Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Revservice\Runrev64.exe Virus. The step by step removal works for every version of Microsoft Windows.
Revservice\Runrev64.exe falls under the Trojan umbrella. It is a nasty virus sneaks into your computer and corrupts everything. This nasty deceiver works in the shadows. Its infiltration process has no symptoms, so you cannot catch it in time to prevent the infection. The Trojan alters your system settings, modifies your Registry and starts malicious processes. At first, you won’t be bothered by its presence. You may not even detect it. The virus is programmed to install itself, to connect to a remote server and to wait for further infections. It can remain inactive for a while, but once it gets its commands, expect trouble. The Trojan interferes with every aspect of your day to day activities. It causes program failures, system crashes, slow and unstable Internet connection. The parasite is also behind the intrusive online ad-interference. The thing about Trojan Horses is that these parasites rarely come alone. They usually bring along a horde of parasites. Revservice\Runrev64.exe is very likely to infect your device with adware, spyware, and even ransomware. The most dangerous aspect of these viruses is their unpredictability. No one can tell you what the future holds. It all depends on the hackers and their current plans. Yet, one is known for sure: you will not like the outcome. Don’t wait to see what will happen. Act against the invader. The sooner you remove the Trojan, the better!
How did I get infected with?
Revservice\Runrev64.exe Trojan did not target your computer in particular. It didn’t hack you. No, the parasite was invited on your computer. You allowed this virus on board. Not unintentionally, of course. The Trojan knows how to trick you. The parasite stole your permission. It either lured you into clanking on a corrupted link, rededicated you to an infected website, or arrived hidden is a spam email. There are numerous virus distribution methods. Yet, they all have a common weakness. They will all fail if you are cautious and doubting. Let’s take the spam emails as an example. The good old spam messages are still the number one cause of virus infections. Yet, they are not what they used to be. The crooks no longer rely on malicious attachments. Nowadays, they tend to embed malicious links in their messages. They write on behalf of well-known organizations and trick their victims into clicking on malicious hyperlinks. One click is all it takes for a virus to be downloaded. Be cautious. Only you can prevent this scenario from unfolding. If you receive an unexpected message, from your bank, for example, go to their official website. Compare the email addresses listed there with the one you have received a message from. If they don’t match, delete the pretender immediately. Also, you can enter the questionable address into a search engine. If it was used for shady business, someone might have complained. Always choose caution over carelessness. It’s up to you to keep your device virus-free.
Why is this dangerous?
Revservice\Runrev64.exe is not to be underestimated. It jeopardizes both your privacy and security. This virus has unrestricted privileges and can manipulate your device. It can install/uninstall programs, add/remove registry entries, corrupt and delete files. The Trojan is a great weapon in its owners’ arsenal. What will happen to your device depends on these criminals and their current needs. If they want cyber-coins, for example, they may turn your machine into a miner. They may also infect it with ransomware and blackmail you. The hackers can also choose to infect your system with spyware and steal sensitive information about you. They may even destroy your OS for fun. You are in a very bad position. The Trojan may affect you terribly. It is an intruder that should not be tolerated. The more time it spends on your device, the bigger the chance it causes serious trouble. Don’t risk your privacy and security. Spare yourself many future headaches. Remove Revservice\Runrev64.exe Trojan the first chance you get.
Manual Revservice\Runrev64.exe Removal Instructions
The Revservice\Runrev64.exe infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Revservice\Runrev64.exe infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Track down Revservice\Runrev64.exe related processes in the computer memory
STEP 2: Locate Revservice\Runrev64.exe startup location
STEP 3: Delete Revservice\Runrev64.exe traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Revservice\Runrev64.exe related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Revservice\Runrev64.exe startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Revservice\Runrev64.exe virus from the windows registry
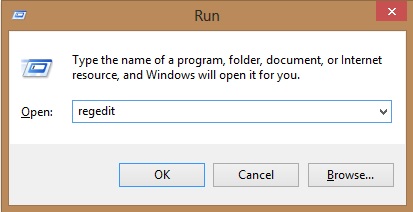
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
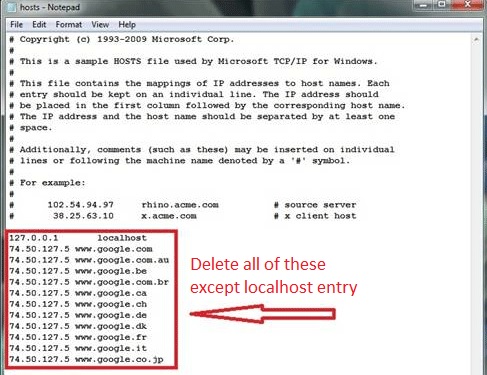
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Revservice\Runrev64.exe
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Revservice\Runrev64.exe, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Revservice\Runrev64.exe Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.