Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RSA-2048 Ransomware?
RSA-2048 is a particularly strong encrypting algorithm. It’s associated with ransomware- possibly the most destructive type of PC parasite you could stumble across online. We’ve taken numerous opportunities to write removal guides about ransomware programs that use the RSA-2048 algorithm. The list includes CryptoWall 3.0, CryptoLocker, KEY Holder and many more similar infections. Therefore, your computer has been recently compromised and one of these viruses is lurking somewhere on your machine. Quite a nasty situation, isn’t it? We should probably let you know that it only gets worse from here. Once the ransomware virus manages to get installed, it scans your machine searching for personal files with specific extensions to encrypt. Another trick the parasite may perform is to block your entire machine this locking you out completely. As you can clearly see, there is a reason why ransomware infections are something that has to be avoided. These parasites are immensely resourceful and impressively harmful. After the scan is complete, the virus usually infects a huge percentage of your private files including music, personal pictures, videos, documents, presentations and other probably quite valuable files you have stored on the device. Then, thanks to the RSA-2048 algorithm, the virus encrypts all of your private information and locks it. From this moment on there is no accessing your own data. Thanks to the encryption, your files change format and your PC cannot read the current one. That means most of your files are now absolutely inaccessible and useless. If you thought THAT was aggravating and unfair, wait till you hear the next part of the scheme. The virus starts generating some highly irritating ransom note. According to this message, in order to regain access to your data, you have to pay a certain sum of money. And it’s usually not a small one. You see where this is going, don’t you? The sole purpose of these infections is to blackmail you which explains why hackers are so interested in developing ransomware. If you have all your important files encrypted or your very own computer locked, chances are, you might panic and follow crooks’ instructions. That is precisely what they want and that is the very last thing you should do. Yes, you are in a vulnerable position but playing by the rules hackers invented might only make things worse. Remember that paying the ransom doesn’t guarantee you anything. Would you like to become a sponsor of greedy cyber criminals?
How did I get infected with?
At the end of the day, PC infections are still computer programs which means they have to be properly installed. Same thing goes for ransomware viruses. No one in their right mind would install such a vicious piece of malware voluntarily so how did you end up infected? Well, most parasites are very sneaky. They usually travel the Web in complete silence so you might remain oblivious to the installation for quite a long time. One of the few things worse than having your PC compromised is having your PC compromised without knowing it. To prevent such an unpleasant scenario in the future, be cautious online. Stay away from the random spam messages or spam email-attachments you might come across. Restrain yourself from clicking third-party commercials and avoid unverified websites. Also, you should keep in mind how dangerous freeware/shareware bundles might be because this is one of the most popular distribution techniques at the moment. Always take your time when installing such bundles. Otherwise, you might accidentally install a whole bunch of infections (including ransomware) alongside the safe programs you were originally going for. Don’t jeopardize your own safety and don’t allow hackers to fool you.

Why is RSA-2048 dangerous?
As previously mentioned, the RSA-2048 encrypting algorithm creates quite a mess. All ransomware programs that use it pose an immense threat for your safety and need to be immediately tackled. However, what you have to remember till you remove the parasite is to ignore the messages it bombards you with. Why would you trust a program that was originally supposed to scam you? Cyber criminals take advantage of the fact many people would panic seeing their entire machine locked or most of their personal files encrypted. It goes without saying that you can’t let hackers mess with you because even if you do pay the ransom, you might gain absolutely nothing. No decryption key, no solution for your problems. Nothing. Is paying the money really a risk worth taking? Our advice for you is to remain calm and collected despite hackers’ tireless attempts to involve you in their frauds. Instead of falling victim to their shenanigans, get rid of the virus and make sure you never have to deal with ransomware again. To delete it manually, please follow the detailed removal guide that you will find down below.
RSA-2048 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

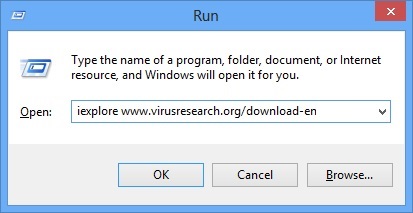
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove RSA-2048 Manually
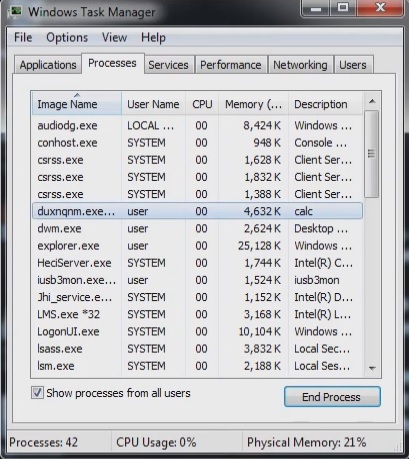
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.