a sudden, you might be dealing with ransomware. How can you tell whether your files have been encrypted? You’ll notice a brand new appendix – the .Onyon file extension. For instance, Summer_2016.mp4 gets renamed to Summer_2016.mp4.onyon. That goes for all your private files stored on the computer. Anything that has the .Onyon extension is inaccessible and unreadable. And that is just the first step of the parasite’s trickery. You will also notice this program’s ransom notes. After Onyon Ransomware has encrypted your data, it drops the “!#_DECRYPT_#!.inf” files. These get added to every single folder that contains encrypted information. As you could imagine, those are indeed a lot of folders. Keep in mind that you’re currently involved in a nasty attempt for a scam and you must be very careful.
How did I get infected with?
One notoriously famous technique involves fake emails. This method allows hackers to spread all kinds of infections online. Next time you receive some suspicious-looking email, delete it on the spot. Clicking open a corrupted email-attachment or message may let loose a virus. Or better yet, a whole bunch of viruses. As mentioned, Onyon Ransomware is a secretive parasite so it relies on your haste and distraction. The virus might pretend to be a job application or some other perfectly safe email. Watch out for potential intruders instead of accidentally installing malware. Also, stay away from illegitimate websites, third-party pop-ups and random torrents or program updates. It’s always better to be safe than sorry so don’t rush. Take your time online to make sure your computer remains virus-free. Ransomware could use some help from a Trojan horse as well. That means you have to check out your device to see if Onyon Ransomware is having some malicious company. It is entirely your job to prevent malware infiltration so be cautious.
Why is Onyon dangerous?
The virus encrypts your precious files and makes them unusable. In addition to that, it tries to manipulate you into paying a ransom. Unless you’re willing to give your money for nothing, you will keep your Bitcoins. In the parasite’s ransom notes you can read that “after payment we will send you the decryption tool that will decrypt all your files.” That is too good to be true, don’t you think? You would be making a deal with cyber criminals who, to put it mildly, aren’t the most honorable people. Ransomware is just a clever way for crooks to blackmail innocent PC users so don’t even consider giving your money away. You may not receive the decryptor promised and your files could remain locked. Instead of allowing hackers to involve you in their fraud, get rid of the parasite. Ignore its empty promises and bogus threats. Onyon Ransomware must be removed ASAP. To do so manually, please follow our detailed removal guide down below.
Onyon Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Onyon Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Onyon encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Onyon encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



