Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Crypt32@mail.ru Ransomware?
You’re dealing with one of the most dangerous types of parasites imaginable. Have you heard of ransomware? It’s that stealthy infection that encrypts your private files and demands a ransom. Ransomware programs are on the rise right now for numerous reasons. They offer hackers one quick and incredibly effective method to gain profit. Illegitimate, effortless profit. As you could imagine, ransomware infections are actually trying to blackmail you. The ransomware you’re stuck with is a typical member of its malicious kind. That means it overall follows the usual pattern. However, this is a pattern that has proved itself to be successful. Once the parasite gets installed, it performs a thorough scan on your machine. This way, it locates all your precious information. As you could imagine, the installation itself happens behind your back. Ransomware doesn’t ask for permission. After all, not many people would agree to download a vicious file-encrypting infection. You will learn more of its infiltration methods down below. Now, when the virus finds your files, encryption begins. This program utilizes a complicated algorithm. Eventually, it denies you access to all files stored on your machine. Yes, that includes your favorite, important, valuable data. That is what ransomware is aiming at. Do you keep backups of your information? You definitely should. In the future, make sure you have copies of your files in order to prevent getting scammed. Think in advance. Ransomware-type parasites go after your files. Therefore, if you protect your files, such infections can’t cause you harm. The virus also renames the target data. That is how you can tell whether your information is accessible or not. If you notice a bizarre extension added to your files, that it is. It’s a crystal clear signal that the infection has locked your data. In addition, this program alters your desktop wallpaper and drops detailed payment instructions. You have to pay a certain sum of money in Bitcoin in order to free your data. The only problem is, you’d be making a deal with cyber criminals. They aren’t exactly the people you should trust with your money, are they? As mentioned already, crooks are attempting to scam you. Their ransomware infection is nothing but a cyber fraud. Stay away from the Crypt32@mail.ru email addresses hackers provide you.
How did I get infected with?
The most plausible explanation involves spam emails. Next time you receive some email or message from an unknown sender, delete it. If you click it open, you may be jeopardizing both your safety and privacy. It is your job to protect your PC from malware. Remember that hackers constantly work on new tricky, harmful infections. In addition, crooks work on new, original infiltration techniques. Ransomware gets spread online via exploit kits or third-party pop-up ads. You may have also installed some fake program update. Another popular method is called freeware or shareware bundling. When installing bundled software, always keep an eye out for infections. You may notice several dangerous parasites in only one seemingly safe bundle. Put your security first and don’t rush. Skipping installation steps is, to put it mildly, a risky move. Always take your time because prevention is a lot easier than deleting a virus. The ransomware could have also used some help from a Trojan horse. In this case, you should check out the machine for more viruses. This file-encrypting pest might be having company. As you can see, ransomware requires from you to be always attentive and cautious. Do not let such a destructive, deceptive program slither itself onto your device.
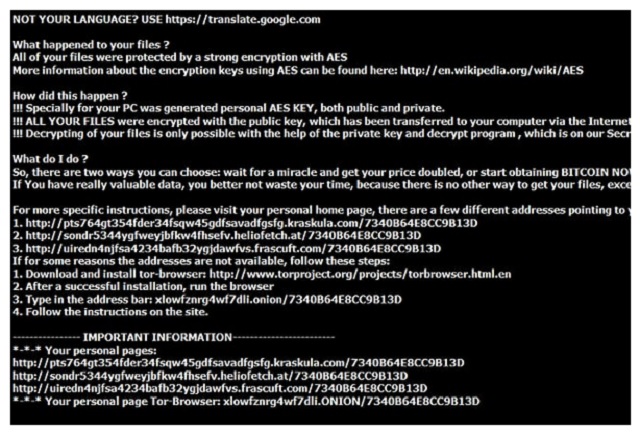
Why is Crypt32@mail.ru dangerous?
The virus is playing mind games with you. Many people would panic seeing their files get locked out of the blue. Thus, that’s how many people lose their money. Do not give into your despair or your anxiety. If you do, you fall straight into hackers’ trap. Keep your Bitcoins. Even if the parasite’s developers promise a decryption key, that’s a lie. Crooks were never interested in freeing your files. You could pay the entire ransom right away and receive nothing. That is because this program is focused on stealing your money. In order not to get scammed, keep your Bitcoins. Ignore hackers’ promises about a decryptor and get rid of the parasite. The sooner, the better. Please follow our manual removal guide down below.
Crypt32@mail.ru Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover Crypt32@mail.ru Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Crypt32@mail.ru encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Crypt32@mail.ru encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



