Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove DilmaLocker Ransomware?
Readers recently started to report a message being displayed when they boot their computer. It’s a translation from the original Portuguese text, and it reads:
* * * ATTENTION * * *
All your files have been encrypted by the Dilma Locker virus
Be calm, we have a solution
The cost to decrypt your files is $ 3000.00 (three thousand reais)
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can not afford it? Take it easy, let’s negotiate, we just want to help you;)
You have the right to decrypt a file for free. Choose one and send us by email (up to 3mb).
Payment is only accepted in bitcoin. Do not know how to use it? We will teach you!
All of your most important files were encrypted using the 256-bit AES algorithm.
Same encryption used by the US government to protect state secrets.
That’s right, it is IMPOSSIBLE to recover your files without the correct password.
If you are interested in obtaining this password and recovering your files, please send an email to dilmaonion@keemail.me
containing the dilminha.dat file that was created on your desktop (it’s your personal identifier, do not miss it).
There is no other way to recover your files without our help, any program or anti-virus that you use will corrupt your files and you will lose them forever.
Once you send us the payment, we will send you the password and the program that will decrypt.
Want some guarantee? Send us any encrypted file and we will decrypt and return it for free.
But walk away, in 4 days your files will be deleted and you will never recover them again.
Looking forward to seeing you ?
I live from computer crime because I do not have so many options to live with dignity within the system.
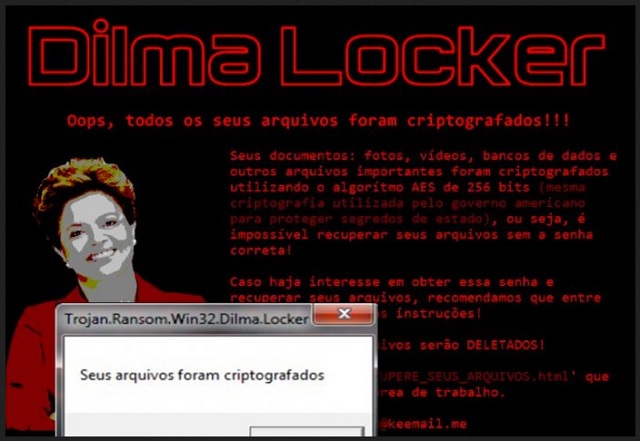
It seems DilmaLocker was inspired by the ex-president of Brazil Dilma Rousseff. However, we have established long ago that hackers know no boundaries when it comes to ransomware. The DilmaLocker virus belongs to perhaps the most dangerous family of parasites. There is a reason why PC users absolutely dread ransomware programs. These infections are a perfect combination of stealthy, aggressive and harmful. Being a classic ransomware program, DilmaLocker works the same way. It uses the AES-256 encrypting algorithm to lock all your files. Yes, every bit of information you’ve stored on your own computer gets encrypted. Do you see why nobody wants to cross paths with ransomware? DilmaLocker takes down your photos, videos, presentations, music files, documents. It gets activated immediately after the installation process is complete. Note that the installation itself happens without your knowledge. Ransomware uses some particularly secretive methods to get downloaded. Once it lands on board, the parasite scans your machine in order to find your files. As mentioned, ransomware targets all your file formats. There’s no escaping its shenanigans because your private data falls victim to the virus. Do you keep important information on your device? You should definitely think about having backup copies as well. In the future, make sure you protect your files in advance. If you have backups, it’s safe to say ransomware can’t cause you any harm. It would still cause you a headache, though. The DilmaLocker parasite uses a complicated cipher to lock your data. Before you know it, this program effectively renames all your files. It adds the “._dilmaV1” extension to the target files. That’s how you can tell your information is no longer readable. For instance, “16th Birthday.mp4” gets renamed to “16th Birthday.mp4._dilmaV1”. This file, along with all the others you have on board, is now locked. Its format gets altered so your computer won’t be able to recognize the new one. And, voila, you won’t be able to open or use your data in any way. Ransomware makes sure you notice its presence. Furthermore, it is attempting to get you to panic. As you could imagine, many people would get quite worried seeing their files get encrypted out of the blue. Giving into your anxiety is never a good move, though. DilmaLocker drops “RECUPERE_SEUS_ARQUIVOS.html”, “background.bmp” and “dilminha.dat” on your desktop. If you thought locking your files was bad enough, wait till you hear what’s about to follow.
How did I get infected with?
The parasite was most likely presented as a harmless message or email. Thus, you got tricked into clicking it open. We’d recommend that you delete the spam messages and email-attachments you receive. Opening those is often a mistake so be very careful. It is your job to prevent malware infiltration. Chances are, DilmaLocker was disguised as some job application or an email from some shipping company. Always keep an eye out for potential parasites unless you want to test out the limits of your luck. The Web is infested with dangerous programs so be cautious. Some seemingly harmless email could help a nasty ransomware infection get installed. Don’t let hackers fool you twice. The ransomware might have also used some help from a Trojan horse. In other words, DilmaLocker might be having malicious company on your device. Check out the computer for further threats. Other popular infiltration methods involve exploit kits, fake torrents, bogus software updates, third-party pop-ups. Stay away from illegitimate websites too. Make sure you only download programs you trust, especially if they are bundled.
Why is DilmaLocker dangerous?
The virus modifies your desktop wallpaper. It provides a ransom note which is entirely in Portuguese. You will also see a picture of Dilma Rousseff herself. Now, this is where the scam begins. According to the ransom notes, you have to make a payment. Crooks demand that you buy a certain decryption key to be able to free your files. The decryptor costs 3000 BRL and that equals over 970 dollars. Are you really willing to make negotiations with hackers? Those are the very people who took your personal files hostage. Giving them your Bitcoins means you’re falling right into their trap. Ransomware is aiming at scamming you. DilmaLocker encrypts your data so it could force you to buy a decryptor. However, there is no guarantee crooks would keep their end of the bargain. You might just get involved in a fraud and your files might remain unusable. To delete the ransomware, please follow our detailed removal guide down below.
DilmaLocker Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover DilmaLocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with DilmaLocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate DilmaLocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



